11 Types of Spoofing Attacks Every Security Professional Should
Por um escritor misterioso
Last updated 11 abril 2025

The term “spoofing” might have a comic implication in some contexts, but it’s no joke when it comes to information security. In fact, this is a subject matter of a whole separate chapter in a seasoned cybercriminal’s handbook. It comprises a multitude of techniques aimed at camouflaging a malicious actor or device as somebody or something else. The goal is to feign trust, gain a foothold in a system, get hold of data, pilfer money, or distribute predatory software. What can black hats try to . . .
The term “spoofing” might have a comic implication in some contexts, but it’s no joke when it comes to information security. In fact, this is a subject matter of a whole separate chapter in a seasoned cybercriminal’s handbook. It comprises a multitude of techniques aimed at camouflaging a malicious actor or device as somebody or something else. Out of all the nefarious scenarios that fit the mold of a spoofing attack, the following 11 types are growingly impactful for the enterprise these days.

20 types of phishing attacks + phishing examples - Norton

Email Spoofing Protection Software - N-able

Spoofing Attacks, Spoofing Vs Phishing
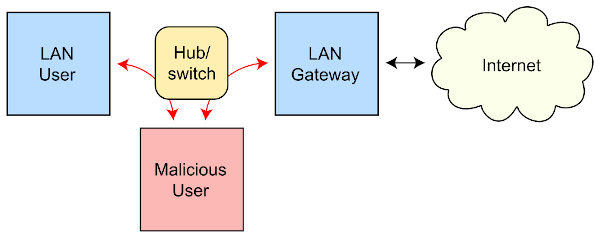
11 Types of Spoofing Attacks You Should Know About

The Comprehensive Guide to 11 Types of Malware in 2023 - TitanFile

6 Common Phishing Attacks and How to Protect Against Them

Most Common Types of Cyber Attacks on Small Businesses

What is Spoofing Attack?
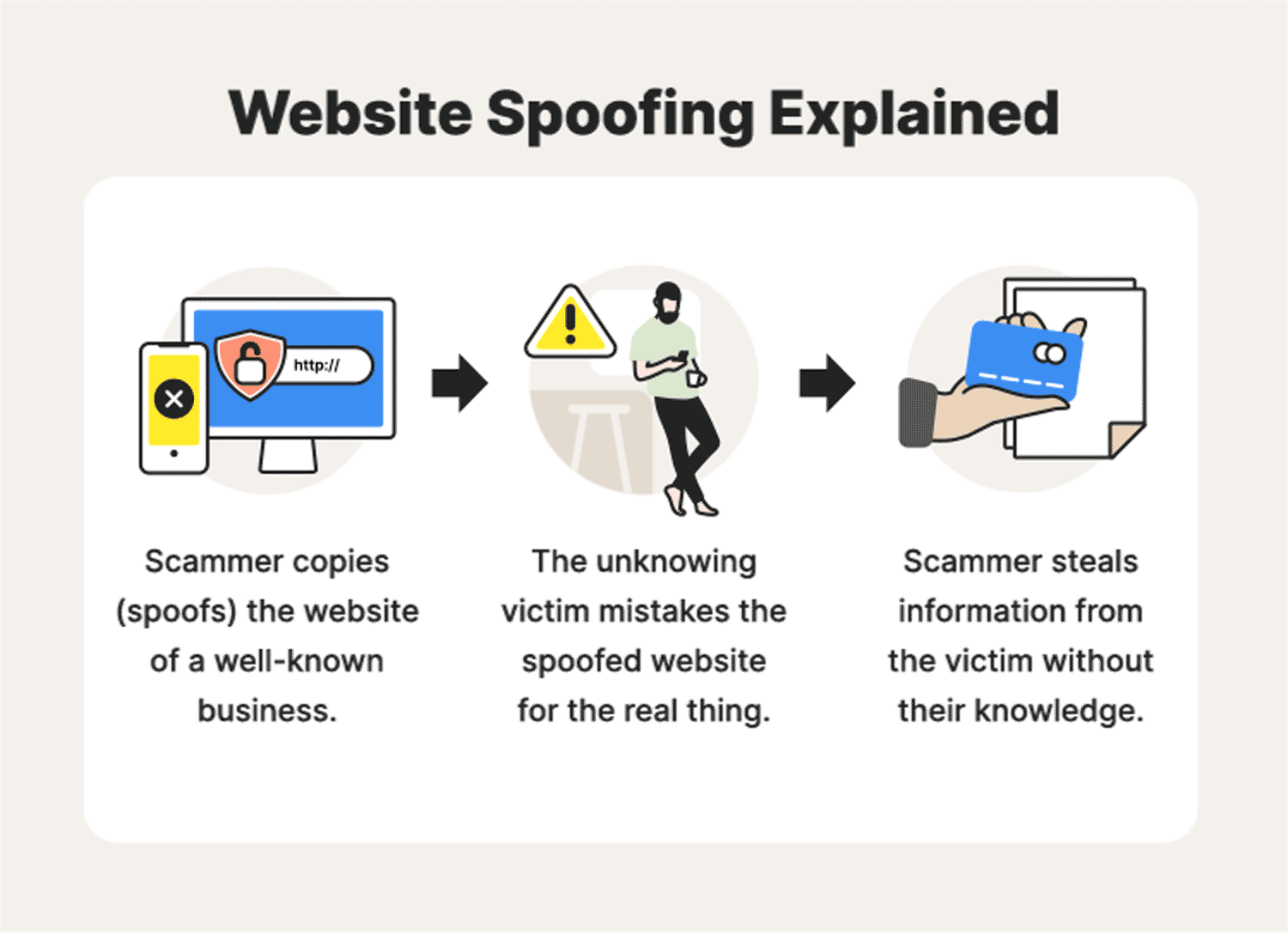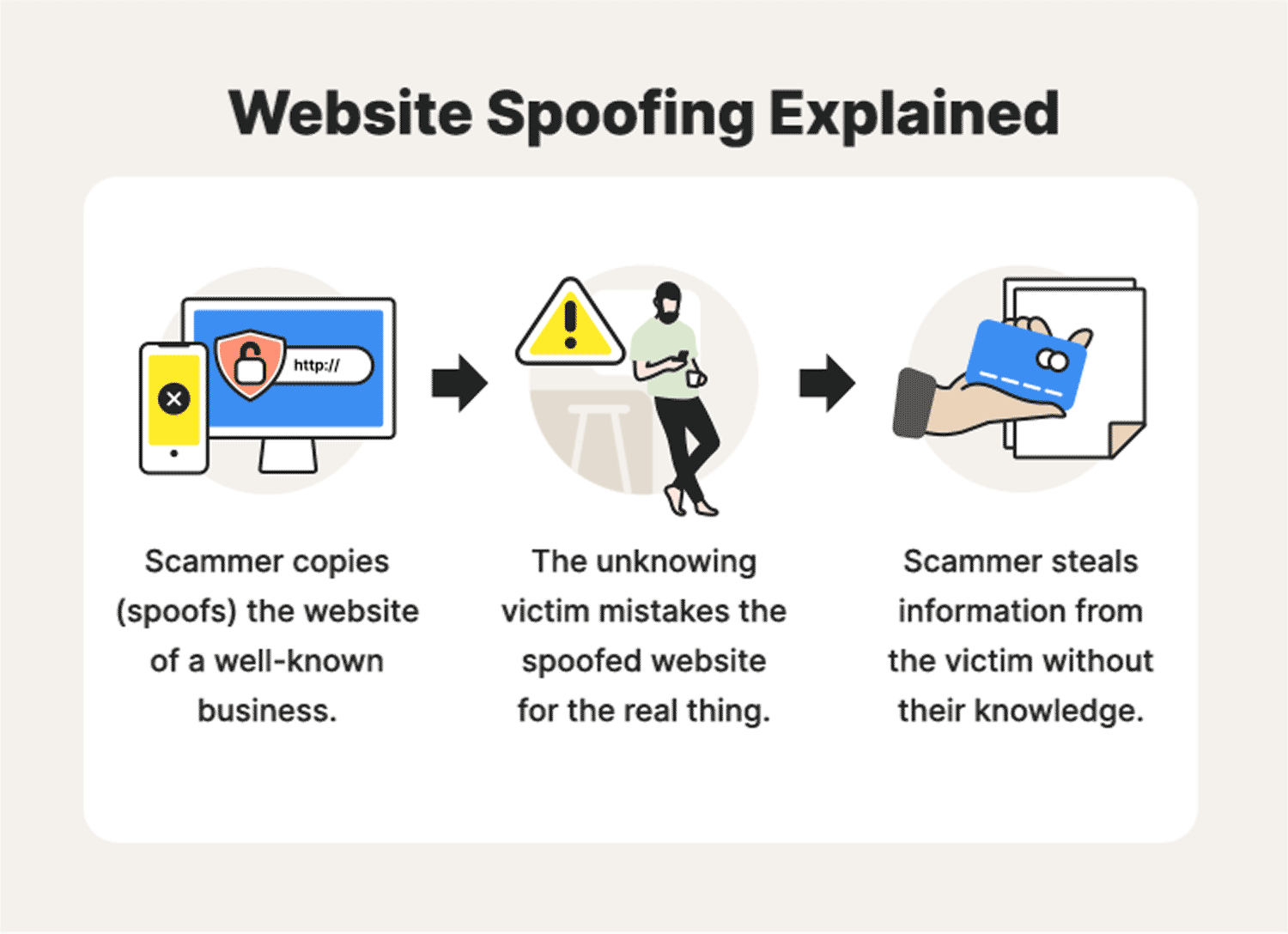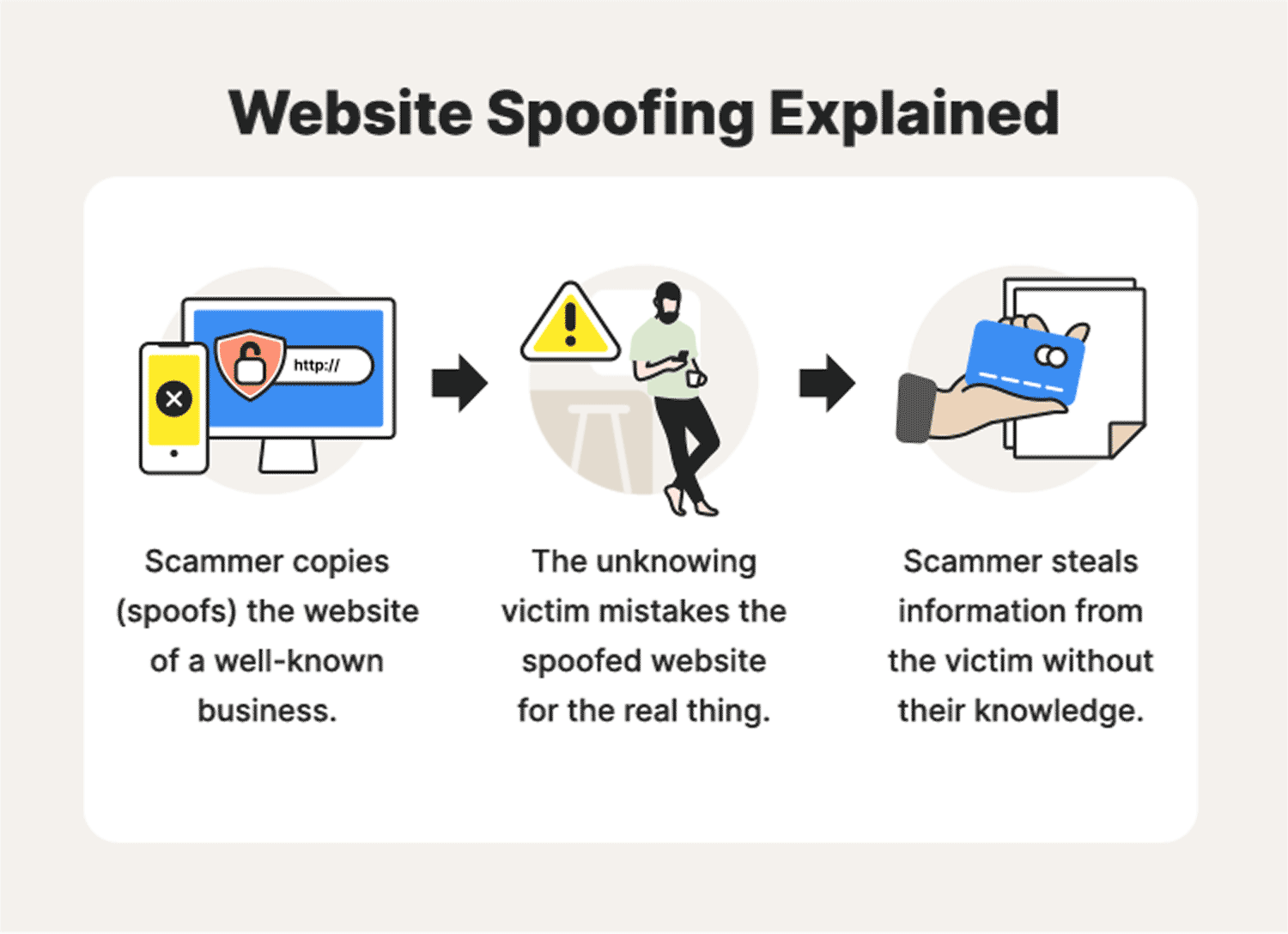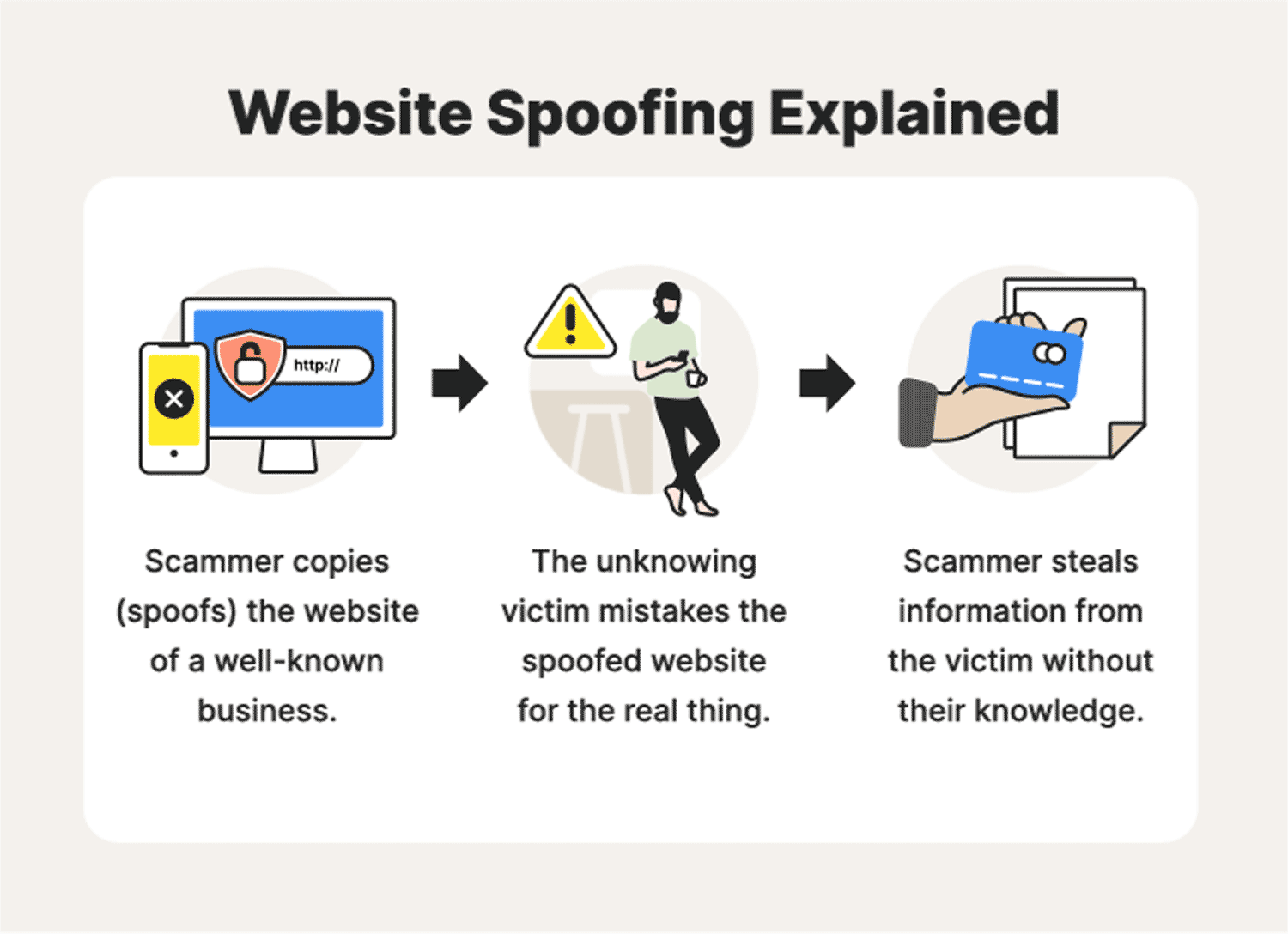
