Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
Por um escritor misterioso
Last updated 13 abril 2025
Did you know that the Secure Shell protocol, better known as SSH, is not as secure as its name suggests? In this post I show you different ways to attack this protocol. %

Explained: The Tinyman Hack (January 2022)
Lazarus Group Using Log4j Exploits to Deploy Remote Access Trojans #hacker # hacking #cyberaware 👨💻

Iranian hacker claims he acted alone in stealing digital SSL certificates, Hacking

Understanding Linux Privilege Escalation: Tips to Improve Cy

Linux Challenges - Cyber Security / Ethical Hacking

Playing with FHIR? Don't get burned, white-hat hacker cautions

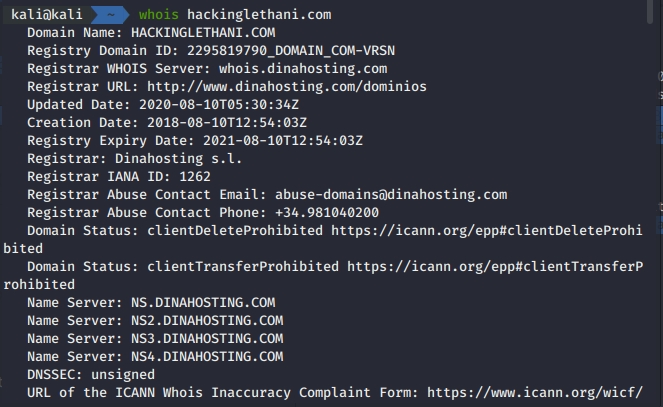
Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
Tips for Investigating Cybercrime Infrastructure
Ethical Hacking - How to start

