Hackers Using New Obfuscation Mechanisms to Evade Detection
Por um escritor misterioso
Last updated 07 abril 2025
Recently, Microsoft has unveiled details of a deceptive social engineering campaign, in which the operators proceeded to change their obfuscation
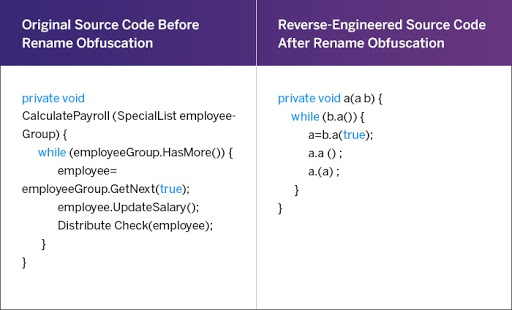
Code Obfuscation: A Comprehensive Guide Against Reverse
Threat Actors Using Obfuscation in Attempt to Evade Detection
A Deep Dive into 70 Layers of Obfuscated Info-Stealer Malware
Computer obfuscation: how can you protect yourself?

BlueNoroff Hackers Utilize ObjCShellz Malware to Create Backdoors
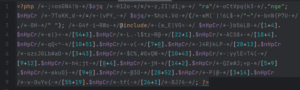
Threat Actors Using Obfuscation in Attempt to Evade Detection
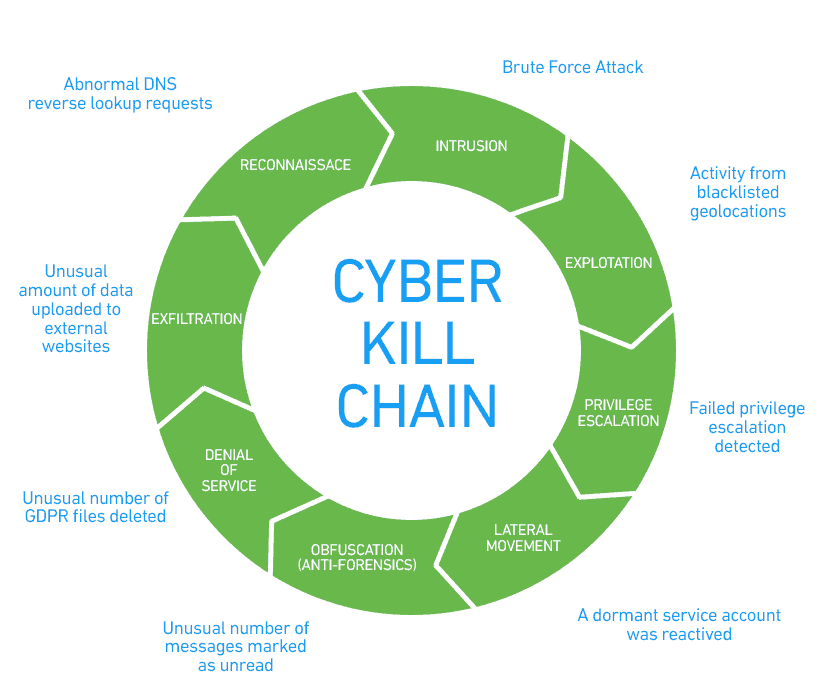
Cyber Kill Chain: Understanding and Mitigating Advanced Threats
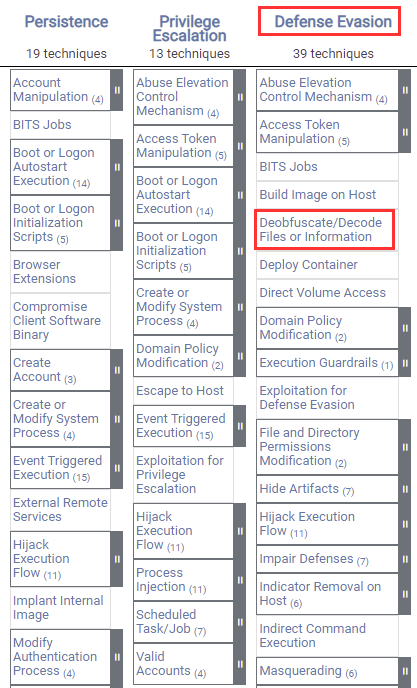
Windows Red Team Defense Evasion Techniques
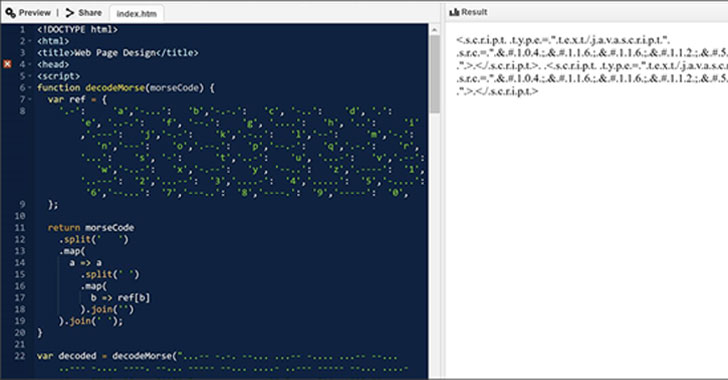
Hackers Spotted Using Morse Code in Phishing Attacks to Evade