Website spoofing: A definition + how spoofing works

6 Common Phishing Attacks and How to Protect Against Them

Network Protocols for Security Professionals
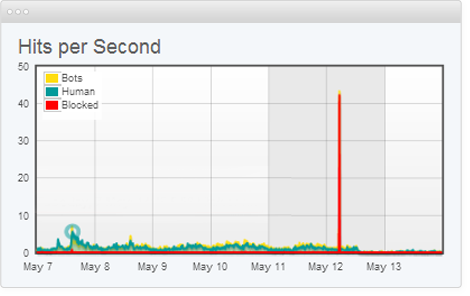
DDoS Attack Types & Mitigation Methods

The 4 Main Types of Spoofing Attacks and How to Prevent Them
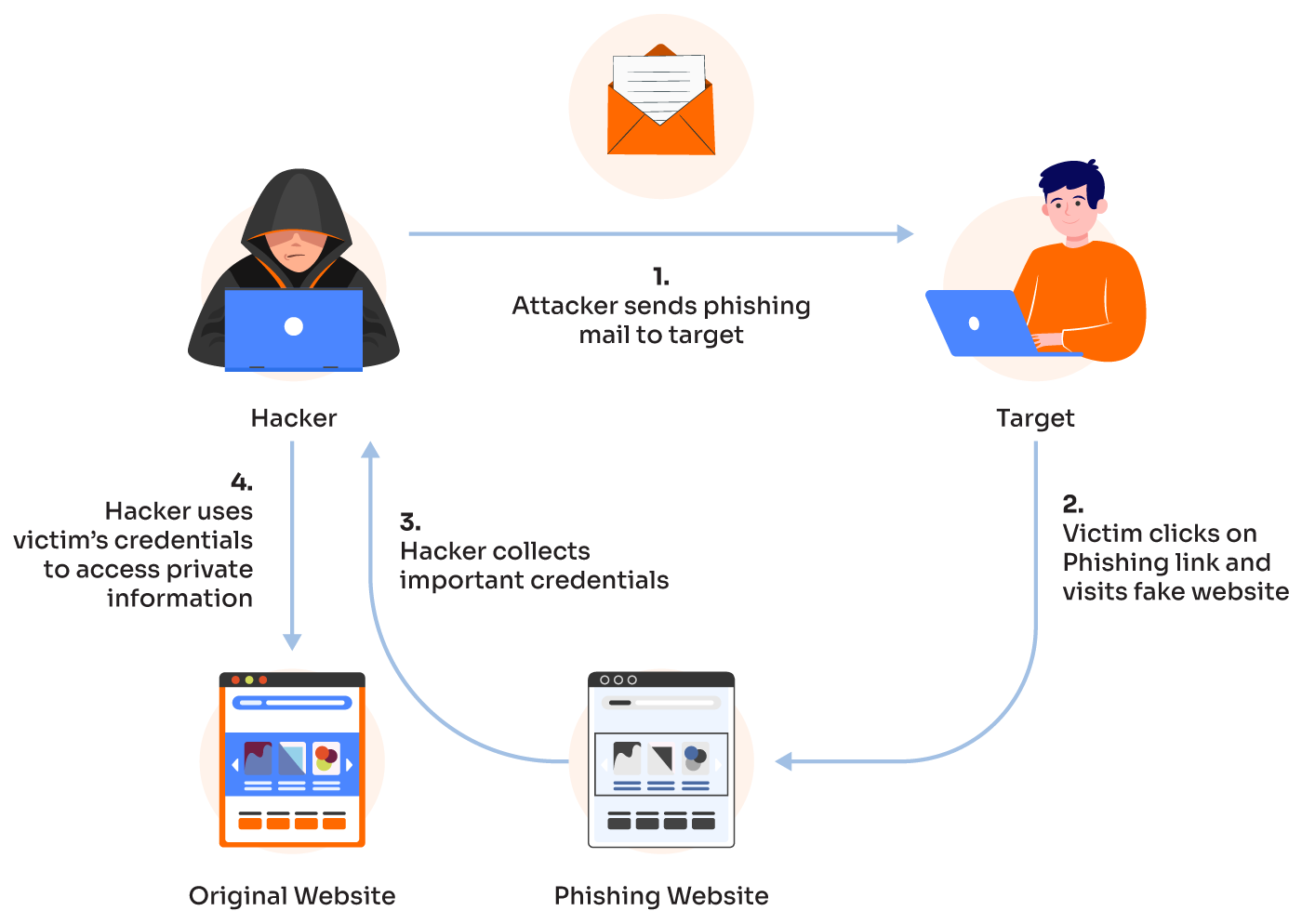
Complete Guide to Phishing: Techniques & Mitigations - Valimail
Recomendado para você
-
 HOW TO REDEEM YOUR REDENGINE KEY AND DOWNLOAD REDENGINE!11 abril 2025
HOW TO REDEEM YOUR REDENGINE KEY AND DOWNLOAD REDENGINE!11 abril 2025 -
