Google Vulnerability Rewards Program, XSS, Best Practices
Por um escritor misterioso
Last updated 19 outubro 2024
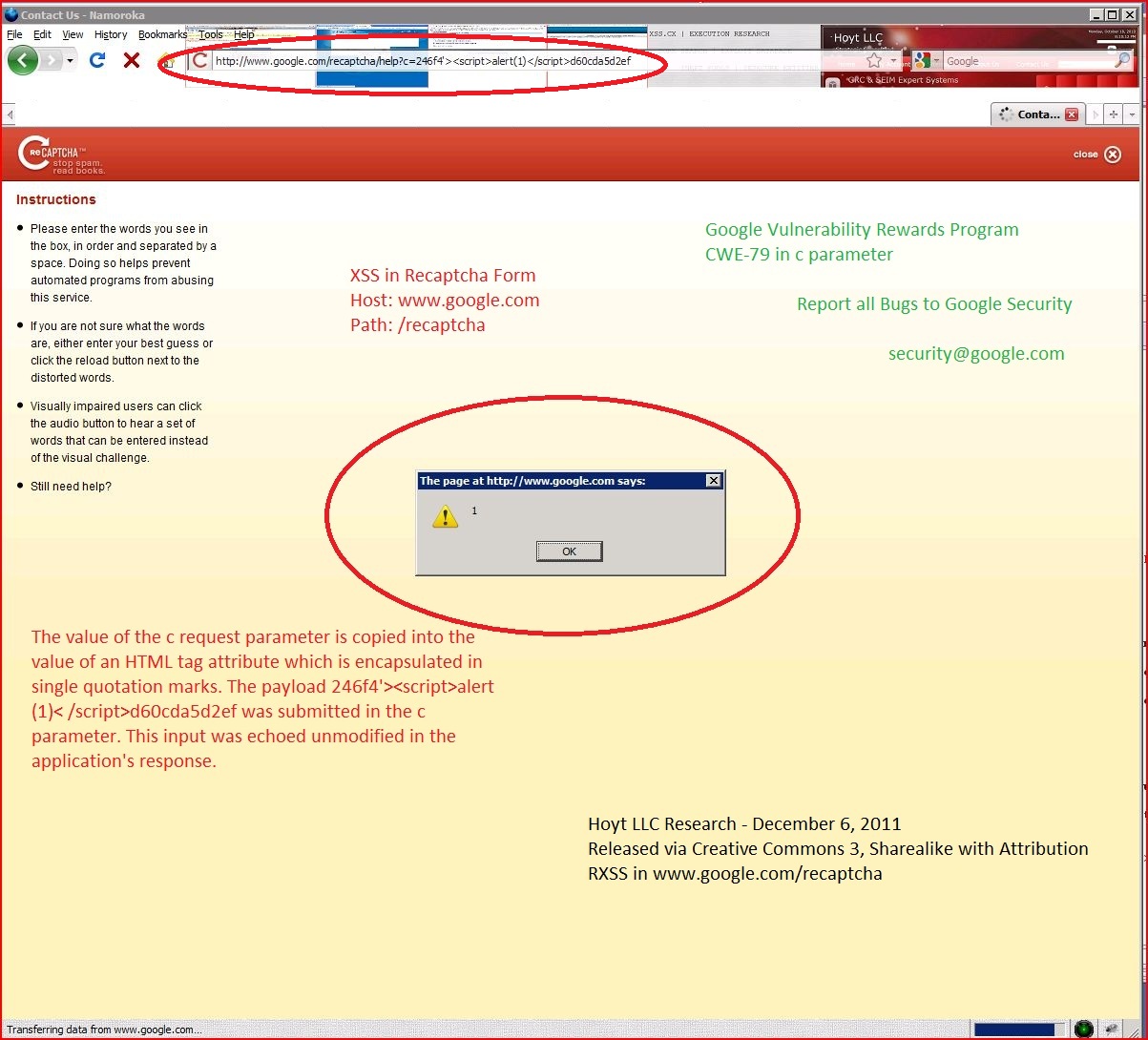
Phishing, Insecure Configuration, XSS, Cross Site Scripting, Best Practices, Vulnerability Management, Captcha Form, vulnerability rewards program, google.com, CWE-79, CAPEC-86, DORK, GHDB Report by

