Transforming Self-XSS Into Exploitable XSS
Por um escritor misterioso
Last updated 07 abril 2025

This blog is describes an attempt by a security researcher to exploit a Cross-site Scripting (XSS) vulnerability. It explains the importance of template strings in XSS filtering, how to overcome the document.domain issue, and the discovery and exploitation of Self-XSS, with reading suggestions.
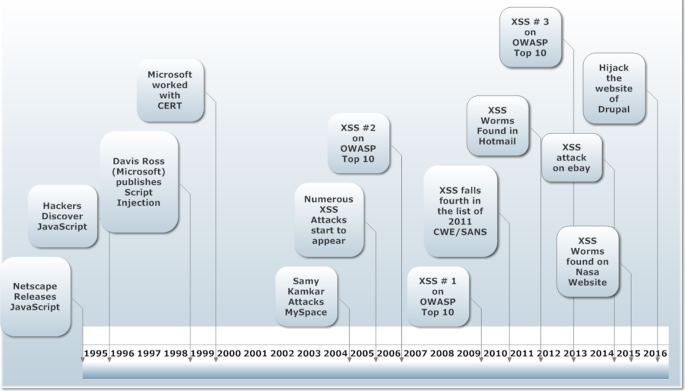
Evaluation and monitoring of XSS defensive solutions: a survey, open research issues and future directions
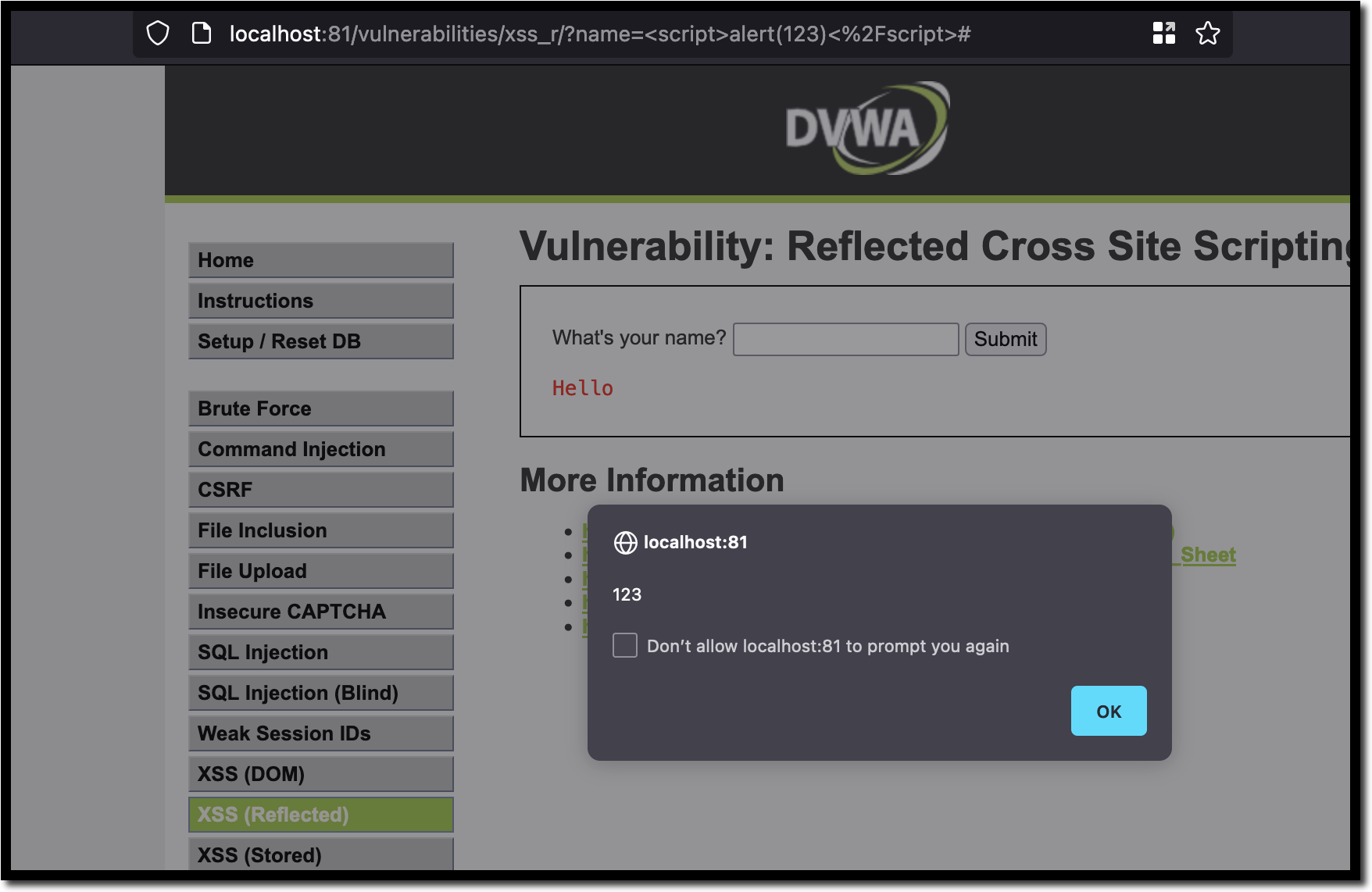