GitHub - SonsoFsERpent/redEngine-Spoofer: With the redENGINE11 abril 2025
-
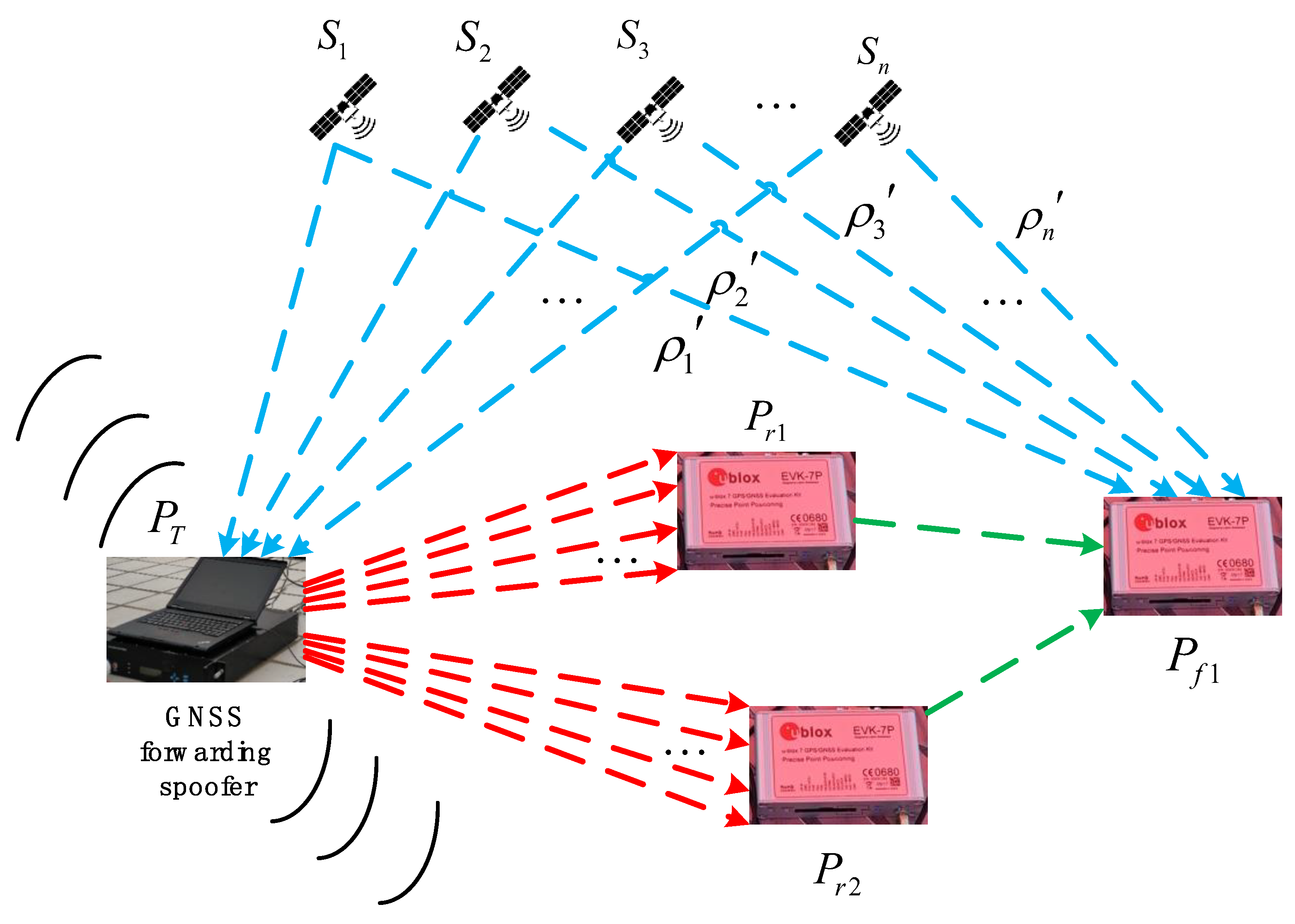 Sensors, Free Full-Text11 abril 2025
Sensors, Free Full-Text11 abril 2025 -
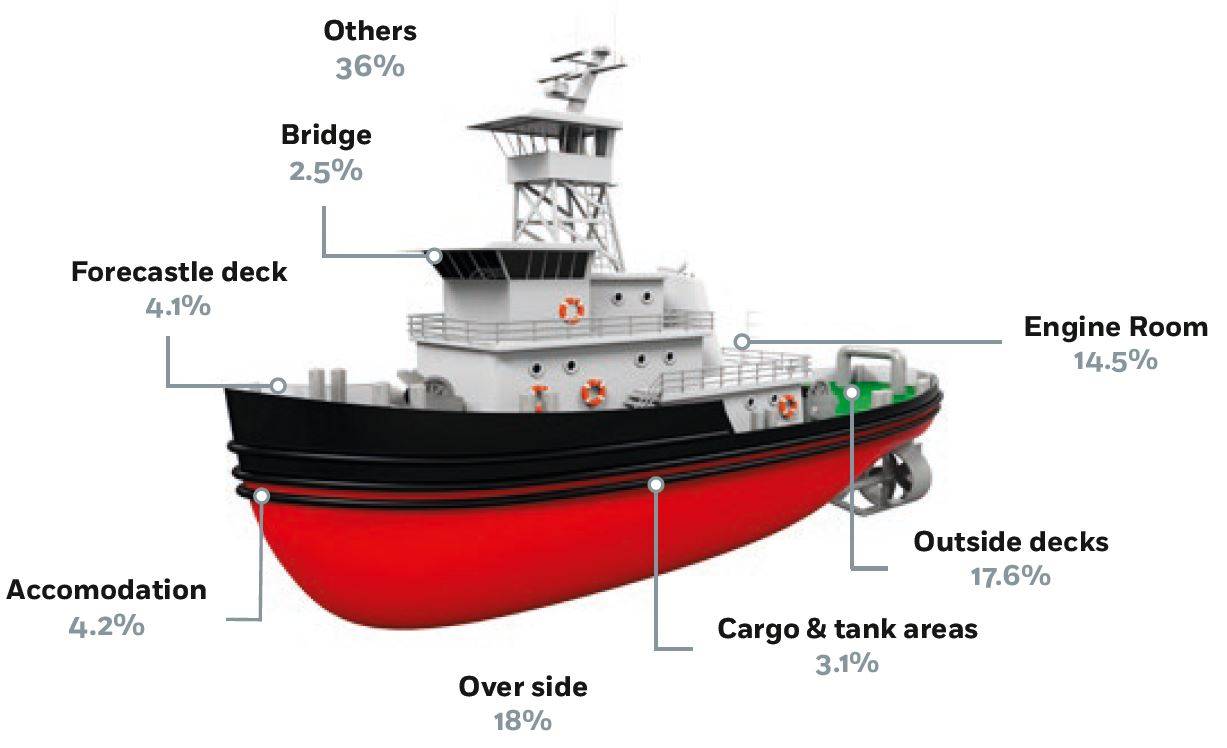 Autonomous Shipping – Cyber Hazards Ahead11 abril 2025
Autonomous Shipping – Cyber Hazards Ahead11 abril 2025 -
 Off-Road Racebikes—Ty Cullins' 2022 TM EN 30011 abril 2025
Off-Road Racebikes—Ty Cullins' 2022 TM EN 30011 abril 2025 -
 Beware of Spoof Websites - RCB Bank11 abril 2025
Beware of Spoof Websites - RCB Bank11 abril 2025 -
Hack The Seas Village - AIS Spoofing Attacks and Some Tools - TIB11 abril 2025
