Evolution of the LockBit Ransomware operation relies on new techniques
Por um escritor misterioso
Last updated 11 abril 2025

Experts documented the evolution of the LockBit ransomware that leverages multiple techniques to infect targets and evade detection.
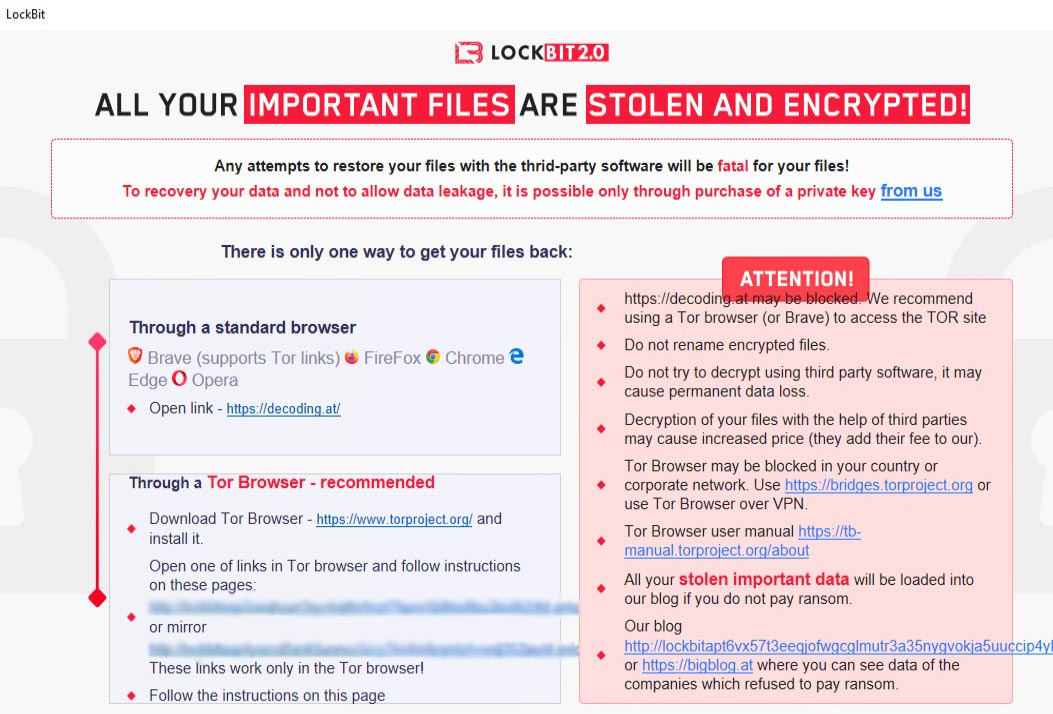
LockBit 2.0 Ransomware Becomes LockFile Ransomware with a Never-Before-Seen Encryption Method
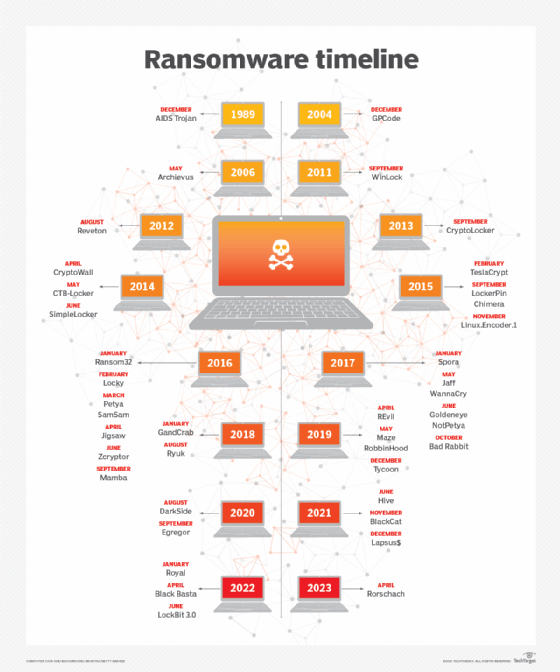
8 Types of Ransomware: Examples of Past and Current Attacks

How LockBit Changed Cybersecurity Forever
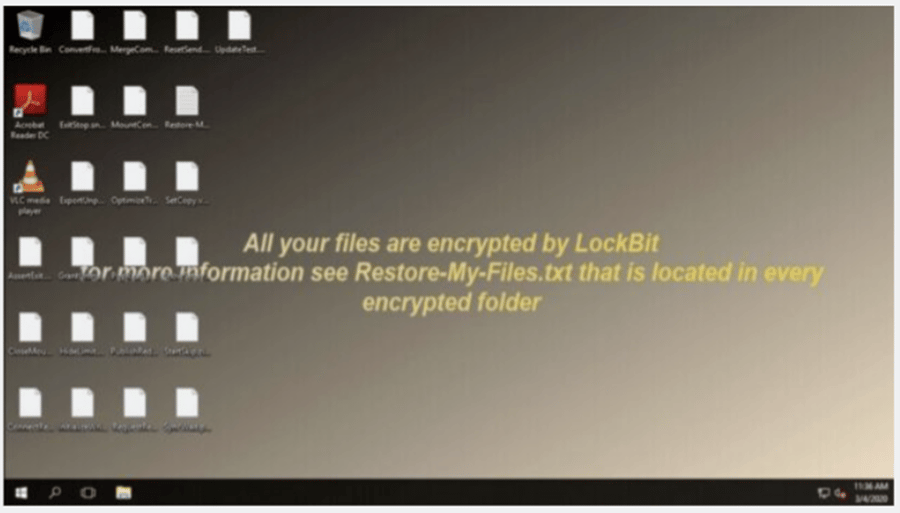
An In-Depth Look at Ransomware Gang, LockBit 3.0
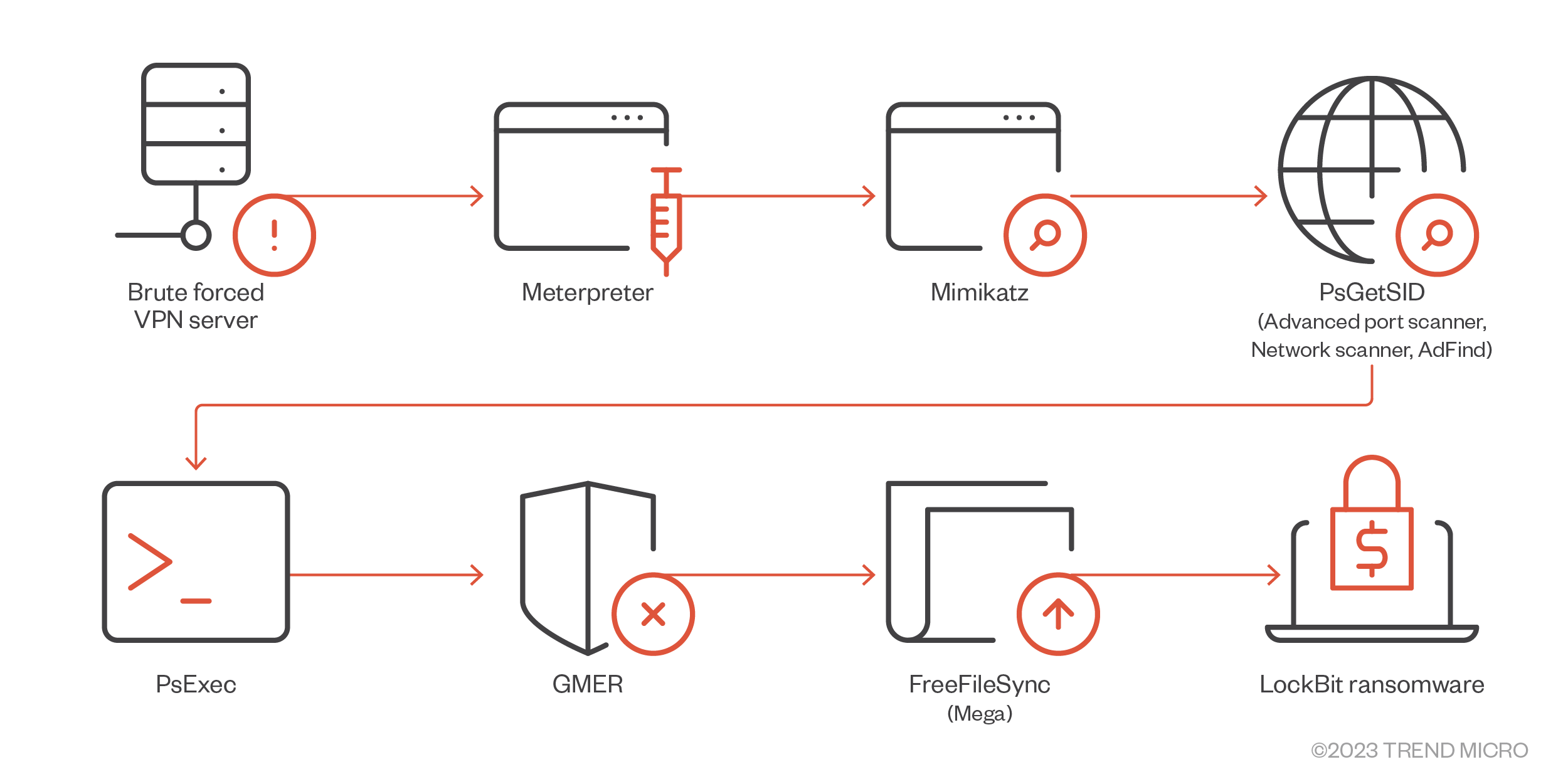
Ransomware Spotlight: LockBit - Security News

LockBit Ransomware Gang Introduces the First Ransomware Bug Bounty Program in the Dark Web

LockBit Ransomware Targets OT
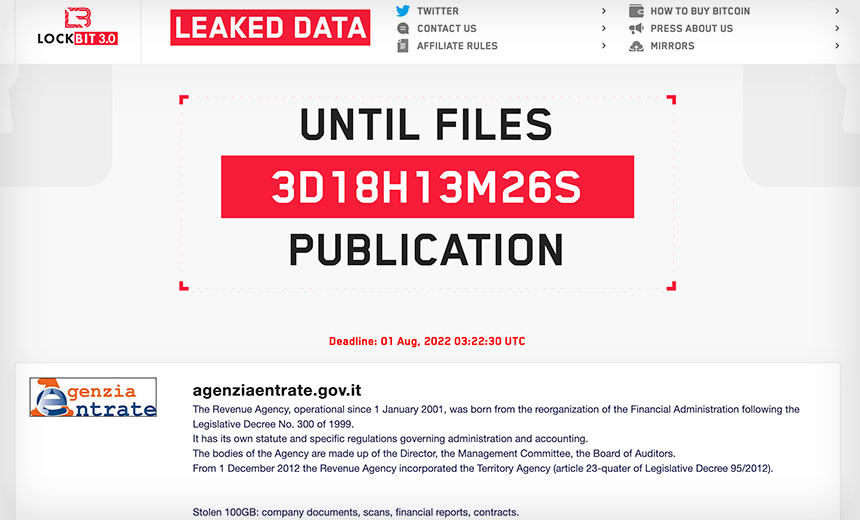
Keys to LockBit's Success: Self-Promotion, Technical Acumen