Trusted Types - Securing the DOM from the bottom up (JSNation Amsterdam)

bug bounty program Archives - Security Affairs
XSS: Principles, Attacks and Security Best Practices
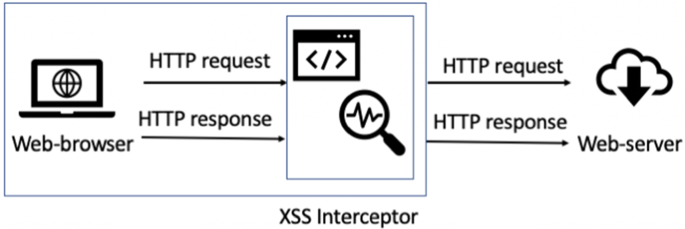
Detection of cross-site scripting (XSS) attacks using machine learning techniques: a review

PayPal Mitigates XSS Vulnerability - BankInfoSecurity
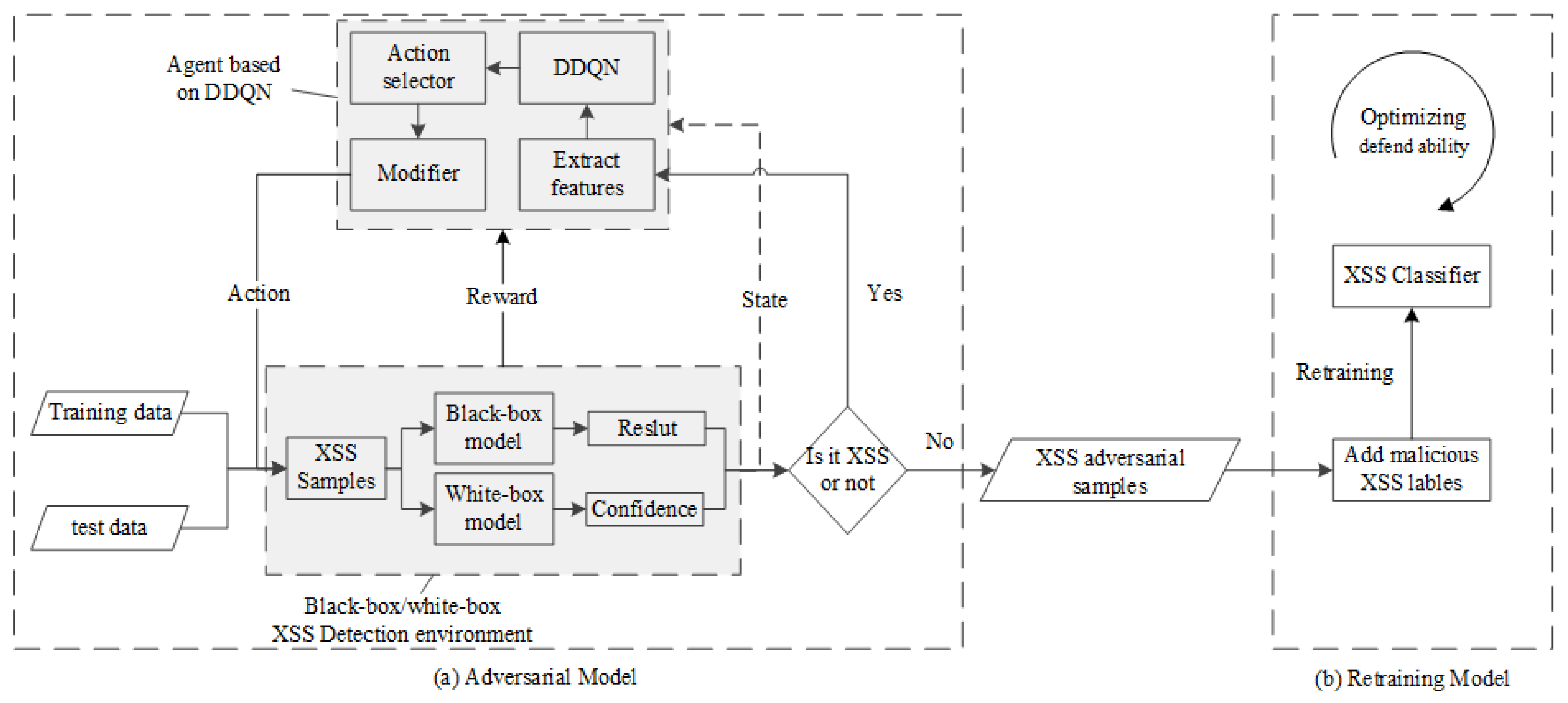
Future Internet, Free Full-Text

Web application vulnerability scans for GKE and Compute Engine are generally available