10 Practical scenarios for XSS attacks
Cross-Site Scripting (XSS) Attack in Modern Frontend Web, by Héla Ben Khalfallah
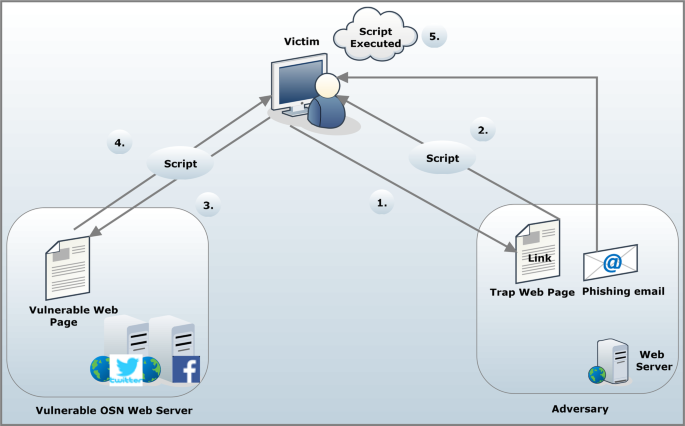
Evaluation and monitoring of XSS defensive solutions: a survey, open research issues and future directions
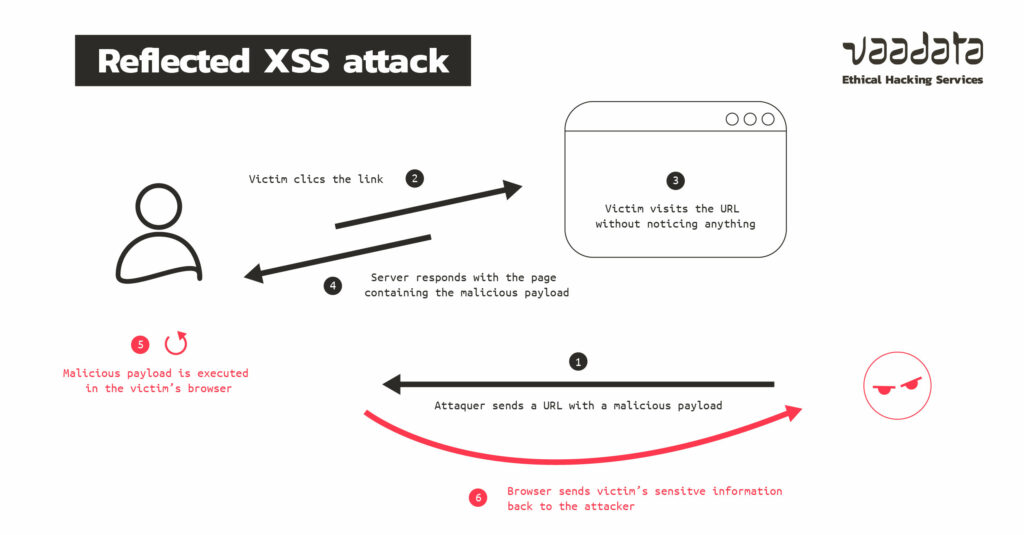
XSS: Principles, Attacks and Security Best Practices
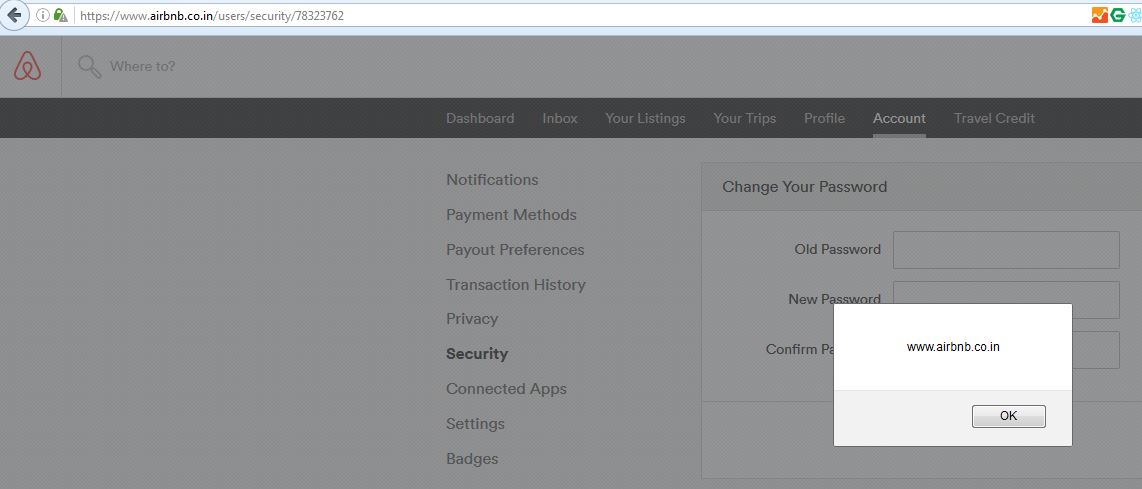
AirBnb Bug Bounty: Turning Self-XSS into Good-XSS #2, Geekboy
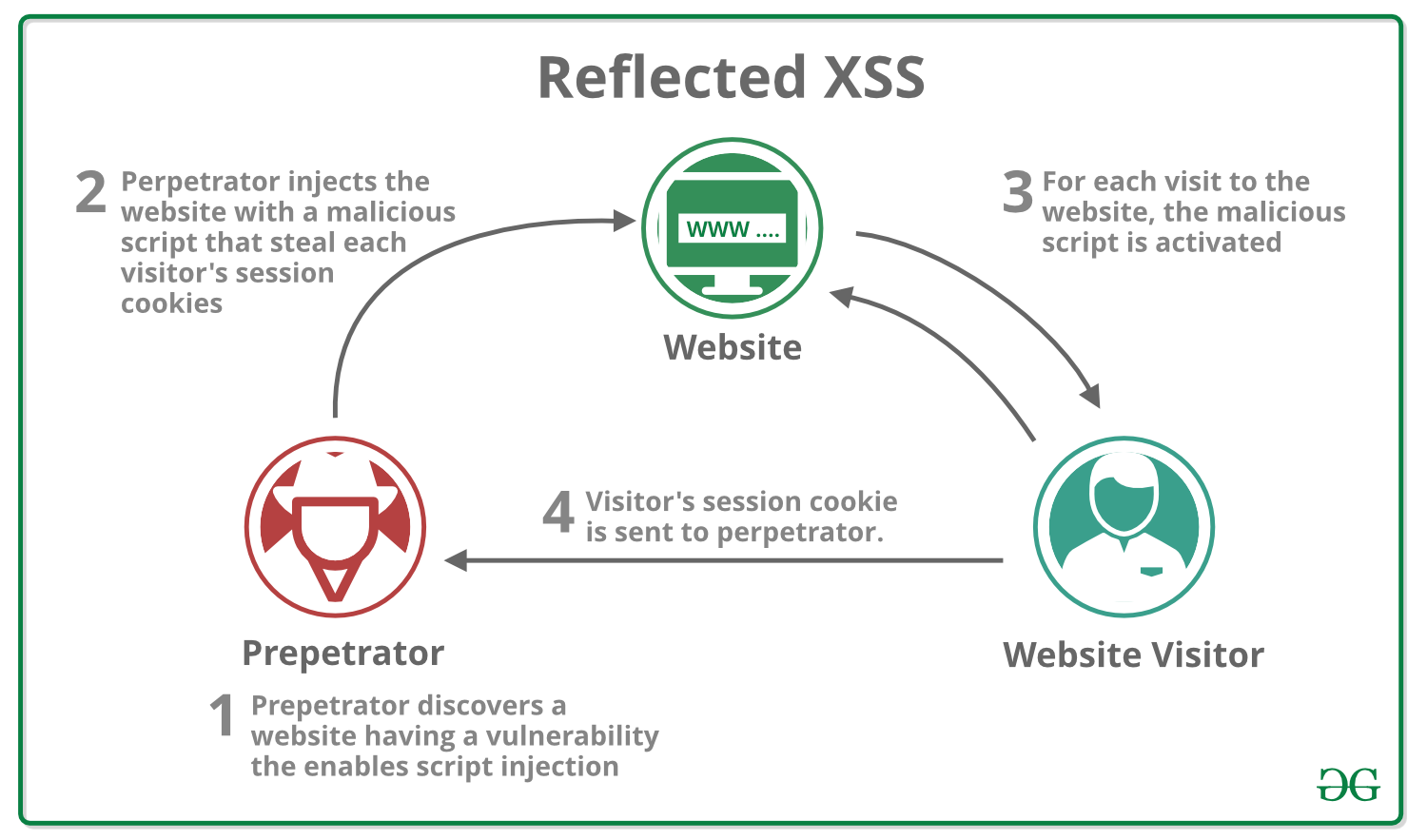
What is Cross Site Scripting (XSS) ? - GeeksforGeeks
