Attackers use dynamic code loading to bypass Google Play store's
Por um escritor misterioso
Last updated 10 abril 2025

Threat actors rely on the 'versioning' technique to evade malware detections of malicious code uploaded to the Google Play Store
3 Google Play Store Apps Exploit Android Zero-Day Used by NSO Group

Deadglyph, a very sophisticated and unknown backdoor targets the

Android App Disguised as a QR scanner, Spreads Joker Variant Trojan
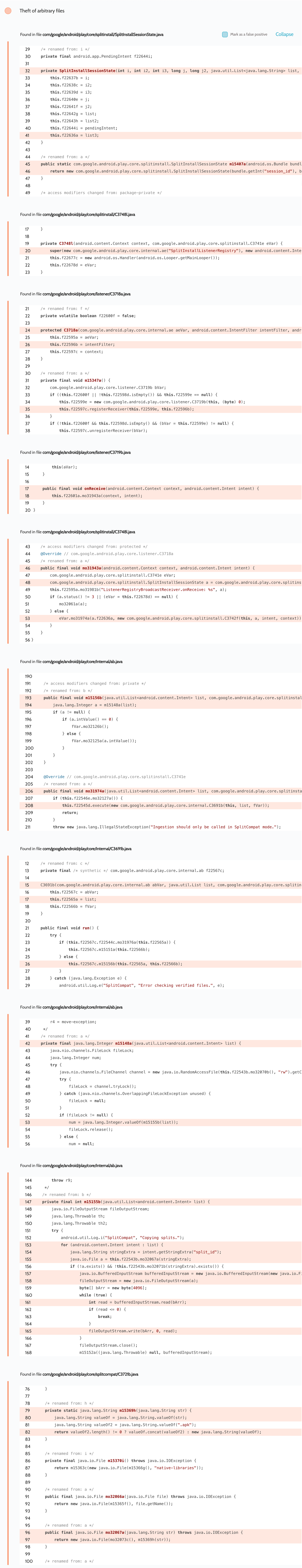
Oversecured automatically discovers persistent code execution in

This is how malicious Android apps avoid Google's security vetting

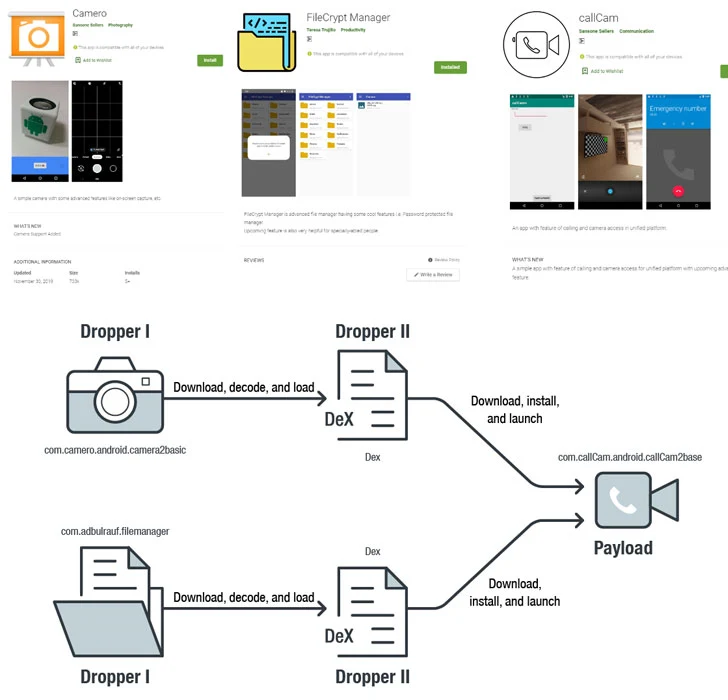
Malicious Apps Use Sneaky Versioning Technique to Bypass Google
Technologies, Free Full-Text

Android: With Android 14, Google has a new plan to make your
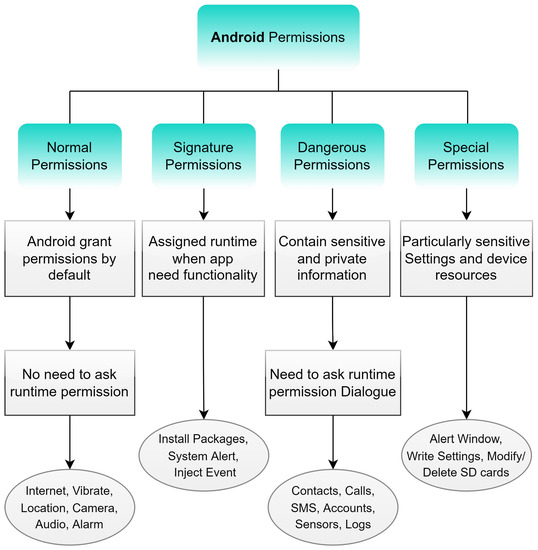
Technologies, Free Full-Text

