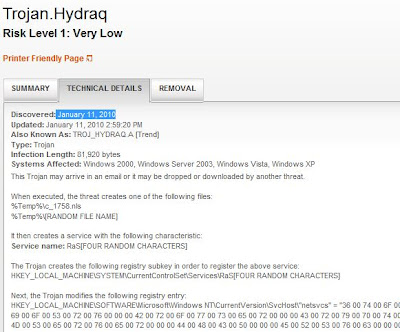
contagio: Trojan.Hydraq detection and naming
Por um escritor misterioso
Last updated 16 abril 2025

PDF) Deep Learning Methods for Malware and Intrusion Detection: A Systematic Literature Review

Avira Labs Research Reveals Hydra Banking Trojan 2.0 targeting a wider network of German and Austrian banks

Cuidado: Uma mensagem de caractere único pode bloquear qualquer Apple iPhone, iPad ou Mac

ThreatExpert Blog: Trojan.Hydraq - Part II
Avira Labs Research Reveals Hydra Banking Trojan 2.0 targeting a wider network of German and Austrian banks

Lecture 11 Malicious Software - ppt download
contagio: February 2010
.jpg)
What Is the Wacatac.B!ml Trojan? How to Remove It From Windows
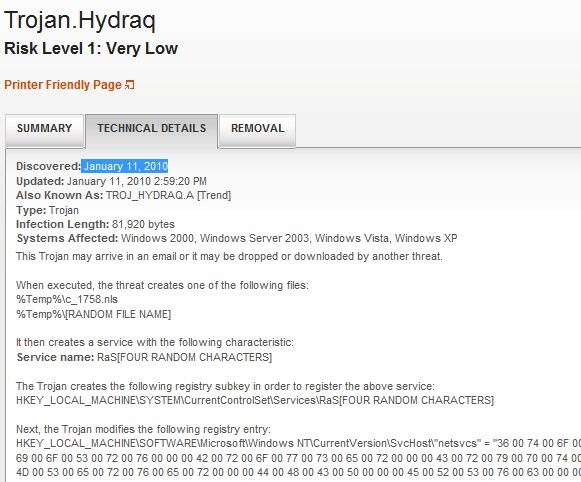
contagio: Trojan.Hydraq detection and naming

A systematic literature review on windows malware detection: Techniques, research issues, and future directions - ScienceDirect

QakBot (Malware Family)