3,000 USD Bounty Finding The Stored Xss Bug using Manual Testing

RebelMouse's Security Bug Bounty Program - RebelMouse

JavaScript for Hacking Made Easy: The Expert Guide on Security

Cross-Site Scripting (XSS) - Page 2 of 3 - Security Intelligence

XSS.Cx Blog: Google Vulnerability Rewards Program: Reflected XSS in mail. google.com
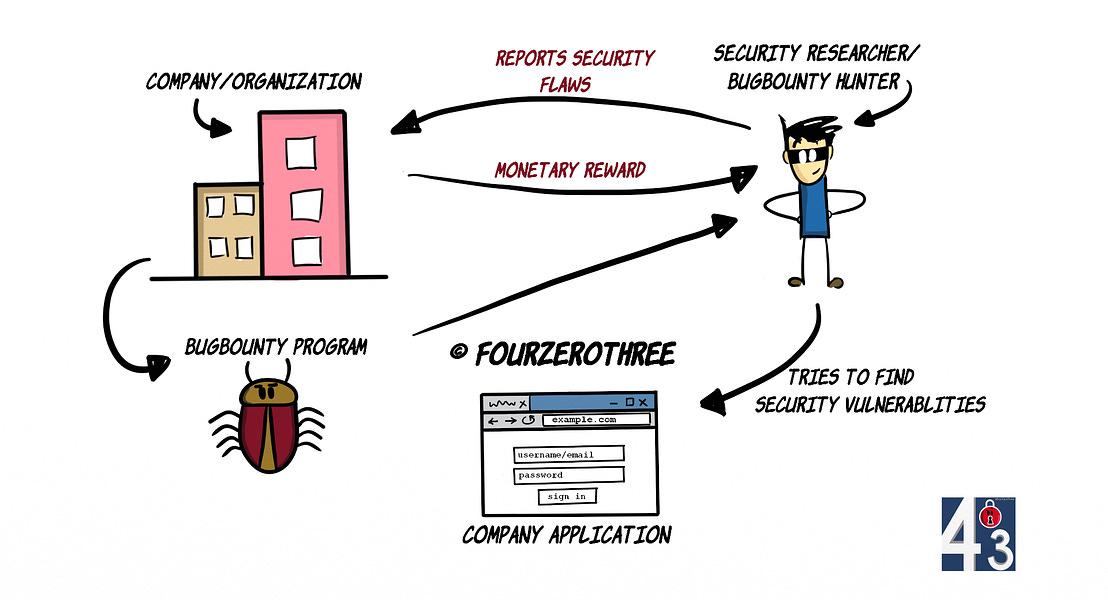
The fascinating World of Bug Bounty hunting - What it is and how you could get your feet wet

