Threats & Research Archives - F-Secure Blog
Por um escritor misterioso
Last updated 02 abril 2025


Blogs - Orpheus Cyber

BATLOADER: The Evasive Downloader Malware – VMware Security Blog

Cyble — Threat Actor Employs PowerShell-Backed Steganography in
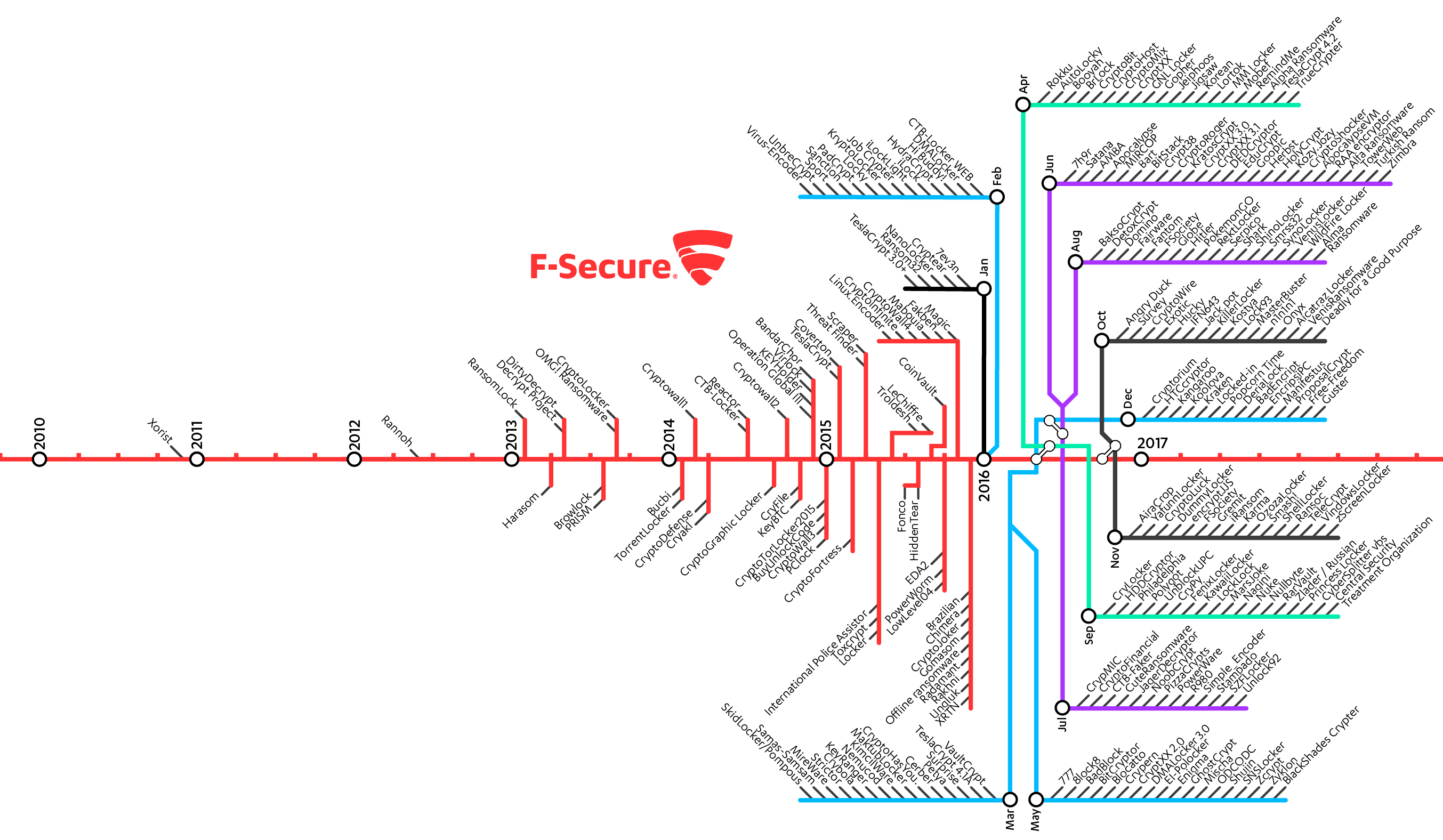
Ransomware Timeline: 2010 – 2017 - F-Secure Blog