Anonymous Claims It Hacked Everything From Nazis' Favorite Web Host
Recomendado para você
-
Quick Domain WHOIS13 abril 2025
-
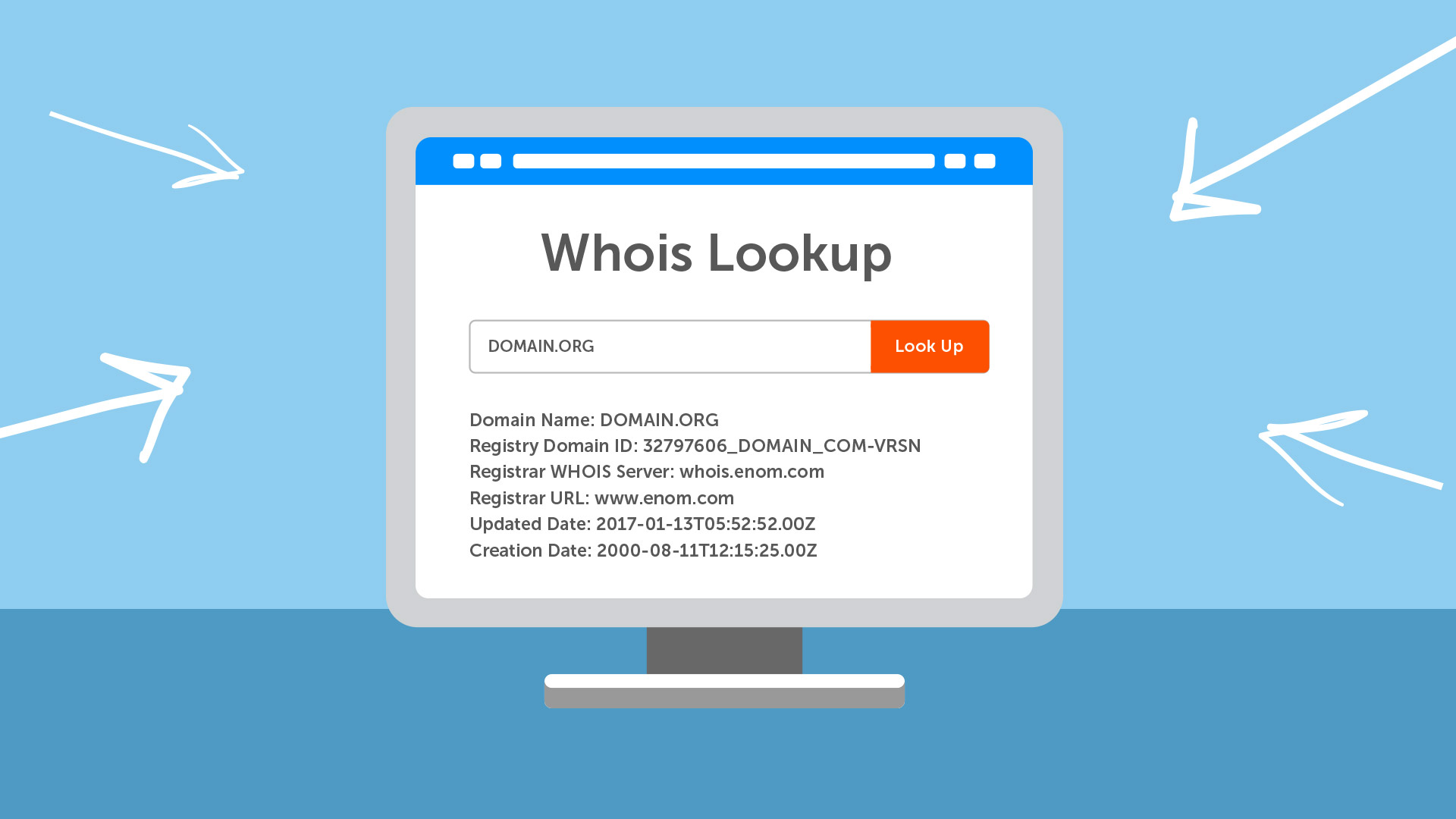 The WHOIS Database13 abril 2025
The WHOIS Database13 abril 2025 -
Find Out Who Owns a Domain with WHOIS Lookup13 abril 2025
-
 WHOIS Domain Lookup - WHMCS Marketplace13 abril 2025
WHOIS Domain Lookup - WHMCS Marketplace13 abril 2025 -
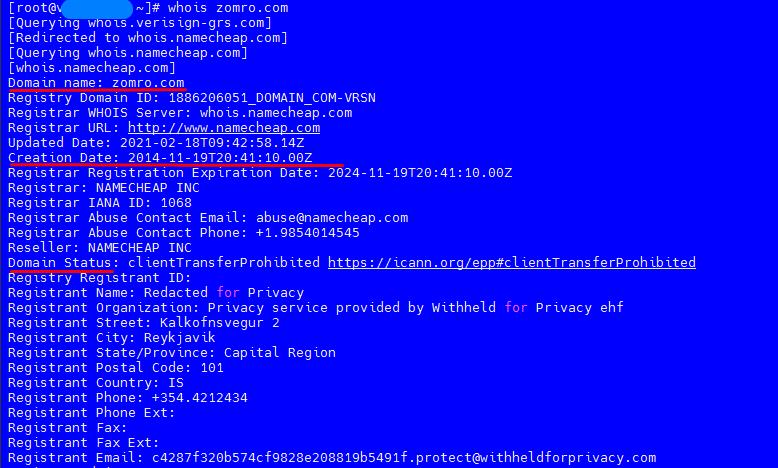 How to see whois of a domain13 abril 2025
How to see whois of a domain13 abril 2025 -
 Domain Privacy and WHOIS Lookup Explained13 abril 2025
Domain Privacy and WHOIS Lookup Explained13 abril 2025 -
Whois powers global expansion with OCI's scalability and performance13 abril 2025
-
 WHOIS Lookup Tool – Find Out Who Owns a Domain13 abril 2025
WHOIS Lookup Tool – Find Out Who Owns a Domain13 abril 2025 -
 Whois.net - Crunchbase Company Profile & Funding13 abril 2025
Whois.net - Crunchbase Company Profile & Funding13 abril 2025 -
Whois Icon13 abril 2025
você pode gostar
-
 Wallpaper : The Last of Us, The Last of Us 2 1920x1080 - JustJon - 1922415 - HD Wallpapers - WallHere13 abril 2025
Wallpaper : The Last of Us, The Last of Us 2 1920x1080 - JustJon - 1922415 - HD Wallpapers - WallHere13 abril 2025 -
 The Kenilworthian: Five Easy Pieces: White Open Sicilian Repertoire13 abril 2025
The Kenilworthian: Five Easy Pieces: White Open Sicilian Repertoire13 abril 2025 -
 Marvel's Spider-Man Remastered chegará ao PC em agosto13 abril 2025
Marvel's Spider-Man Remastered chegará ao PC em agosto13 abril 2025 -
 There goes my Hero, he's ordinary - My Hero | Foo Fighters Song | Home Print13 abril 2025
There goes my Hero, he's ordinary - My Hero | Foo Fighters Song | Home Print13 abril 2025 -
 Redneck Woman (tradução) - Gretchen Wilson - VAGALUME13 abril 2025
Redneck Woman (tradução) - Gretchen Wilson - VAGALUME13 abril 2025 -
 Apresentação da Peça Roblox no Teatro Municipal - FundArt13 abril 2025
Apresentação da Peça Roblox no Teatro Municipal - FundArt13 abril 2025 -
 Seek MBTI Personality Type: INTJ or INTP?13 abril 2025
Seek MBTI Personality Type: INTJ or INTP?13 abril 2025 -
 86 EIGHTY-SIX: Crunchyroll anuncia dublagem do anime – ANMTV13 abril 2025
86 EIGHTY-SIX: Crunchyroll anuncia dublagem do anime – ANMTV13 abril 2025 -
 The one game I would love to have backwards compatability with13 abril 2025
The one game I would love to have backwards compatability with13 abril 2025 -
 alan becker gaming,funny alan becker gaming s | Art Board Print13 abril 2025
alan becker gaming,funny alan becker gaming s | Art Board Print13 abril 2025
