Vidar Spyware Abuses CHM File Formats to Evade Detection
Por um escritor misterioso
Last updated 11 abril 2025

Threat actors are hiding Vidar malware in Microsoft Compiled HTML files to avoid detection in email spam campaigns to target victims and harvest data. Know more!

Vidar Stealer Abuses Mastadon Social Network
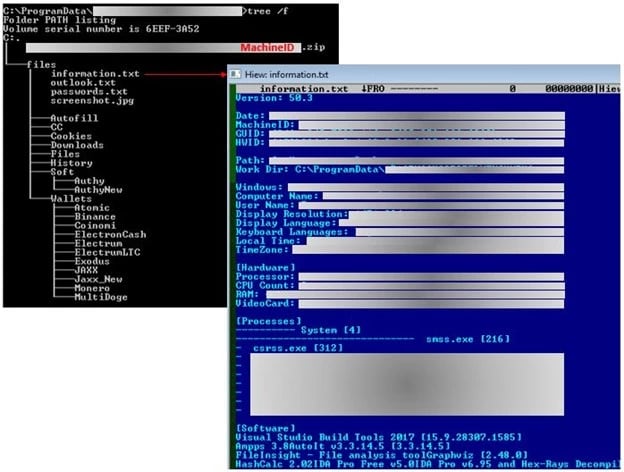
Vidar Malware Launcher Concealed in Help File
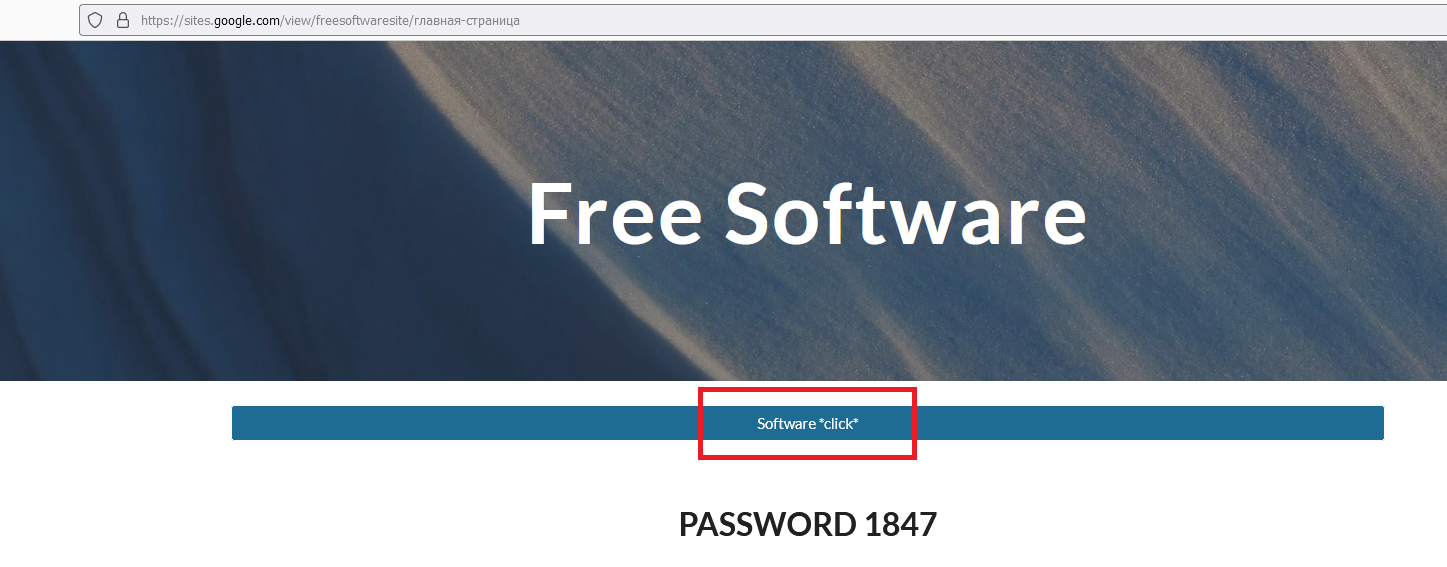
Vidar Infostealer Malware Returns with new TTPS – Detection & Response - Security Investigation
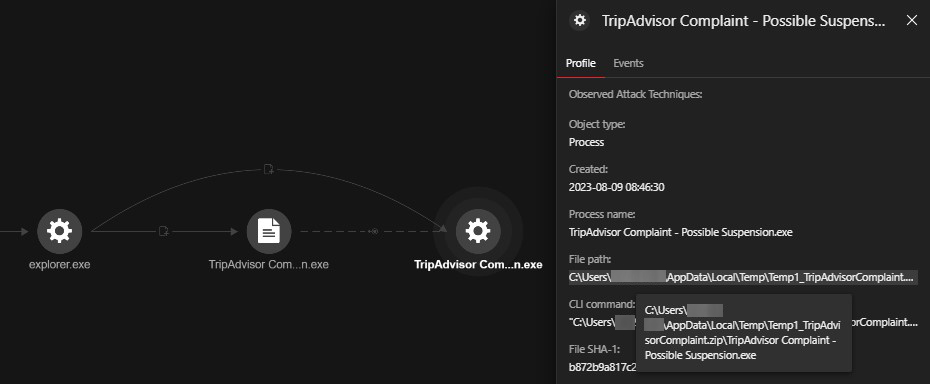
RedLine/Vidar Abuses EV Certificates, Shifts to Ransomware