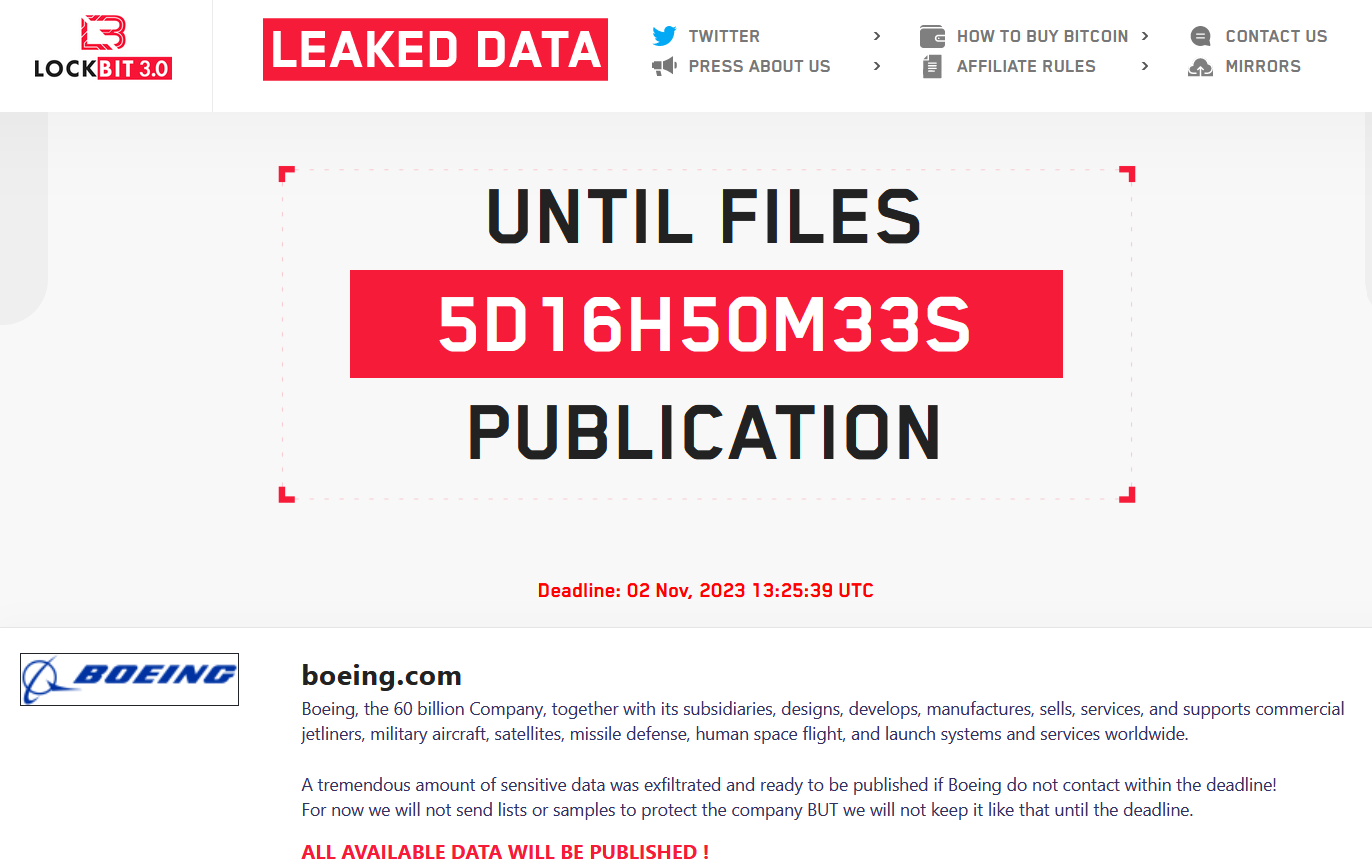
LockBit Ransomware Archives - Security Affairs

What is the LockBit Ransomware? - Computer One Australia
.jpg?1686841193)
CISA releases information on LockBit
Recomendado para você
-
 Evades io Videos —11 abril 2025
Evades io Videos —11 abril 2025 -
 Quiet Quarry, Evades.io Wiki11 abril 2025
Quiet Quarry, Evades.io Wiki11 abril 2025 -
 How SARS-CoV-2 evades the immune system11 abril 2025
How SARS-CoV-2 evades the immune system11 abril 2025 -
 Restless Ridge, Evades.io Wiki11 abril 2025
Restless Ridge, Evades.io Wiki11 abril 2025 -
 AVS Display Cards for Tablets 1.111 abril 2025
AVS Display Cards for Tablets 1.111 abril 2025 -
 Specialized S-Works Evade II ANGI MIPS Down Under LTD - Arizona's11 abril 2025
Specialized S-Works Evade II ANGI MIPS Down Under LTD - Arizona's11 abril 2025 -
 Evades.io - *NEW AREA* COUPLED CORRIDORS + *NEW* ENEMIES??11 abril 2025
