Windows JavaScript zero-day, Iran-based hack-and-leak, METRO
Por um escritor misterioso
Last updated 16 janeiro 2025

Exploited Windows zero-day lets JavaScript files bypass Mark of the Web security warnings According to Bleeping Computer, this has already been seen in ransomware attacks. Windows includes a security feature called Mark-of-the-Web (MoTW) that flags a file as having been downloaded from the Internet

Consequential, a policy podcast from Carnegie Mellon University

The Cyber Cold War: How Russia is Using Cyber Attacks as a Weapon in Geopolitics – International Defense Security & Technology

CISA Warns of Russian Hackers Targeting JetBrains TeamCity Software Ad

Ethical hacking for IoT: Security issues, challenges, solutions and recommendations - ScienceDirect

Signal >> Blog
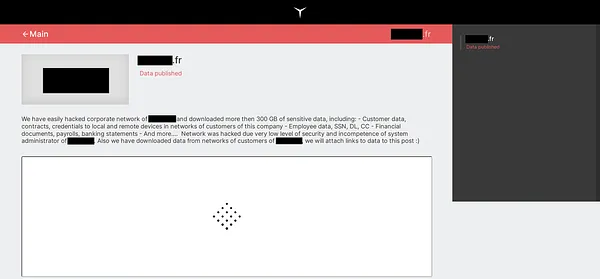
Risky Biz News: China faces its first truly mega-leak

The Anomali Blog

Cybercrime and cyber conflicts: Russia
The IT Governance Podcast
Windows JavaScript zero-day, Iran hack-and-leak, METRO retailer attack