-
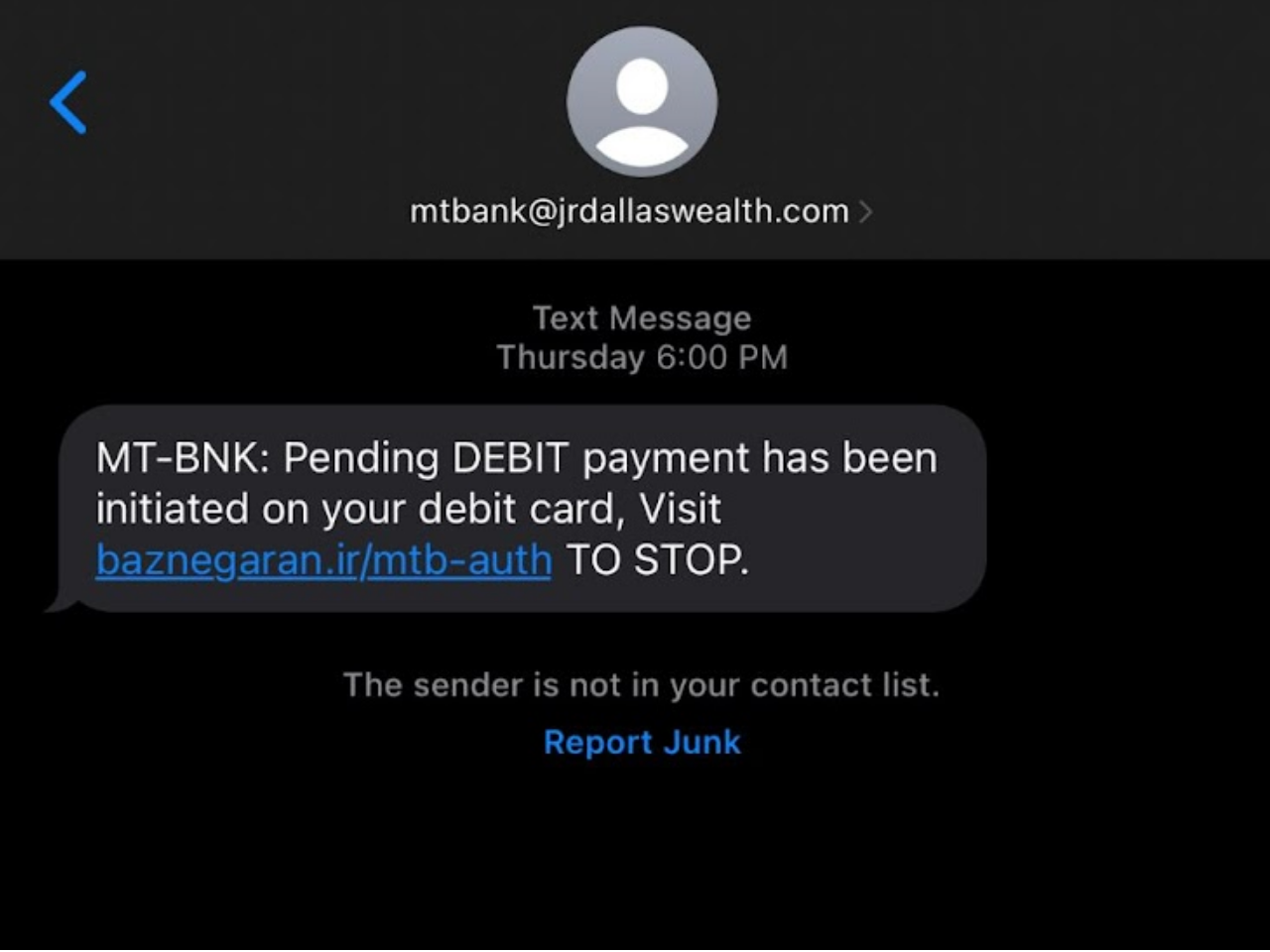 What Is Spoofing In Cybersecurity?11 abril 2025
What Is Spoofing In Cybersecurity?11 abril 2025 -
Cracked Hwid Spoofer11 abril 2025
-
 Protecting GPS From Spoofers Is Critical to the Future of11 abril 2025
Protecting GPS From Spoofers Is Critical to the Future of11 abril 2025
você pode gostar
-
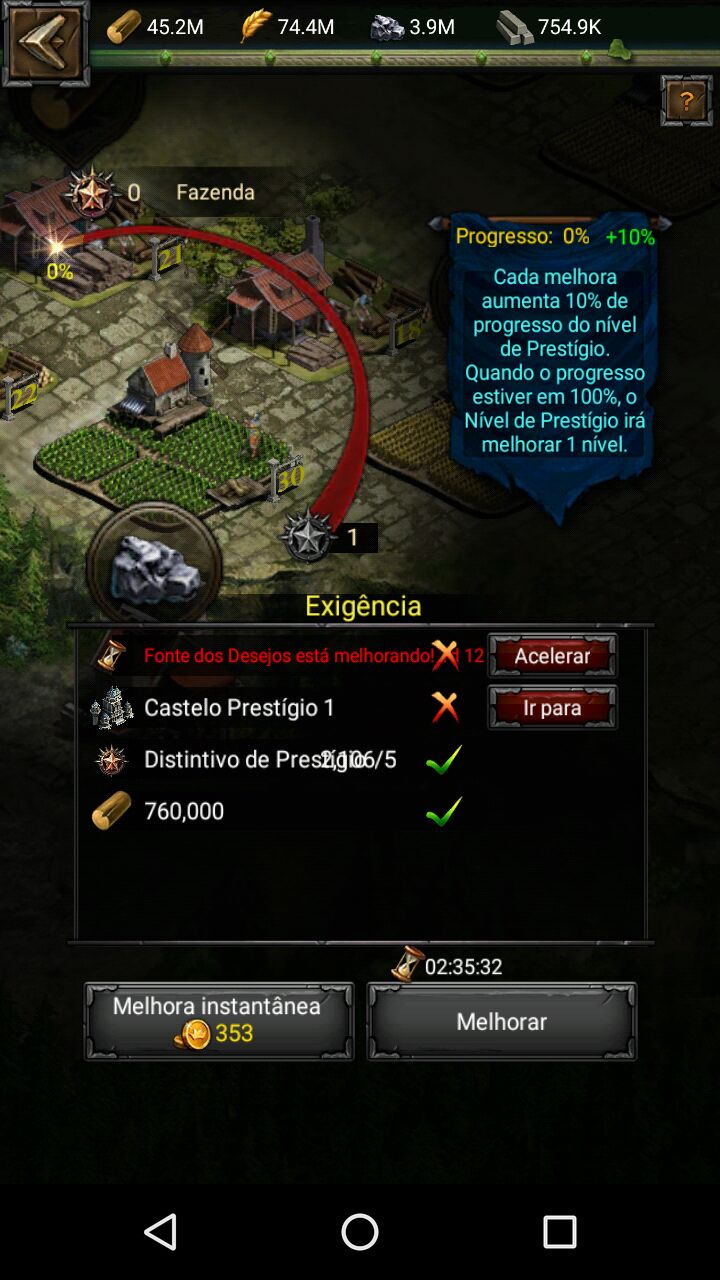 Prestigio 1 e 2 ~ Clash of Kings Brasil11 abril 2025
Prestigio 1 e 2 ~ Clash of Kings Brasil11 abril 2025 -
 All Of Us Are Dead' Renewed Season 2 Netflix — 'Warrior Nun11 abril 2025
