From Code to Court: Role of Source Code in Detecting the FTX Fraud - UnitedLex
Por um escritor misterioso
Last updated 11 abril 2025

In the current digital world, where financial transactions are enveloped in layers of code.

Effective Law Firm Document Retention Policy

FTX reports new details of collapse, sets bar date for claims

What is the purpose of eDiscovery
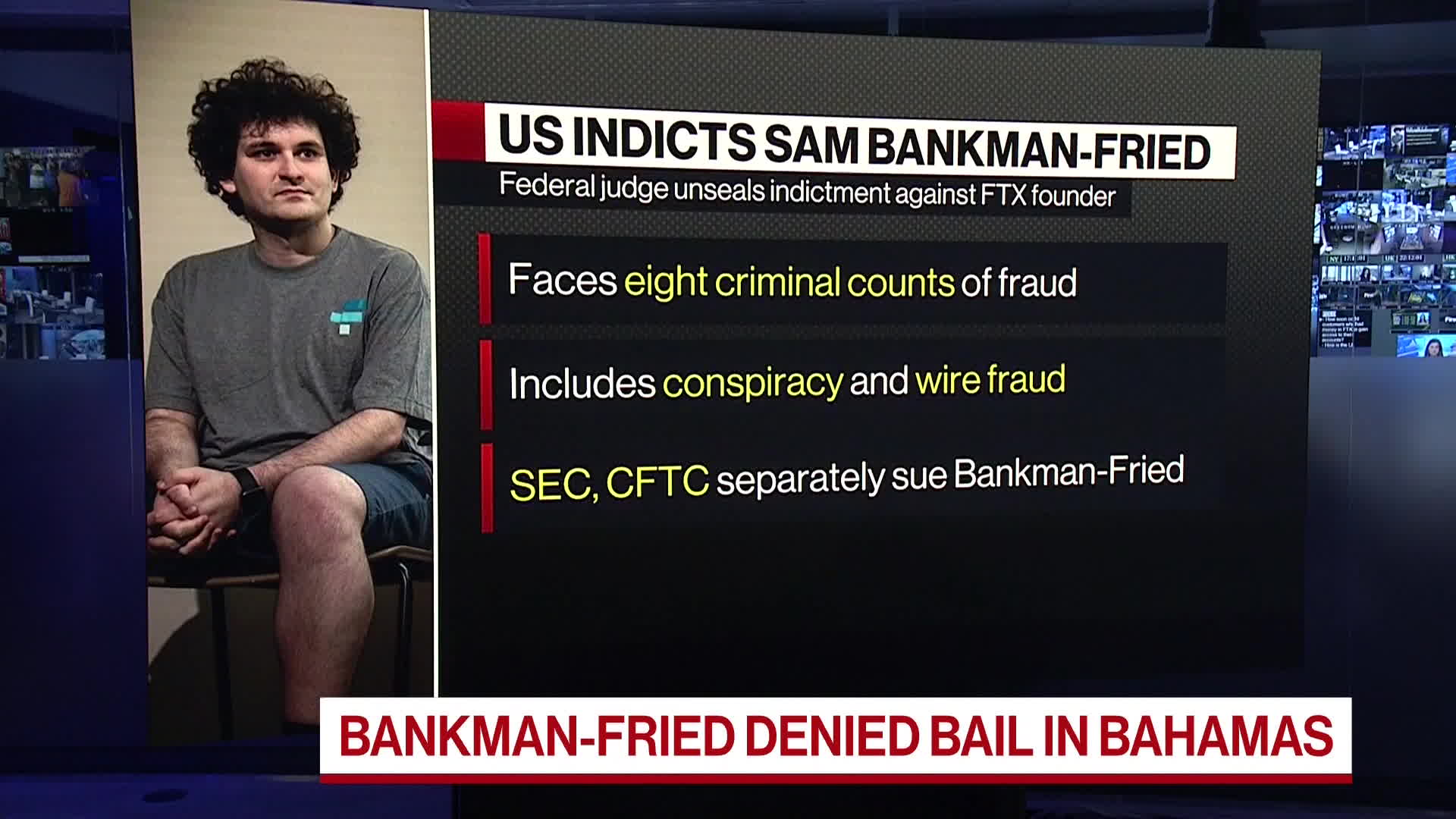
John J. Ray III Says at FTX Hearing US Customers Most Likely to Recoup Money - Bloomberg