Mal-Detect: An intelligent visualization approach for malware detection - ScienceDirect
Recomendado para você
-
Ikarus antivirus detects this as a Trojan.Win64.CoinMiner · Issue #1620 · baldurk/renderdoc · GitHub16 abril 2025
-
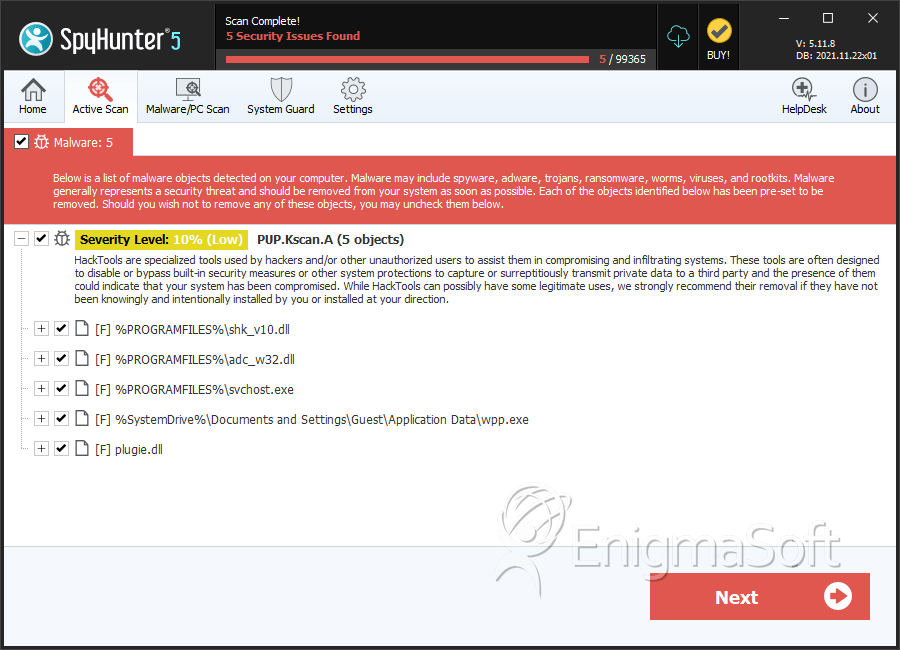 Trojan:Win32/FakeScanti Removal Report16 abril 2025
Trojan:Win32/FakeScanti Removal Report16 abril 2025 -
 malware - Why is my debugger detected as a Trojan by anti-virus software? - Information Security Stack Exchange16 abril 2025
malware - Why is my debugger detected as a Trojan by anti-virus software? - Information Security Stack Exchange16 abril 2025 -
Trojan.Python.Psw · Issue #823 · instaloader/instaloader · GitHub16 abril 2025
-
 Punkston TH61 Keyboard Software contains Trojan : r/MechanicalKeyboards16 abril 2025
Punkston TH61 Keyboard Software contains Trojan : r/MechanicalKeyboards16 abril 2025 -
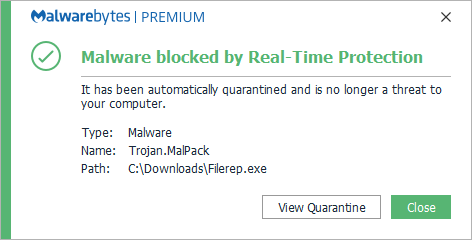 Trojan.Malpack16 abril 2025
Trojan.Malpack16 abril 2025 -
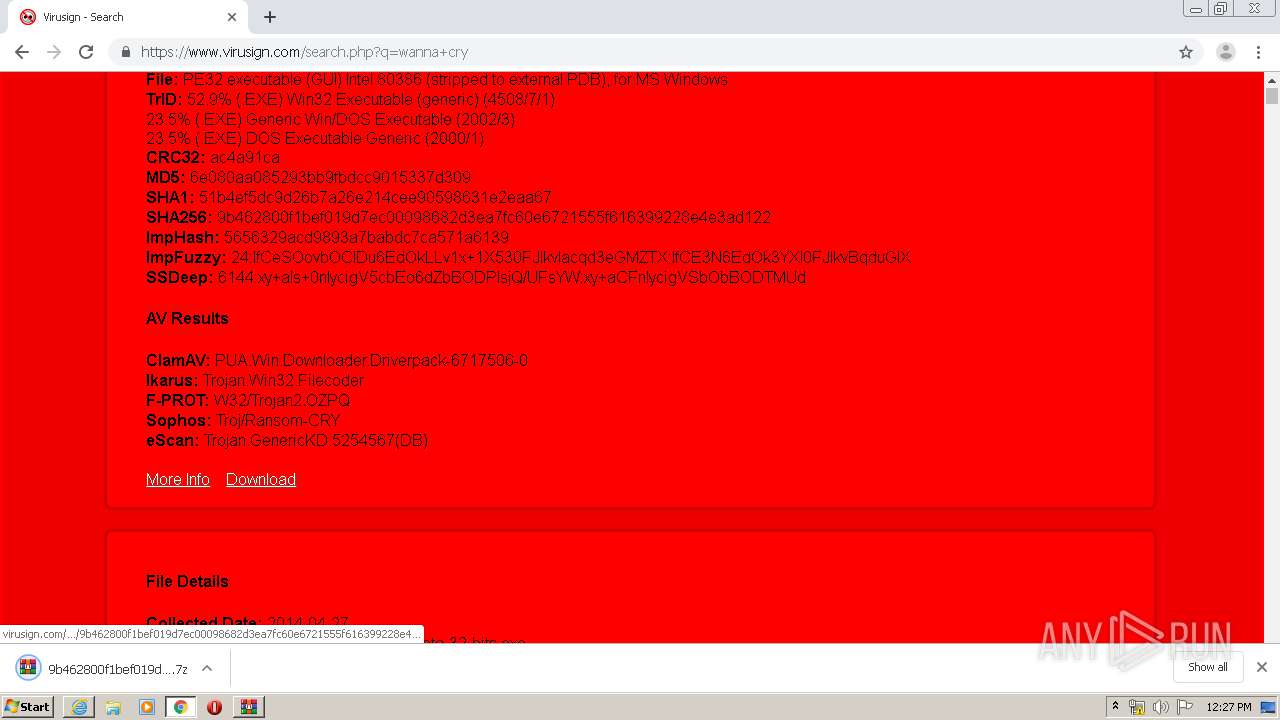 Malware analysis Malicious activity16 abril 2025
Malware analysis Malicious activity16 abril 2025 -
 The contents of the compressed file in B6500360.exe. Analysis 2016 abril 2025
The contents of the compressed file in B6500360.exe. Analysis 2016 abril 2025 -
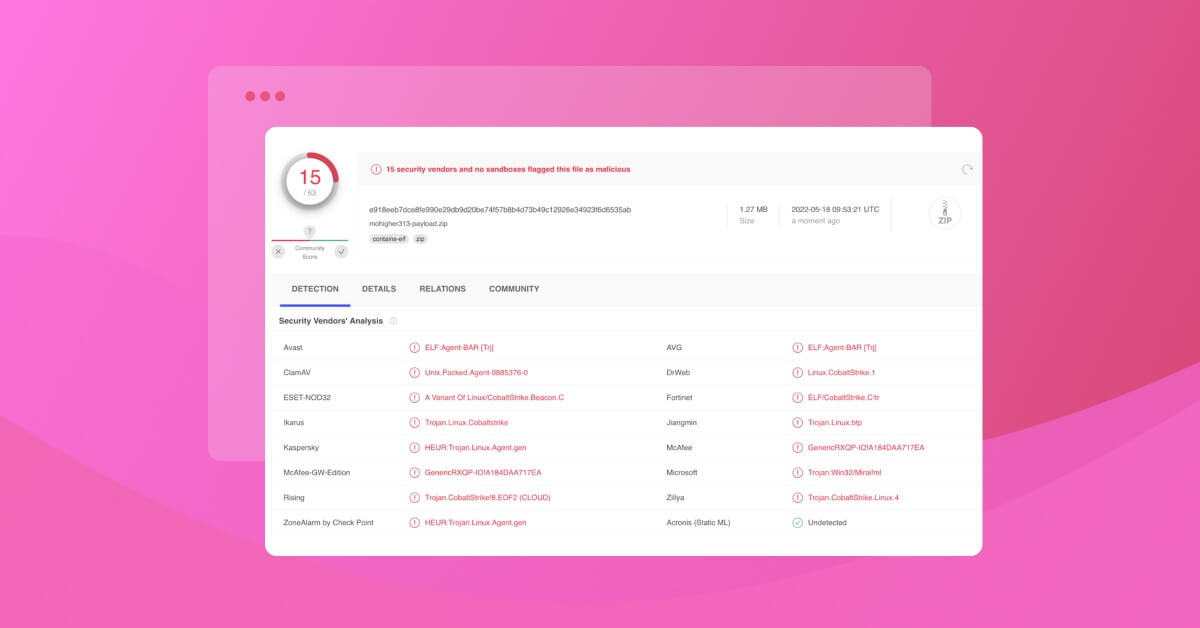 Snyk finds 200+ malicious npm packages, including Cobalt Strike dependency confusion attacks16 abril 2025
Snyk finds 200+ malicious npm packages, including Cobalt Strike dependency confusion attacks16 abril 2025 -
![PDF] Malware Detection and Removal: An examination of personal anti-virus software](https://d3i71xaburhd42.cloudfront.net/3854f4d4217f9340348342f5764e3d6c84779101/4-Table2-1.png) PDF] Malware Detection and Removal: An examination of personal anti-virus software16 abril 2025
PDF] Malware Detection and Removal: An examination of personal anti-virus software16 abril 2025
você pode gostar
-