Evades.io - *NEW AREA* COUPLED CORRIDORS + *NEW* ENEMIES??11 abril 2025 -
 Arsenal's Nicolas Anelka evades a tackle from West Ham United's11 abril 2025
Arsenal's Nicolas Anelka evades a tackle from West Ham United's11 abril 2025 -
 Shimmer Myr · March of the Machine Commander (MOC) #376 · Scryfall11 abril 2025
Shimmer Myr · March of the Machine Commander (MOC) #376 · Scryfall11 abril 2025 -
 B.1.617.2 enters and fuses lung cells with increased efficiency11 abril 2025
B.1.617.2 enters and fuses lung cells with increased efficiency11 abril 2025
você pode gostar
-
 Y2k butterfly Free t shirt design, Roblox t shirts, Roblox shirt11 abril 2025
Y2k butterfly Free t shirt design, Roblox t shirts, Roblox shirt11 abril 2025 -
 Giovanni è il nuovo postino di C'è Posta per Te11 abril 2025
Giovanni è il nuovo postino di C'è Posta per Te11 abril 2025 -
 Dunder Mifflin Paper Company Inc. Hoodie - Office Hooded Sweatshirt11 abril 2025
Dunder Mifflin Paper Company Inc. Hoodie - Office Hooded Sweatshirt11 abril 2025 -
 HVirtua - caindo-de-paraquedas - Jogos Educativos11 abril 2025
HVirtua - caindo-de-paraquedas - Jogos Educativos11 abril 2025 -
 A 3d image of a coat of arms. Russian flag russian coat of arms11 abril 2025
A 3d image of a coat of arms. Russian flag russian coat of arms11 abril 2025 -
 Steam Support :: Steam and macOS 10.15 Catalina11 abril 2025
Steam Support :: Steam and macOS 10.15 Catalina11 abril 2025 -
Game Exchange Namibia, FIFA 22 DEMO is available on the PS311 abril 2025
-
 Fix Roblox cursor going off screen on Windows PC11 abril 2025
Fix Roblox cursor going off screen on Windows PC11 abril 2025 -
99puzzles.com - Os Melhores Puzzles11 abril 2025
-
 Página 6 Jogo Galinha Imagens – Download Grátis no Freepik11 abril 2025
Página 6 Jogo Galinha Imagens – Download Grátis no Freepik11 abril 2025