FTX Python code 'allowed' Alameda Research to spend deposits • The Register

UnitedLex on LinkedIn: #bestinbusiness2022 #incbestinbusiness #positiveimpact #mission #values…

Is Tesla driving towards patent monetization by suing charging tech rival for refusing to take a license? - UnitedLex

Search & Analytics

UnitedLex on LinkedIn: #edi #ediscovery #rfp #litigation

UnitedLex on LinkedIn: Is Tesla driving towards patent monetization by suing charging tech rival…

UnitedLex on LinkedIn: #intellectualproperty #ip #ipmanagement #patent

New Trojan is simple, novel. Criminal activity targets East Asia. Insider risks. Applying SEC cyber rules. ICC hacked.
Recomendado para você
-
 Programmers 1080P, 2K, 4K, 5K HD wallpapers free download11 abril 2025
Programmers 1080P, 2K, 4K, 5K HD wallpapers free download11 abril 2025 -
 Programming Coding Language 4K Wallpaper #6.256411 abril 2025
Programming Coding Language 4K Wallpaper #6.256411 abril 2025 -
 Download 4k Laptop Programming Screen Wallpaper11 abril 2025
Download 4k Laptop Programming Screen Wallpaper11 abril 2025 -
 Wallpaper laptop, code, programming, programmer, hacker hd, picture, image11 abril 2025
Wallpaper laptop, code, programming, programmer, hacker hd, picture, image11 abril 2025 -
 Programmer Wallpapers on WallpaperDog11 abril 2025
Programmer Wallpapers on WallpaperDog11 abril 2025 -
 Download Programmers Heartbeat In Coding Wallpaper11 abril 2025
Download Programmers Heartbeat In Coding Wallpaper11 abril 2025 -
 IT Programmer write code program on the , Stock Video11 abril 2025
IT Programmer write code program on the , Stock Video11 abril 2025 -
 International Programmer's Day: Know the Remote Evolution – Turing11 abril 2025
International Programmer's Day: Know the Remote Evolution – Turing11 abril 2025 -
 Download 4k Programming Laptop Wallpaper11 abril 2025
Download 4k Programming Laptop Wallpaper11 abril 2025 -
 What could construction learn from software development standards11 abril 2025
What could construction learn from software development standards11 abril 2025
você pode gostar
-
Hora de Aventura com Fionna e Cake Temporada 1 - streaming11 abril 2025
-
Toy Partner - Roblox Celebrity Pack: Conjunto de Figuras e Acessórios (Vários modelos) ㅤ, ROBLOX11 abril 2025
-
 Almost Everybody Wins: Counter-Strike Online 211 abril 2025
Almost Everybody Wins: Counter-Strike Online 211 abril 2025 -
9th Annual Labor Day Classic - Photos11 abril 2025
-
 Celesteela GX - 208/214 - Full Art Ultra Rare - Pokemon Singles » Sun & Moon: Unbroken Bonds - Collector's Cache11 abril 2025
Celesteela GX - 208/214 - Full Art Ultra Rare - Pokemon Singles » Sun & Moon: Unbroken Bonds - Collector's Cache11 abril 2025 -
8 Ball Pool BR Fichas Compre e se sinta 100% seguro, além do nosso grupo no WhatsApp temos mais 3 grupos no Facebook: 8 Ball Pool - Galera da Sinuca (22 mil membros) 8 Bal11 abril 2025
-
 Time Wasters: Lollygag and Dillydally11 abril 2025
Time Wasters: Lollygag and Dillydally11 abril 2025 -
 4,083 Like And Dislike Balance Illustrations - Free in SVG, PNG, EPS - IconScout11 abril 2025
4,083 Like And Dislike Balance Illustrations - Free in SVG, PNG, EPS - IconScout11 abril 2025 -
 Horrortale Height Chart by AkaixZenny on DeviantArt11 abril 2025
Horrortale Height Chart by AkaixZenny on DeviantArt11 abril 2025 -
 Resident Evil 4 Remake First Look At Deluxe Edition Costumes11 abril 2025
Resident Evil 4 Remake First Look At Deluxe Edition Costumes11 abril 2025