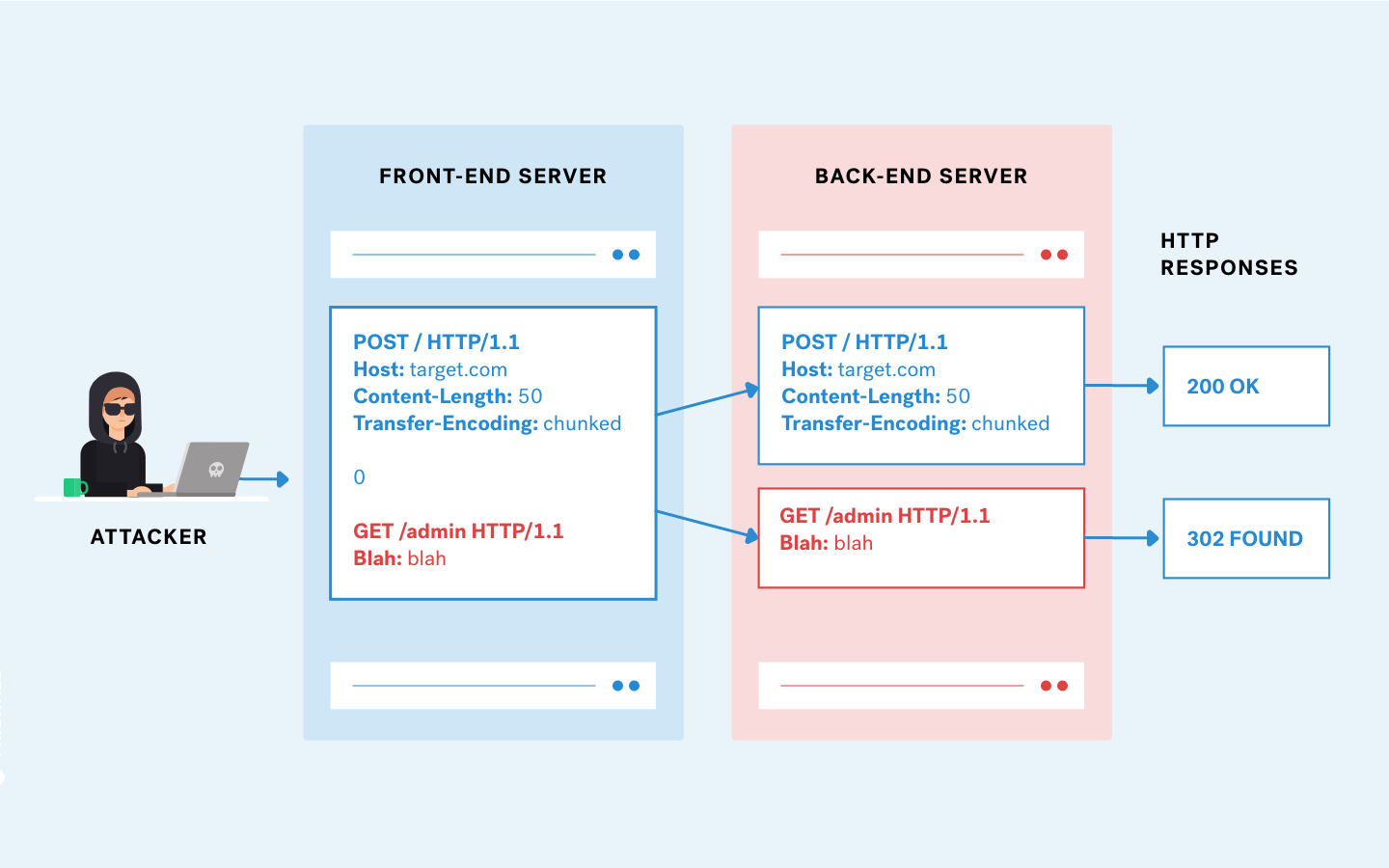
A Pentester's Guide to Cross-Site Scripting (XSS)

What is a Cross-Site Scripting (XSS) attack: Definition & Examples
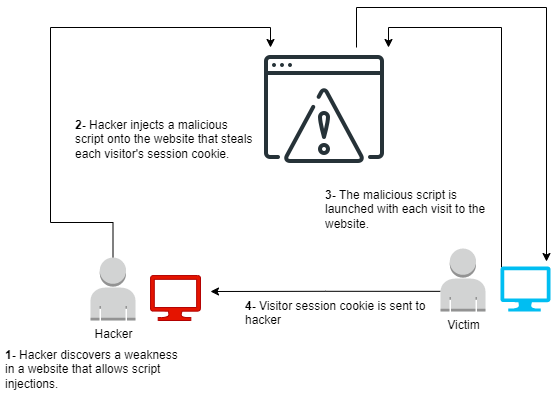
What is Cross-Site Scripting (XSS) Reflected Self Vulnerability?