7 steps to avoid uncoordinated vulnerability disclosure
Recomendado para você
-
 What is XSS?, Understanding Cross-Site Scripting19 outubro 2024
What is XSS?, Understanding Cross-Site Scripting19 outubro 2024 -
Getting started with XSS: Cross-Site Scripting Attacks19 outubro 2024
-
HTML from Strings and XSS - Beginner JavaScript - Wes Bos19 outubro 2024
-
 AppFW XSS Was not getting detected19 outubro 2024
AppFW XSS Was not getting detected19 outubro 2024 -
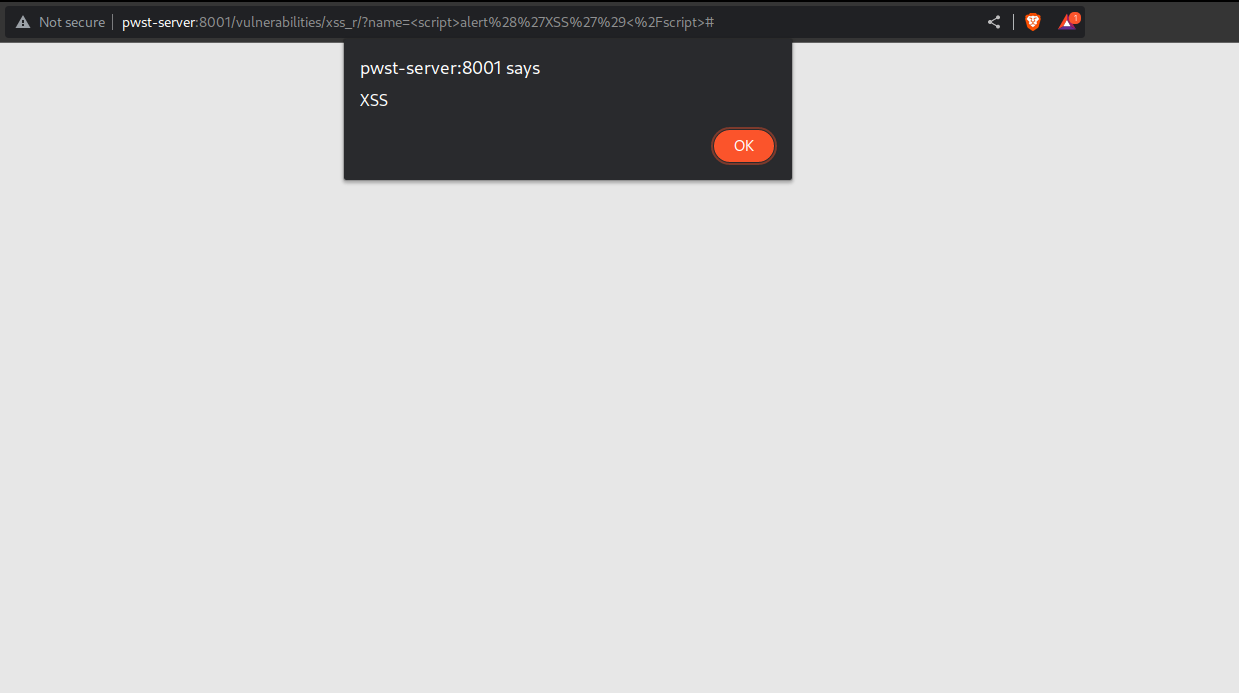 Exploiting DVWA Using Reflected Cross-Site Scripting (XSS)19 outubro 2024
Exploiting DVWA Using Reflected Cross-Site Scripting (XSS)19 outubro 2024 -
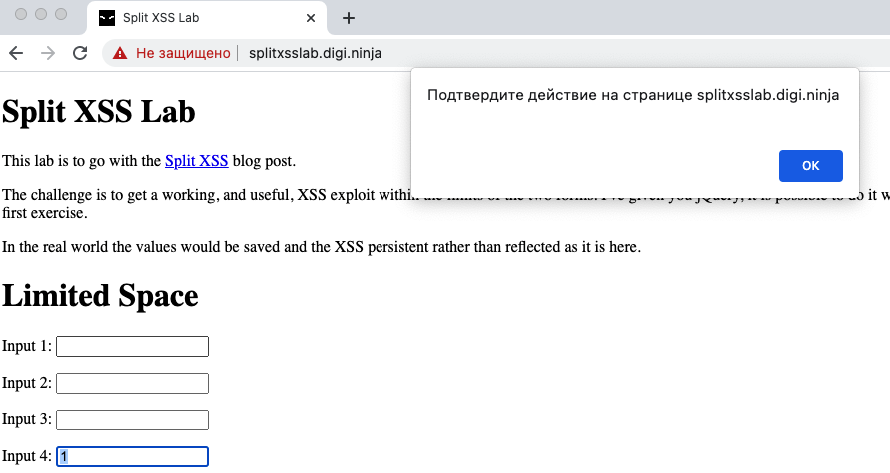 Lifehacks for hackers: Split XSS – Lyhins' Lab19 outubro 2024
Lifehacks for hackers: Split XSS – Lyhins' Lab19 outubro 2024 -
Xsss store19 outubro 2024
-
 CYBSEC Advisory#2011-0402 Multiple XSSs in Oracle JD Edwards19 outubro 2024
CYBSEC Advisory#2011-0402 Multiple XSSs in Oracle JD Edwards19 outubro 2024 -
 Cross Site Scripting - XSS19 outubro 2024
Cross Site Scripting - XSS19 outubro 2024 -
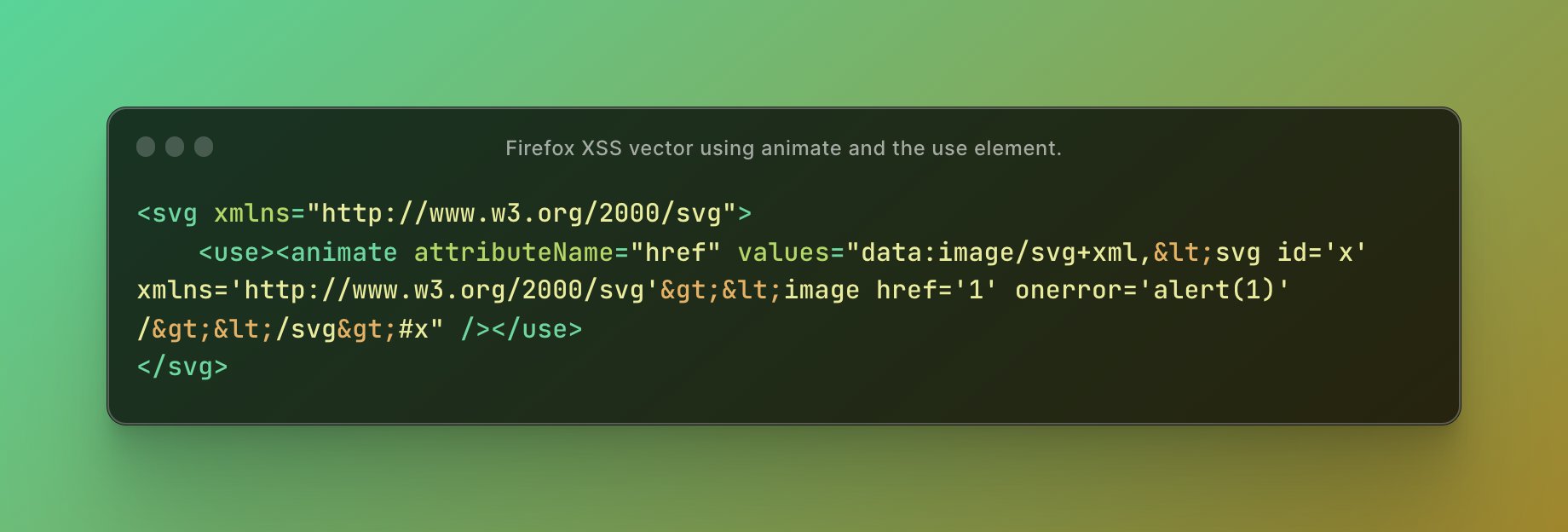 Gareth Heyes on X: A quite wonderful Firefox only XSS vector19 outubro 2024
Gareth Heyes on X: A quite wonderful Firefox only XSS vector19 outubro 2024
você pode gostar
-
![MELHOR] King Legacy Hack Script: AUTO FARM, COLLECT FRUITS](https://i.ytimg.com/vi/a_T9vU5k14s/maxresdefault.jpg) MELHOR] King Legacy Hack Script: AUTO FARM, COLLECT FRUITS19 outubro 2024
MELHOR] King Legacy Hack Script: AUTO FARM, COLLECT FRUITS19 outubro 2024 -
 Xadrez Figura Rei Rainha Bispo Cavaleiro Torre Peão Conjunto Dois imagem vetorial de jekin013© 24265511819 outubro 2024
Xadrez Figura Rei Rainha Bispo Cavaleiro Torre Peão Conjunto Dois imagem vetorial de jekin013© 24265511819 outubro 2024 -