Vidar Malware Conceals within Microsoft Help Files – TheCyberThrone

Vidar Malware Uses Microsoft Help Files to Launch Attacks

Operation Dragon Castling Targets Betting Companies

Vidar Stealer H&M Campaign - Toxin Labs
.jpg)
Fake Microsoft customer support and help file is actually Vidar malware that steals info - Neowin

Vidar Stealer Abuses Mastadon Social Network
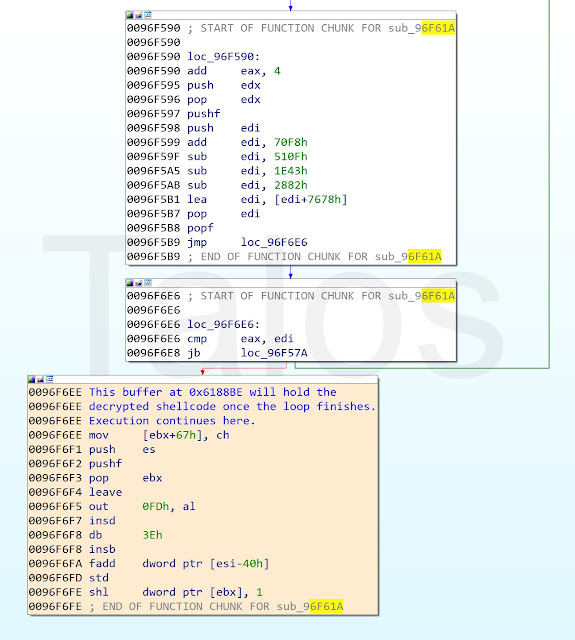
Old dog, new tricks - Analysing new RTF-based campaign distr - vulnerability database

Cyble — Vidar Stealer Under the Lens: A Deep-dive Analysis
Vidar Trojan Analysis, Malware Overview by
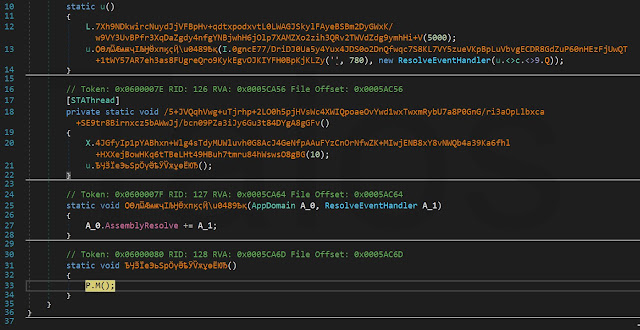
Old dog, new tricks - Analysing new RTF-based campaign distr - vulnerability database