Self XSS to Account Takeover. Exploiting Self Stored XSS to escalate…, by Ch3ckM4te
5 Real-World Cross Site Scripting Examples
Recomendado para você
-
 Cross Site Scripting (XSS) - Payload Generator07 abril 2025
Cross Site Scripting (XSS) - Payload Generator07 abril 2025 -
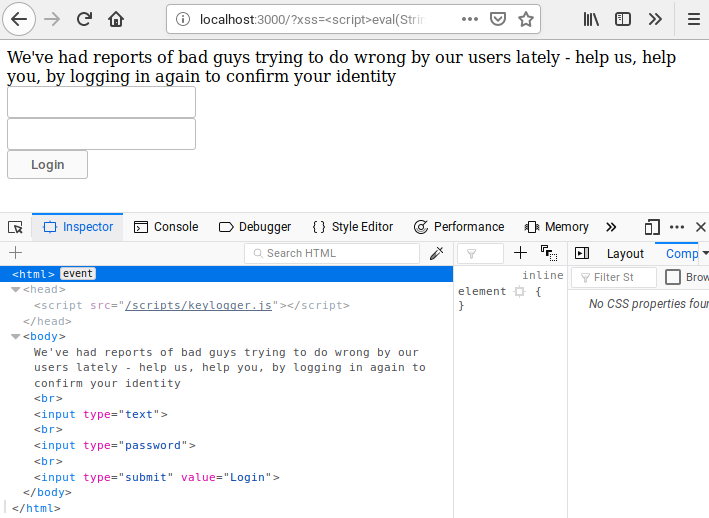 A Deeper Look into XSS Payloads07 abril 2025
A Deeper Look into XSS Payloads07 abril 2025 -
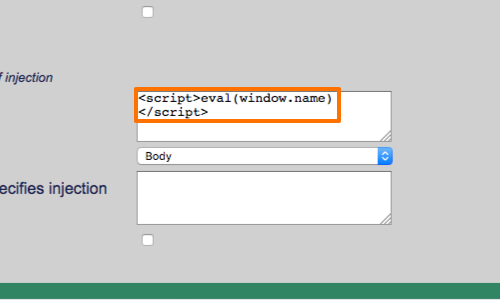 XSS Filters: Beating Length Limits Using Shortened Payloads07 abril 2025
XSS Filters: Beating Length Limits Using Shortened Payloads07 abril 2025 -
PayloadsAllTheThings/XSS Injection/README.md at master07 abril 2025
-
GitHub - XSSPayloads/XSS: XSS Payloads07 abril 2025
-
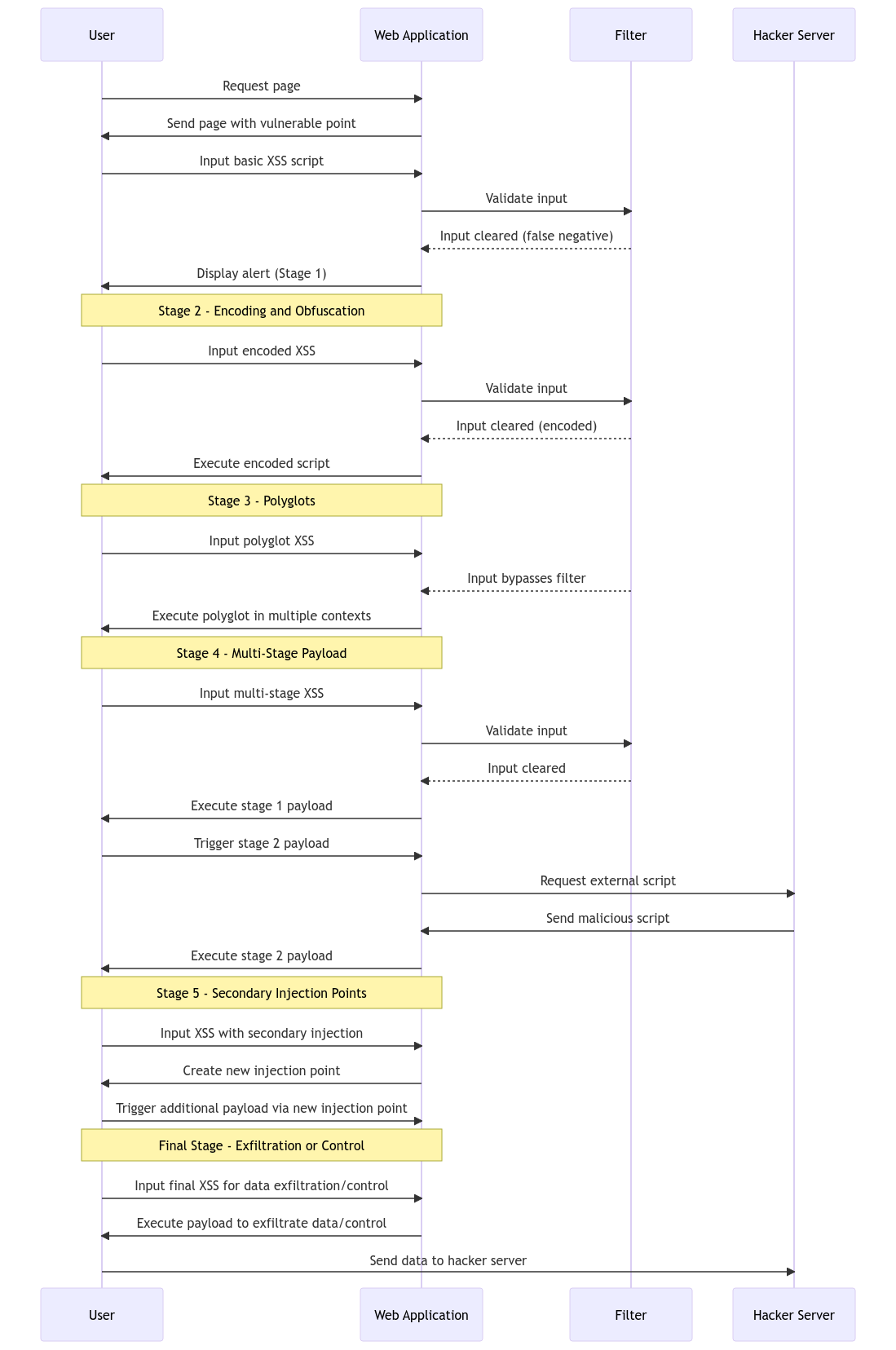 Decoding Advanced XSS Payload Chaining Tactics07 abril 2025
Decoding Advanced XSS Payload Chaining Tactics07 abril 2025 -