 ⛏️ 5 Modelos de Casas de Minecraft Simples que Você pode Construir com Facilidade16 abril 2025
⛏️ 5 Modelos de Casas de Minecraft Simples que Você pode Construir com Facilidade16 abril 2025 -
 From Conquest to Tribal Survival in Postindustrial Society - ppt download16 abril 2025
From Conquest to Tribal Survival in Postindustrial Society - ppt download16 abril 2025 -
 Scenarios of Konoha — Kakashi and his reaction to his kid (preferably a16 abril 2025
Scenarios of Konoha — Kakashi and his reaction to his kid (preferably a16 abril 2025 -
 Ghost of Tsushima, Honorable Review, by Jordan “Krunky” Price16 abril 2025
Ghost of Tsushima, Honorable Review, by Jordan “Krunky” Price16 abril 2025 -
 Palmeiras Não Tem Mundial - Single - Album by Mc Mickey Sp & DJ16 abril 2025
Palmeiras Não Tem Mundial - Single - Album by Mc Mickey Sp & DJ16 abril 2025 -
 Cartas da Mestra Pórtia: Chohan do Raio Violeta da Grande Fraternidade Branca (Cartas dos Mestres Ascensos Livro 1) (Portuguese Edition) eBook : Martini, Michele: Kindle Store16 abril 2025
Cartas da Mestra Pórtia: Chohan do Raio Violeta da Grande Fraternidade Branca (Cartas dos Mestres Ascensos Livro 1) (Portuguese Edition) eBook : Martini, Michele: Kindle Store16 abril 2025 -
 Ishowspeed Tank Tops - ishowspeed barking shitpost meme merch Tank Top RB1312 | Ishowspeed Merch16 abril 2025
Ishowspeed Tank Tops - ishowspeed barking shitpost meme merch Tank Top RB1312 | Ishowspeed Merch16 abril 2025 -
 Los sets LEGO Harry Potter 2024 revisan el concepto coleccionable16 abril 2025
Los sets LEGO Harry Potter 2024 revisan el concepto coleccionable16 abril 2025 -
 Prime Gaming Launched In India: FIFA 23, Destiny 2, More Games Available For Free16 abril 2025
Prime Gaming Launched In India: FIFA 23, Destiny 2, More Games Available For Free16 abril 2025 -
 Movie Wonder Woman: Bloodlines 4k Ultra HD Wallpaper16 abril 2025
Movie Wonder Woman: Bloodlines 4k Ultra HD Wallpaper16 abril 2025