Cybercriminals Abusing Open-Source Merlin Post-Exploitation Toolkit to Breach Entities
Recomendado para você
-
 Evade SCRIPT11 abril 2025
Evade SCRIPT11 abril 2025 -
 EVADE (AUTO REVIVE) – DailyPastebin11 abril 2025
EVADE (AUTO REVIVE) – DailyPastebin11 abril 2025 -
 Evade: Walkspeed, Auto Respawn, ESP Mobile Script11 abril 2025
Evade: Walkspeed, Auto Respawn, ESP Mobile Script11 abril 2025 -
 Facts Hub Evade Mobile Script11 abril 2025
Facts Hub Evade Mobile Script11 abril 2025 -
 The FDA Doesn't Care About Health Apps, So the Courts Stepped Up11 abril 2025
The FDA Doesn't Care About Health Apps, So the Courts Stepped Up11 abril 2025 -
 HOW TO BOOST YOUR FPS IN EVADE ROBLOX - BiliBili11 abril 2025
HOW TO BOOST YOUR FPS IN EVADE ROBLOX - BiliBili11 abril 2025 -
 Hackers Using New Obfuscation Mechanisms to Evade Detection11 abril 2025
Hackers Using New Obfuscation Mechanisms to Evade Detection11 abril 2025 -
New Cactus ransomware encrypts itself to evade antivirus11 abril 2025
-
 Seriously? Helping trouble-makers to evade moderation? : r/discordapp11 abril 2025
Seriously? Helping trouble-makers to evade moderation? : r/discordapp11 abril 2025 -
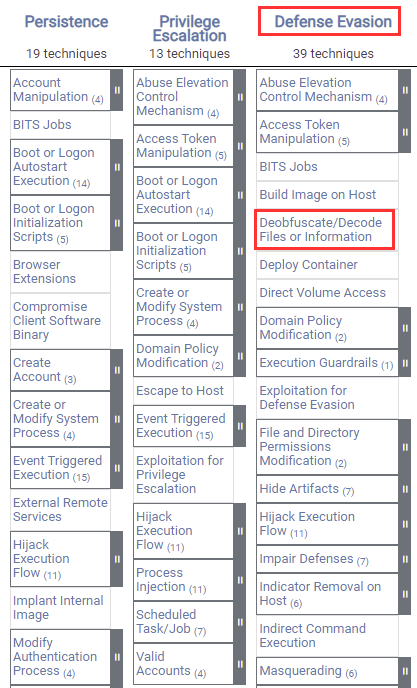 Windows Red Team Defense Evasion Techniques11 abril 2025
Windows Red Team Defense Evasion Techniques11 abril 2025
você pode gostar
-
 Meet the shameless gold diggers who will rinse wealthy men for their cash - and the man who LIKES it - Mirror Online11 abril 2025
Meet the shameless gold diggers who will rinse wealthy men for their cash - and the man who LIKES it - Mirror Online11 abril 2025 -
 Les Bleus champions du monde : Griezmann et Mbappé candidats au Ballon d'or - Le Parisien11 abril 2025
Les Bleus champions du monde : Griezmann et Mbappé candidats au Ballon d'or - Le Parisien11 abril 2025 -
 Al Nasr Saudi Club vs. Almeria Spanish Club Friendly Match11 abril 2025
Al Nasr Saudi Club vs. Almeria Spanish Club Friendly Match11 abril 2025 -
Pottery Barn Outlet - Northborough Popup — PHIONAH11 abril 2025
-
 Forza Motorsport 4 Wallpapers in high quality for your smartphone : r/forza11 abril 2025
Forza Motorsport 4 Wallpapers in high quality for your smartphone : r/forza11 abril 2025 -
 Baby Gregory (FNAF Security Breach Comic Dub)11 abril 2025
Baby Gregory (FNAF Security Breach Comic Dub)11 abril 2025 -
 Stream Bring Me The Horizon - Stay Doomed Prod. Vapid Shine by ✨ Vapid Shine ✨11 abril 2025
Stream Bring Me The Horizon - Stay Doomed Prod. Vapid Shine by ✨ Vapid Shine ✨11 abril 2025 -
Steam Workshop::[SESSION] Five Nights at Freddy's 3 Lighting11 abril 2025
-
 Mashle: Magic and Muscles Todos os Episódios Online » Anime TV Online11 abril 2025
Mashle: Magic and Muscles Todos os Episódios Online » Anime TV Online11 abril 2025 -
 Cutest Cats — follow cutest-cats for more adorable gifs11 abril 2025
Cutest Cats — follow cutest-cats for more adorable gifs11 abril 2025


![Steam Workshop::[SESSION] Five Nights at Freddy's 3 Lighting](https://steamuserimages-a.akamaihd.net/ugc/964234420704659961/EDEB01255B7089A3C40CEB22000FF76A7E7301E3/?imw=637&imh=358&ima=fit&impolicy=Letterbox&imcolor=%23000000&letterbox=true)