LLMs lower the barrier for entry into cybercrime - Help Net Security

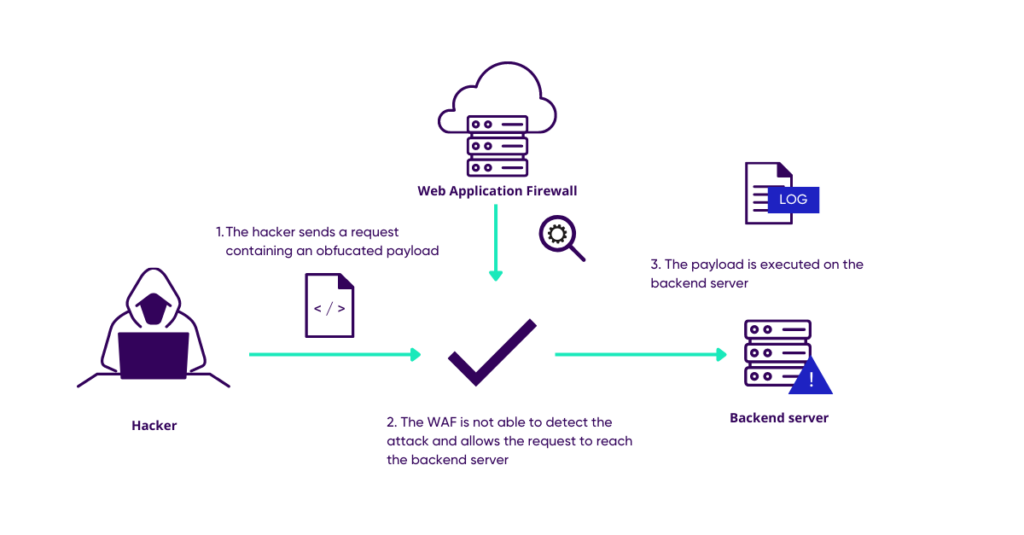
Web Application Obfuscation: '-/WAFs..Evasion..Filters//alert

What is C2? Command and Control Infrastructure Explained
Recomendado para você
-
 TrickGate, a packer used by malware to evade detection since 201607 abril 2025
TrickGate, a packer used by malware to evade detection since 201607 abril 2025 -
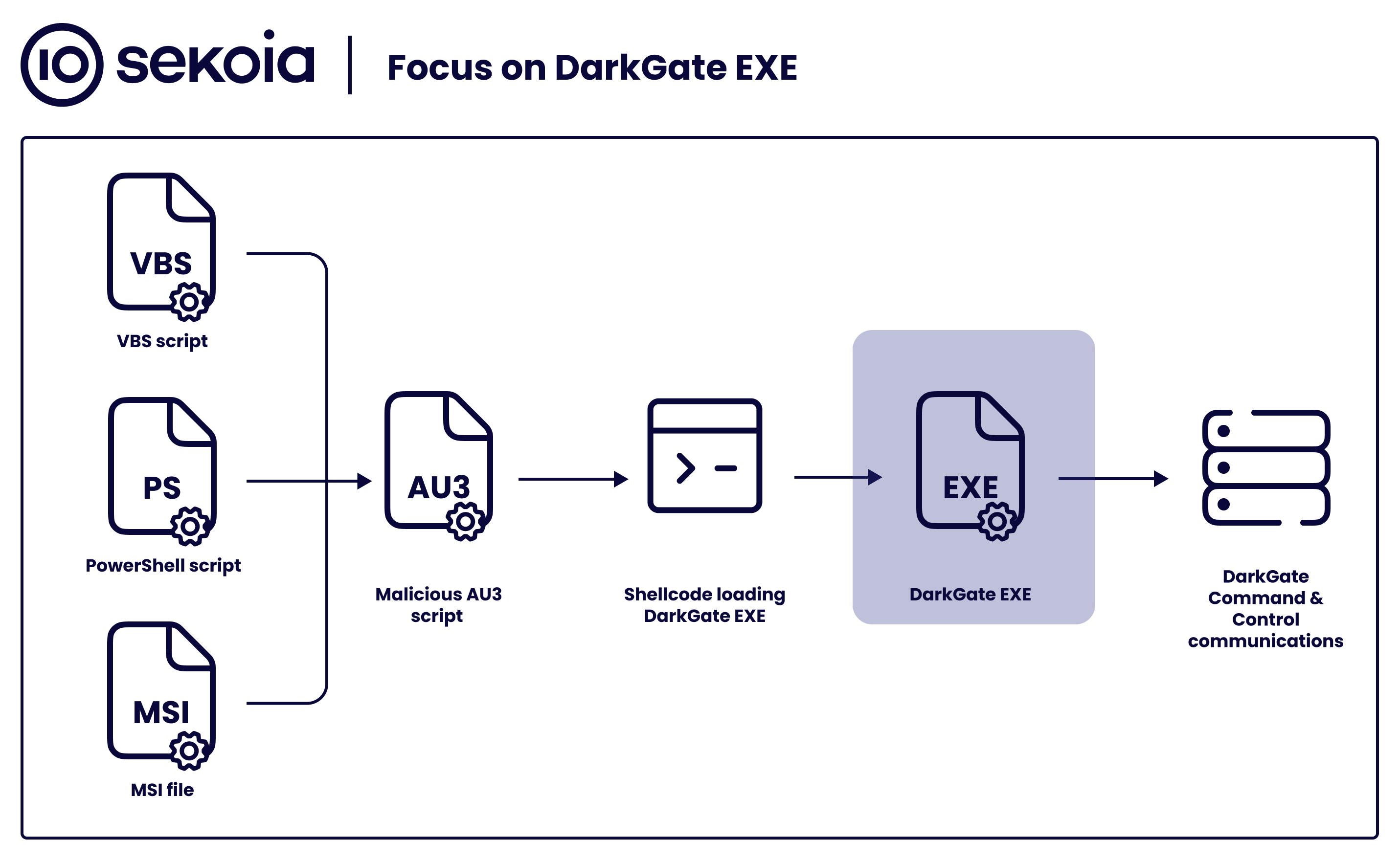
Sekoia.io on X: #DarkGate gained popularity among threat actors07 abril 2025
-
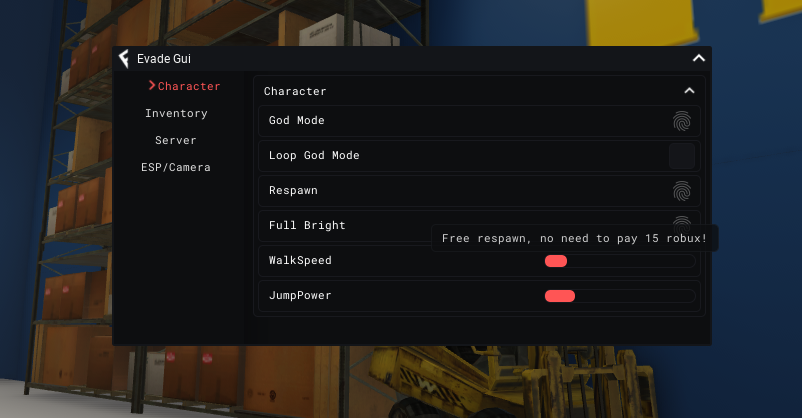
 Roblox Evade Script Pastebin Hacks - December 202307 abril 2025
Roblox Evade Script Pastebin Hacks - December 202307 abril 2025 -
 Facts Hub Evade Mobile Script07 abril 2025
Facts Hub Evade Mobile Script07 abril 2025 -
 How ransomware attackers evade your organization's security07 abril 2025
How ransomware attackers evade your organization's security07 abril 2025 -
 HOW TO BOOST YOUR FPS IN EVADE ROBLOX - BiliBili07 abril 2025