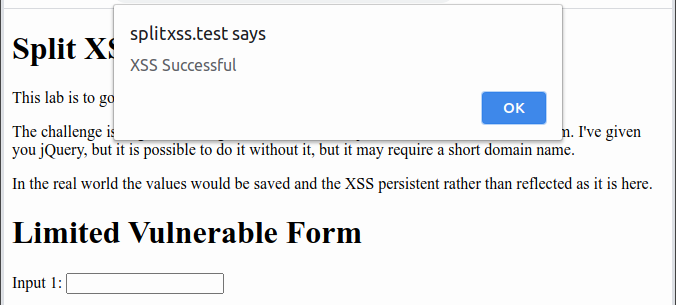 Split XSS - DigiNinja07 abril 2025
Split XSS - DigiNinja07 abril 2025 -
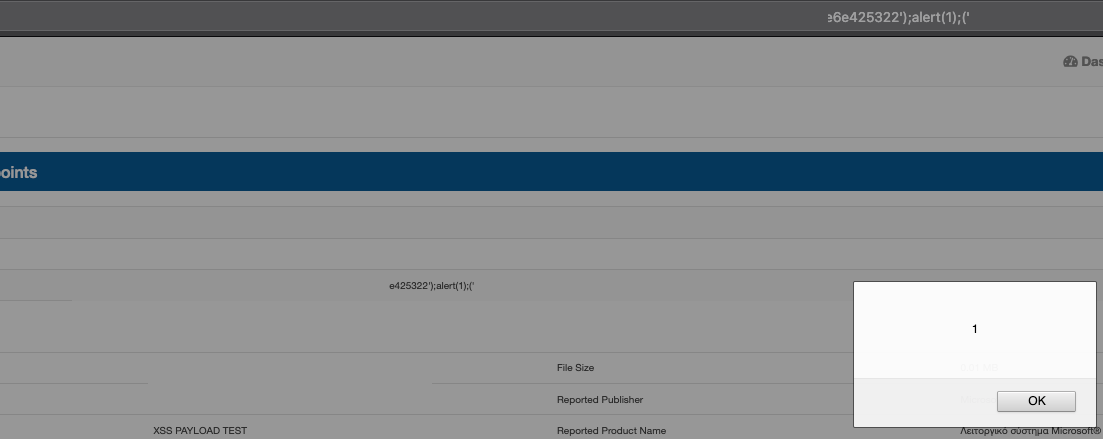 XSS Via XML Value Processing. XXE is not the only vulnerability07 abril 2025
XSS Via XML Value Processing. XXE is not the only vulnerability07 abril 2025 -
 What is a cross-site scripting vulnerability?07 abril 2025
What is a cross-site scripting vulnerability?07 abril 2025 -
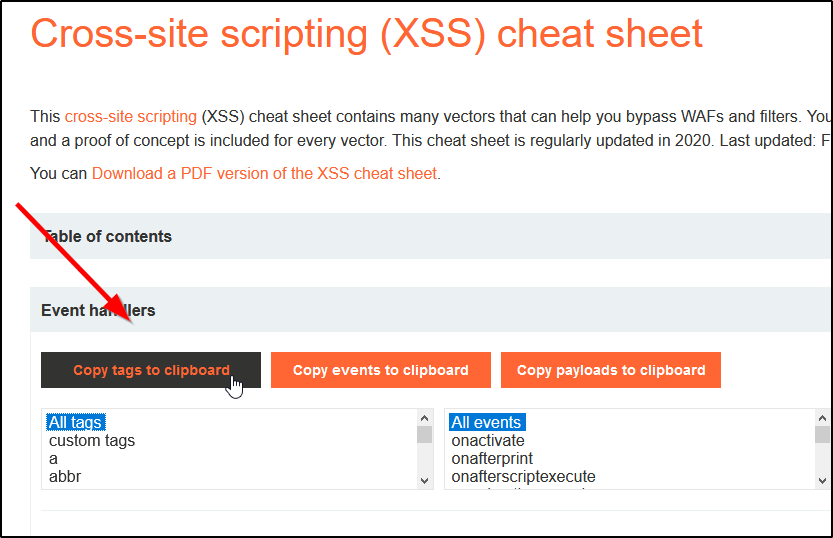 XSS Infinite Logins07 abril 2025
XSS Infinite Logins07 abril 2025
você pode gostar
-
 A História e a filosofia da ciência no ensino de ciências A07 abril 2025
A História e a filosofia da ciência no ensino de ciências A07 abril 2025 -
 Fandom - A Round Trip Across the Multiverse: Characters07 abril 2025
Fandom - A Round Trip Across the Multiverse: Characters07 abril 2025 -
 Dragonslayer - Rotten Tomatoes07 abril 2025
Dragonslayer - Rotten Tomatoes07 abril 2025 -
 Baby Ant Gets Lost and Exhausted07 abril 2025
Baby Ant Gets Lost and Exhausted07 abril 2025 -
 The Promised Neverland – Manga Mate07 abril 2025
The Promised Neverland – Manga Mate07 abril 2025 -
 Neil Druckmann - Petitions & Information - ·07 abril 2025
Neil Druckmann - Petitions & Information - ·07 abril 2025 -
 Obito and madara, naruto, shinobi, HD wallpaper07 abril 2025
Obito and madara, naruto, shinobi, HD wallpaper07 abril 2025 -
 What is the correct size for a thumbnail? - Art Design Support - Developer Forum07 abril 2025
What is the correct size for a thumbnail? - Art Design Support - Developer Forum07 abril 2025 -
 Recompensas dos Jogos do Clã – 23 à 29 de Junho/2020 - Clash of07 abril 2025
Recompensas dos Jogos do Clã – 23 à 29 de Junho/2020 - Clash of07 abril 2025 -
 Video Game Five Nights at Freddy's 4 4k Ultra HD Wallpaper07 abril 2025
Video Game Five Nights at Freddy's 4 4k Ultra HD Wallpaper07 abril 2025