 AcTiVision Guitar Hero III: Legends of Rock - Game Only (Playstation 2) Musical Games for Playstation 2 : Video Games19 outubro 2024
AcTiVision Guitar Hero III: Legends of Rock - Game Only (Playstation 2) Musical Games for Playstation 2 : Video Games19 outubro 2024 -
 Limited Quantity Neon Genesis Evangelion Watches Now Available to Pre-Order - Siliconera19 outubro 2024
Limited Quantity Neon Genesis Evangelion Watches Now Available to Pre-Order - Siliconera19 outubro 2024 -
.jpg?width=1920&height=1920&fit=bounds&quality=80&format=jpg&auto=webp) Zachary Levi and cast of Shazam! Fury of the Gods pen their own Shazam family comic19 outubro 2024
Zachary Levi and cast of Shazam! Fury of the Gods pen their own Shazam family comic19 outubro 2024 -
 Munching for Meaning Prepared for: Florida Council of Teachers of19 outubro 2024
Munching for Meaning Prepared for: Florida Council of Teachers of19 outubro 2024 -
/i.s3.glbimg.com/v1/AUTH_63b422c2caee4269b8b34177e8876b93/internal_photos/bs/2019/H/y/k4jUhNTQ6Udx5UUE5qmQ/foto04emp-201-call-b5.jpg) AeC adia novas centrais de call center, Empresas19 outubro 2024
AeC adia novas centrais de call center, Empresas19 outubro 2024 -
 Pawn Promotion: How to Promote a Pawn in Chess - 2023 - MasterClass19 outubro 2024
Pawn Promotion: How to Promote a Pawn in Chess - 2023 - MasterClass19 outubro 2024 -
 Funny Aesthetic Summer Baby Tee Streetwear Gothic Harajuku Loded Diper Letter Graphic Emo T-shirt Crop Top Women Y2k Clothes - AliExpress19 outubro 2024
Funny Aesthetic Summer Baby Tee Streetwear Gothic Harajuku Loded Diper Letter Graphic Emo T-shirt Crop Top Women Y2k Clothes - AliExpress19 outubro 2024 -
 Especial – Pokémon: Meloetta19 outubro 2024
Especial – Pokémon: Meloetta19 outubro 2024