Technical Documentation Archives - Palo Alto Networks Blog

Research Blog - Following the people and events that make up the

Behind the scenes of business email compromise: Using cross-domain

Compromised Microsoft Key: More Impactful Than We Thought

Threat Insight Information & Resources
Recomendado para você
-
 Hacker Typer Pro - Prank App on the App Store02 abril 2025
Hacker Typer Pro - Prank App on the App Store02 abril 2025 -
![web-app] GeekTyper+ - An Awesome Hacking Prank by fediaFedia on DeviantArt](https://images-wixmp-ed30a86b8c4ca887773594c2.wixmp.com/f/9a1e44ad-d8a6-484b-91a3-ccc9c064e06b/d89qfjh-6261d898-bc08-492d-9900-bd4112a2b800.png?token=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJ1cm46YXBwOjdlMGQxODg5ODIyNjQzNzNhNWYwZDQxNWVhMGQyNmUwIiwiaXNzIjoidXJuOmFwcDo3ZTBkMTg4OTgyMjY0MzczYTVmMGQ0MTVlYTBkMjZlMCIsIm9iaiI6W1t7InBhdGgiOiJcL2ZcLzlhMWU0NGFkLWQ4YTYtNDg0Yi05MWEzLWNjYzljMDY0ZTA2YlwvZDg5cWZqaC02MjYxZDg5OC1iYzA4LTQ5MmQtOTkwMC1iZDQxMTJhMmI4MDAucG5nIn1dXSwiYXVkIjpbInVybjpzZXJ2aWNlOmZpbGUuZG93bmxvYWQiXX0.oUIGTa07W9kPsvJkQrQRmybs3Sg2UuirmS2sC-R3Ilg) web-app] GeekTyper+ - An Awesome Hacking Prank by fediaFedia on DeviantArt02 abril 2025
web-app] GeekTyper+ - An Awesome Hacking Prank by fediaFedia on DeviantArt02 abril 2025 -
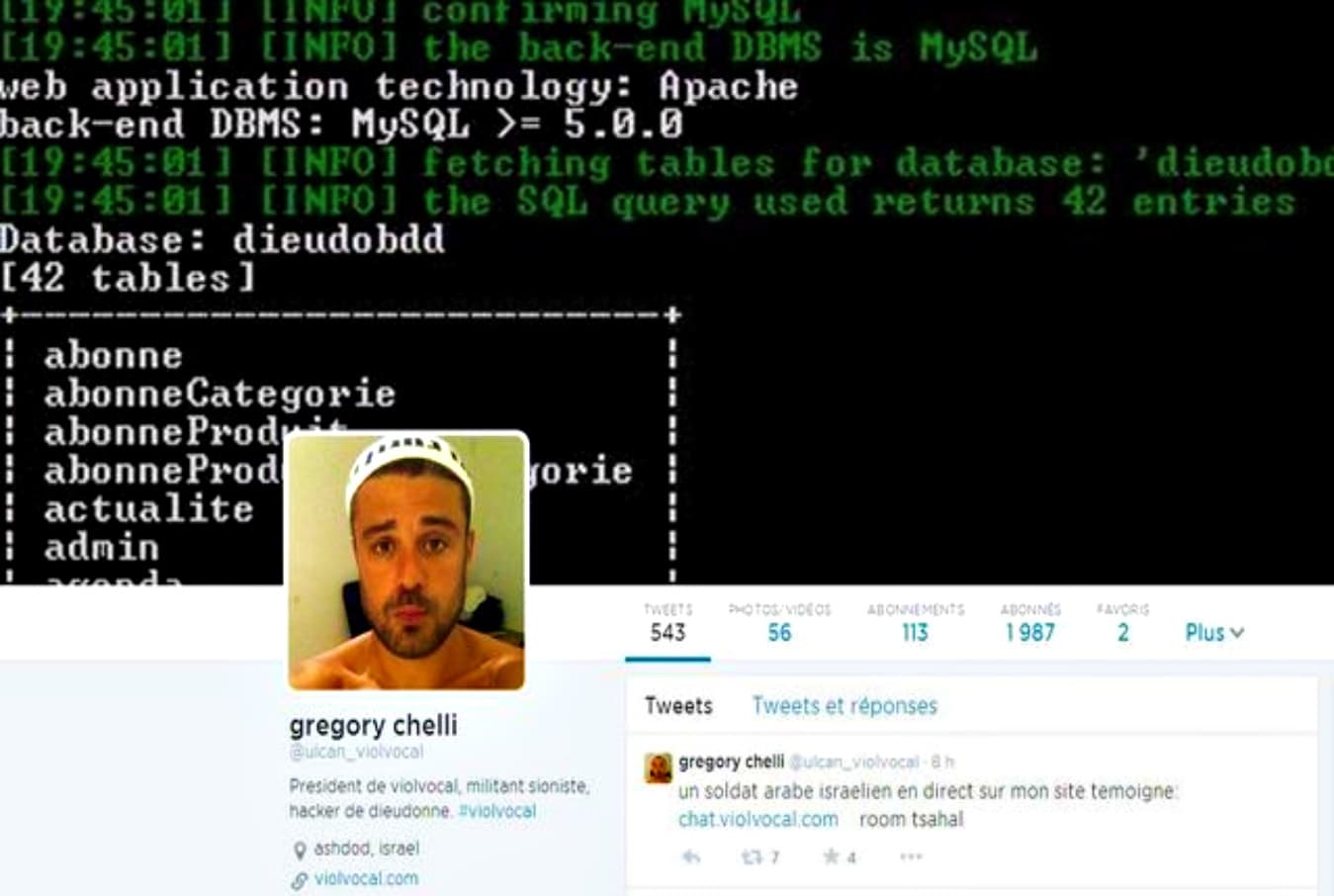 Death linked to prank - France seeks extradition of hacker from Israel02 abril 2025
Death linked to prank - France seeks extradition of hacker from Israel02 abril 2025 -
 Hacker text animations plugin Universe Hacker Text by Maxon02 abril 2025
Hacker text animations plugin Universe Hacker Text by Maxon02 abril 2025 -
 What is Anonymous? The group went from 4chan to cyberattacks on Russia02 abril 2025
What is Anonymous? The group went from 4chan to cyberattacks on Russia02 abril 2025 -
 Anonymous Indonesia' Launches Cyber Attack on Government Sites02 abril 2025
Anonymous Indonesia' Launches Cyber Attack on Government Sites02 abril 2025 -
 WordPress Website Hacked? We'll Show You What to Do Next02 abril 2025
WordPress Website Hacked? We'll Show You What to Do Next02 abril 2025 -