HOW TO BOOST YOUR FPS IN EVADE ROBLOX - BiliBili07 abril 2025 -
Roblox Script - Evade, God Mode, Auto Bhop, Server Crash, ESP, and More!07 abril 2025
-
 Eve 70 EVADE Daily Missions Build dow 40% Survive special rounds 250 Equipment Play Other Modes I Spectate Ro Leaderboard Othe: - iFunny07 abril 2025
Eve 70 EVADE Daily Missions Build dow 40% Survive special rounds 250 Equipment Play Other Modes I Spectate Ro Leaderboard Othe: - iFunny07 abril 2025 -
 How can I make a Night vision goggle tool? - Scripting Support - Developer Forum07 abril 2025
How can I make a Night vision goggle tool? - Scripting Support - Developer Forum07 abril 2025 -
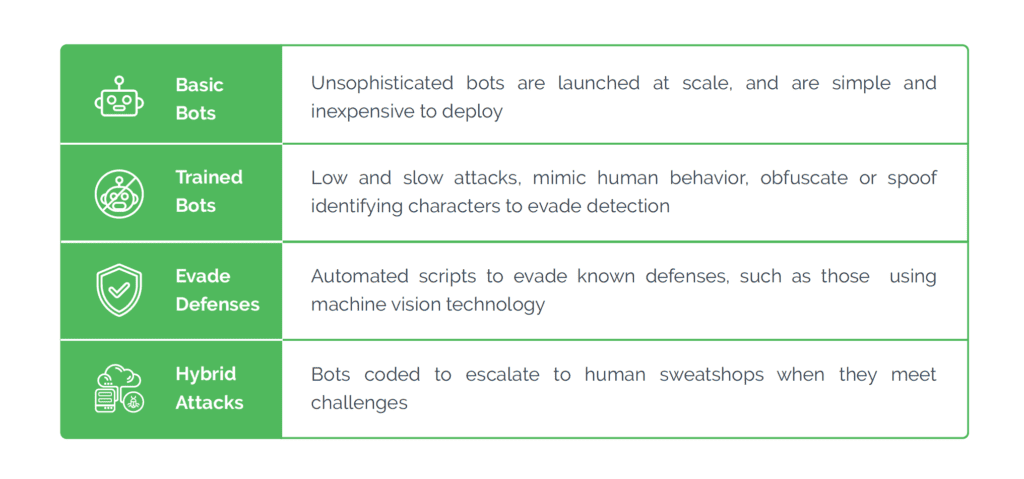 What Is Bot Detection?07 abril 2025
What Is Bot Detection?07 abril 2025
você pode gostar
-
 Life Is A Game: The inspirational success story of a legendary game developer!07 abril 2025
Life Is A Game: The inspirational success story of a legendary game developer!07 abril 2025 -
 Harry Potter: 10 Memes That Perfectly Sum Up The Malfoy Family07 abril 2025