Webinars Archives - DarkOwl, LLC
Recomendado para você
-
Hacker's Keyboard - Apps on Google Play16 janeiro 2025
-
robloxscripts · GitHub Topics · GitHub16 janeiro 2025
-
 Roblox Studio: The Get Started Guide - Create & Learn16 janeiro 2025
Roblox Studio: The Get Started Guide - Create & Learn16 janeiro 2025 -
 how to HACK in Arsenal (Arsenal Roblox)16 janeiro 2025
how to HACK in Arsenal (Arsenal Roblox)16 janeiro 2025 -
 The Complete 2023 Roblox Studio Masterclass16 janeiro 2025
The Complete 2023 Roblox Studio Masterclass16 janeiro 2025 -
/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2022/Q/S/qI5Ax6RRSodwLvzMHIfQ/capa-celular-cirotta-01.jpg) Capa anti-espionagem para celular também evita ataques hackers16 janeiro 2025
Capa anti-espionagem para celular também evita ataques hackers16 janeiro 2025 -
 Hackers exploit Roblox's scripting engine to install Trojan16 janeiro 2025
Hackers exploit Roblox's scripting engine to install Trojan16 janeiro 2025 -
 Listen to Hacked podcast16 janeiro 2025
Listen to Hacked podcast16 janeiro 2025 -
 The trouble with Roblox, the video game empire built on child labour, Games16 janeiro 2025
The trouble with Roblox, the video game empire built on child labour, Games16 janeiro 2025 -
 The trouble with Roblox, the video game empire built on child16 janeiro 2025
The trouble with Roblox, the video game empire built on child16 janeiro 2025
você pode gostar
-
 Lance Reddick : Melhores filmes e séries - AdoroCinema16 janeiro 2025
Lance Reddick : Melhores filmes e séries - AdoroCinema16 janeiro 2025 -
 One-Punch Man: Season 2 (BD)16 janeiro 2025
One-Punch Man: Season 2 (BD)16 janeiro 2025 -
 Player's menthol move16 janeiro 2025
Player's menthol move16 janeiro 2025 -
 Classic Characters Who Can Return In Street Fighter 616 janeiro 2025
Classic Characters Who Can Return In Street Fighter 616 janeiro 2025 -
 Call of Duty: WWII Review16 janeiro 2025
Call of Duty: WWII Review16 janeiro 2025 -
Raul Livros Santa Bárbara d'Oeste SP16 janeiro 2025
-
 Friends! Fleetway super sonic and sonic (STC + IDW AU) : r/SonicTheHedgehog16 janeiro 2025
Friends! Fleetway super sonic and sonic (STC + IDW AU) : r/SonicTheHedgehog16 janeiro 2025 -
 Llama Amigos Large Canvas Organizer Bag by Contemporary Artist Two16 janeiro 2025
Llama Amigos Large Canvas Organizer Bag by Contemporary Artist Two16 janeiro 2025 -
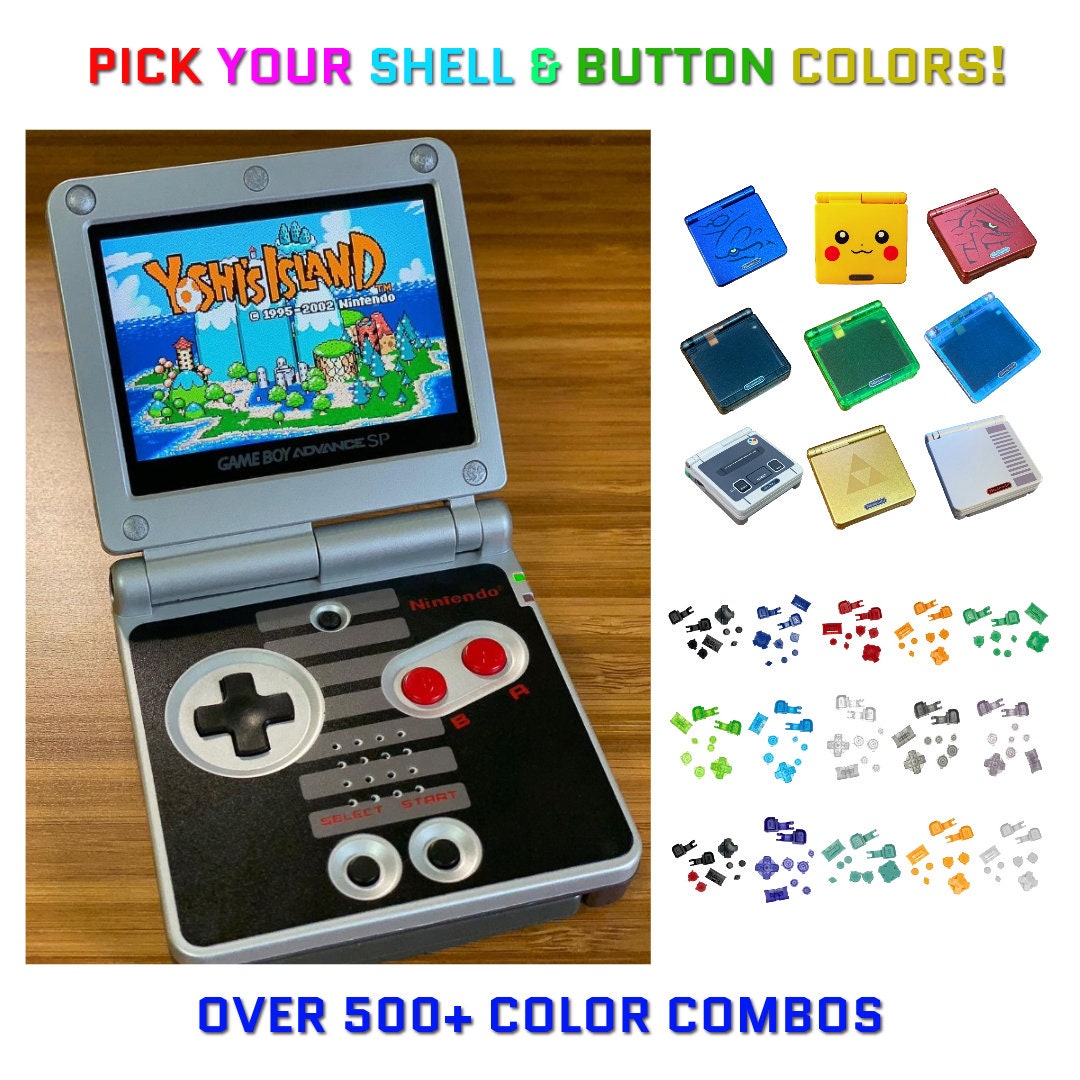 Nintendo Game Boy Advance GBA SP IPS Mod System 10 Levels16 janeiro 2025
Nintendo Game Boy Advance GBA SP IPS Mod System 10 Levels16 janeiro 2025 -
 Create Stunning Instagram Stories & Carousels with Social Design App from Fundy Designer16 janeiro 2025
Create Stunning Instagram Stories & Carousels with Social Design App from Fundy Designer16 janeiro 2025