All Of Us Are Dead' Renewed Season 2 Netflix — 'Warrior Nun11 abril 2025 -
 WBC final: Japan wins 3-2 in victory over Team USA11 abril 2025
WBC final: Japan wins 3-2 in victory over Team USA11 abril 2025 -
 Os 35 principais modelos de PowerPoint de quebra-cabeças para incrementar suas palestras!!11 abril 2025
Os 35 principais modelos de PowerPoint de quebra-cabeças para incrementar suas palestras!!11 abril 2025 -
 Requests are OPEN 🖤🎃🖤 — omg hiii majin sonic11 abril 2025
Requests are OPEN 🖤🎃🖤 — omg hiii majin sonic11 abril 2025 -
 12/20/2023 MARVELS SPIDER-MAN 2 SUIT VARIANT SET OF 10 COMICS11 abril 2025
12/20/2023 MARVELS SPIDER-MAN 2 SUIT VARIANT SET OF 10 COMICS11 abril 2025 -
 Como pronunciar Warrior Nun11 abril 2025
Como pronunciar Warrior Nun11 abril 2025 -
David Berlinski Penguin Random House11 abril 2025
-
 Recomendação de anime - Summer Time Rendering, um anime de tirar o11 abril 2025
Recomendação de anime - Summer Time Rendering, um anime de tirar o11 abril 2025 -
 Killing Bite Harem x Shy/Child Like Shota Dragon Brute Reader in 202311 abril 2025
Killing Bite Harem x Shy/Child Like Shota Dragon Brute Reader in 202311 abril 2025