Harry Potter: 10 Memes That Perfectly Sum Up The Malfoy Family07 abril 2025 -
 Easter egg, Blue Dotted Easter Egg with Pink Bow, blue and white07 abril 2025
Easter egg, Blue Dotted Easter Egg with Pink Bow, blue and white07 abril 2025 -
 Street Fighter 6: How to play online with friends07 abril 2025
Street Fighter 6: How to play online with friends07 abril 2025 -
 Kamisama gakkou no ochikobore - MangaDex07 abril 2025
Kamisama gakkou no ochikobore - MangaDex07 abril 2025 -
 Tecnicas de ataque en ajedrez07 abril 2025
Tecnicas de ataque en ajedrez07 abril 2025 -
 SCREAM 6 - Trailer (2023)07 abril 2025
SCREAM 6 - Trailer (2023)07 abril 2025 -
 atualizacao de 2023 do mx grau07 abril 2025
atualizacao de 2023 do mx grau07 abril 2025 -
 Gin no Guardian Season 1 + 2 Subtitle Indonesia07 abril 2025
Gin no Guardian Season 1 + 2 Subtitle Indonesia07 abril 2025 -
 Sonic, Shadow and Silver: Dreams of an Absolution (AMV)07 abril 2025
Sonic, Shadow and Silver: Dreams of an Absolution (AMV)07 abril 2025