 Hacking is a Mindset, Not a Skillset: Why civic hacking is key for contemporary creativity.02 abril 2025
Hacking is a Mindset, Not a Skillset: Why civic hacking is key for contemporary creativity.02 abril 2025 -
:format(jpg)/cloudfront-us-east-1.images.arcpublishing.com/coindesk/CRPSIVI225EMZL6F5P4MHD5SNA.jpg) The Art of the Prank: How a Hacker Tried to Fake the World's Most Expensive NFT - CoinDesk02 abril 2025
The Art of the Prank: How a Hacker Tried to Fake the World's Most Expensive NFT - CoinDesk02 abril 2025 -
:format(jpg)/cloudfront-us-east-1.images.arcpublishing.com/coindesk/CRPSIVI225EMZL6F5P4MHD5SNA.jpg) The Art of the Prank: How a Hacker Tried to Fake the World's Most02 abril 2025
The Art of the Prank: How a Hacker Tried to Fake the World's Most02 abril 2025
você pode gostar
-
 Shimano BB-MT800 Pressfit Bottom Bracket02 abril 2025
Shimano BB-MT800 Pressfit Bottom Bracket02 abril 2025 -
Steam 工作坊::Five Nights at Freddy's 1 Stylized Map!02 abril 2025
-
 Moto Moto, Madagascar Wiki02 abril 2025
Moto Moto, Madagascar Wiki02 abril 2025 -
RandomGuy1237's Profile02 abril 2025
-
 Com estreia em Derby, colombiano Angulo se torna o 113º estrangeiro a jogar pelo Verdão – Palmeiras02 abril 2025
Com estreia em Derby, colombiano Angulo se torna o 113º estrangeiro a jogar pelo Verdão – Palmeiras02 abril 2025 -
 Monster Trucks RAM Rebel #1 by DipperBronyPines98 on DeviantArt02 abril 2025
Monster Trucks RAM Rebel #1 by DipperBronyPines98 on DeviantArt02 abril 2025 -
 How to Run a PowerShell Script ITPro Today: IT News, How-Tos02 abril 2025
How to Run a PowerShell Script ITPro Today: IT News, How-Tos02 abril 2025 -
 Análise De volta ao paraíso da destruição em Burnout Paradise02 abril 2025
Análise De volta ao paraíso da destruição em Burnout Paradise02 abril 2025 -
 Scp-3008 roblox - iFunny Brazil02 abril 2025
Scp-3008 roblox - iFunny Brazil02 abril 2025 -
 Characters appearing in Love, Chunibyo & Other Delusions! Movie: Take On Me Anime02 abril 2025
Characters appearing in Love, Chunibyo & Other Delusions! Movie: Take On Me Anime02 abril 2025