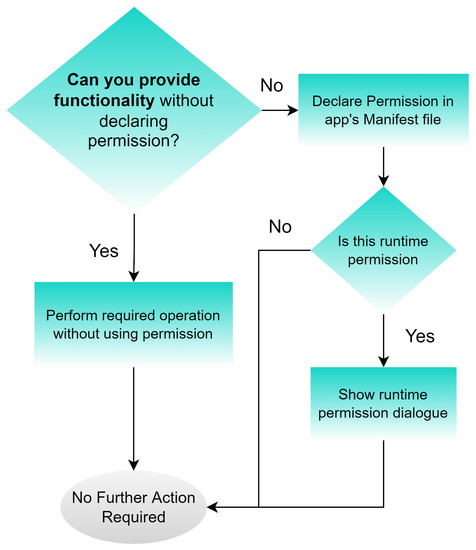
Dynamic analysis and tampering
Recomendado para você
-
 Roblox Evade Codes (November 2023)10 abril 2025
Roblox Evade Codes (November 2023)10 abril 2025 -
 Roblox Evade – Free codes (December 2023) - Xfire10 abril 2025
Roblox Evade – Free codes (December 2023) - Xfire10 abril 2025 -
 Roblox Evade Codes (March 2023)10 abril 2025
Roblox Evade Codes (March 2023)10 abril 2025 -
 All Evade Codes(Roblox) - Tested December 2022 - Player Assist10 abril 2025
All Evade Codes(Roblox) - Tested December 2022 - Player Assist10 abril 2025 -
 Roblox Evade Codes (June 2023): Free Customization10 abril 2025
Roblox Evade Codes (June 2023): Free Customization10 abril 2025 -
 Roblox Evolution Evade Codes January 2023 in 202310 abril 2025
Roblox Evolution Evade Codes January 2023 in 202310 abril 2025 -
 Chinese-backed DragonSpark hackers evade detection with SparkRAT10 abril 2025
Chinese-backed DragonSpark hackers evade detection with SparkRAT10 abril 2025 -
 Codes d'évasion (novembre 2022) – Guides de jeu professionnels10 abril 2025
Codes d'évasion (novembre 2022) – Guides de jeu professionnels10 abril 2025 -
 Stranger Danger - Self-Defense, Escape & Evade10 abril 2025
Stranger Danger - Self-Defense, Escape & Evade10 abril 2025 -
Data Encoder Crypter10 abril 2025
você pode gostar
-
Jotaro Kujo10 abril 2025
-
 Dio brando images on10 abril 2025
Dio brando images on10 abril 2025 -
 BEYBLADE X Kamen X Ekusu Kurosu Cosplay Costume10 abril 2025
BEYBLADE X Kamen X Ekusu Kurosu Cosplay Costume10 abril 2025 -
 LX Factory Lisbon: Street Art, Murals, Sunday Markets, Music & Brunch10 abril 2025
LX Factory Lisbon: Street Art, Murals, Sunday Markets, Music & Brunch10 abril 2025 -
nome para colocar princesa do ff|Pesquisa do TikTok10 abril 2025
-
 Desenhos de Unicórnio para pintar e colorir - Blog Ana Giovanna10 abril 2025
Desenhos de Unicórnio para pintar e colorir - Blog Ana Giovanna10 abril 2025 -
 Pokeball PNG - Free Download10 abril 2025
Pokeball PNG - Free Download10 abril 2025 -
 Welcome To The Gaudium - The School Of Joy!10 abril 2025
Welcome To The Gaudium - The School Of Joy!10 abril 2025 -
 COMO COLOCAR ITENS A VENDA E GANHAR MUITOS ROBUX* NO JOGO PLS10 abril 2025
COMO COLOCAR ITENS A VENDA E GANHAR MUITOS ROBUX* NO JOGO PLS10 abril 2025 -
 Payday 3 announced, planned for a 2023 release date10 abril 2025
Payday 3 announced, planned for a 2023 release date10 abril 2025


