Trojan.PDF.PHISH.TIAOOHQI - Threat Encyclopedia
Por um escritor misterioso
Last updated 02 abril 2025

This Trojan arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.It redirects browsers to certain sites.

PDF) THE TROJAN WAR David Tew

Threat Encyclopedia — How To Fix Guide

National Tyronians Identification Card – TYRO GYN PHI FRATERNITY
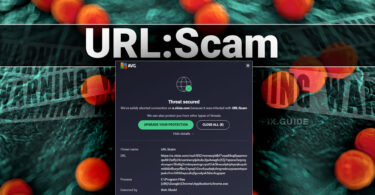
Threat Encyclopedia — How To Fix Guide

PDF) THE TROJAN WAR David Tew

Invisible Supply Chain Attacks Based on Trojan Source
PDF) A Conceptual Framework for Threat Assessment Based on
Malware Analysis - Suspicious Malware under PDF
Threat Encyclopedia

PDF) THE TROJAN WAR David Tew

PDF) Spyware and Trojan Horses IJSRD - International Journal for

PDF) THE TROJAN WAR David Tew

PDF) THE TROJAN WAR David Tew

PDF) Spyware and Trojan Horses IJSRD - International Journal for

HSTF-Model: An HTTP-based Trojan detection model via the
Recomendado para você
-
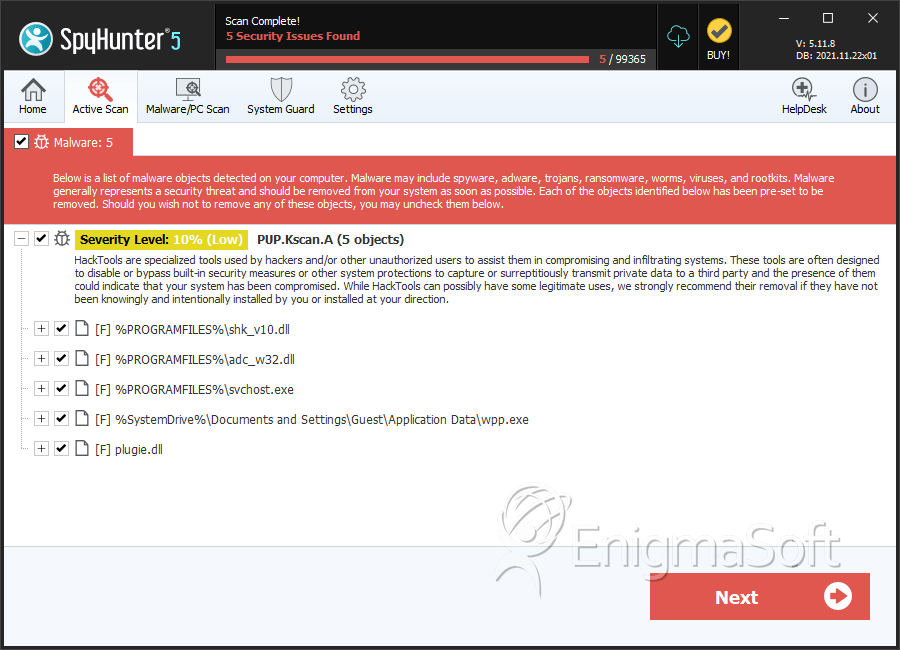 Trojan:Win32/FakeScanti Removal Report02 abril 2025
Trojan:Win32/FakeScanti Removal Report02 abril 2025 -
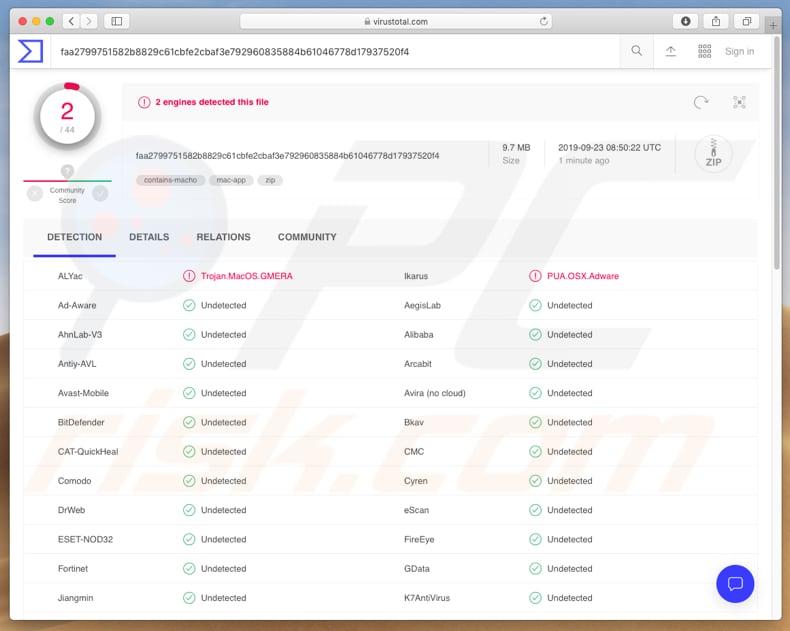 GMERA Trojan (Mac) - Removal steps, and macOS cleanup (updated)02 abril 2025
GMERA Trojan (Mac) - Removal steps, and macOS cleanup (updated)02 abril 2025 -
 Punkston TH61 Keyboard Software contains Trojan : r/MechanicalKeyboards02 abril 2025
Punkston TH61 Keyboard Software contains Trojan : r/MechanicalKeyboards02 abril 2025 -
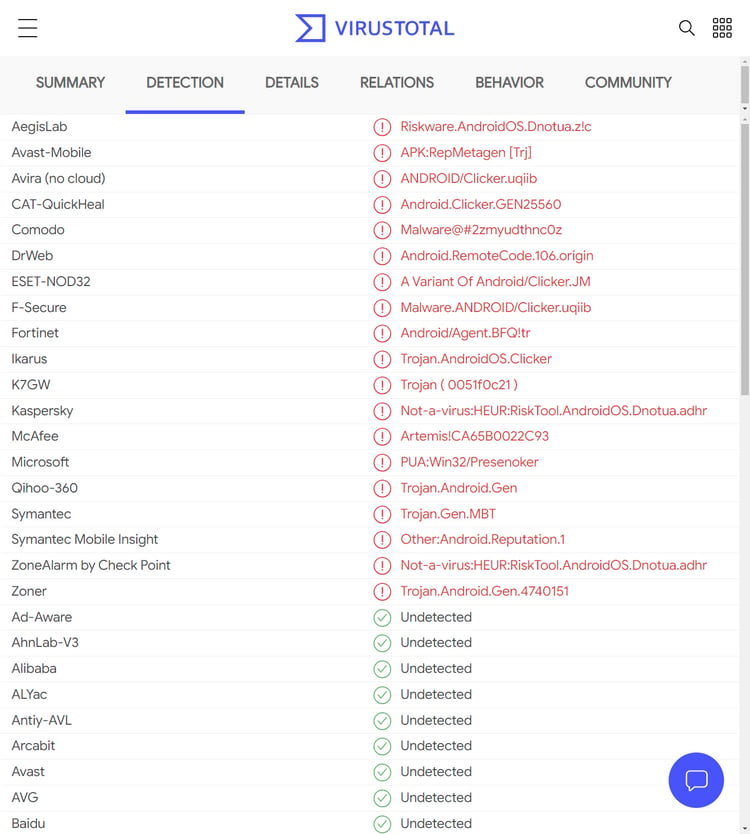 Riskware Android streaming apps found on Samsung's Galaxy store02 abril 2025
Riskware Android streaming apps found on Samsung's Galaxy store02 abril 2025 -
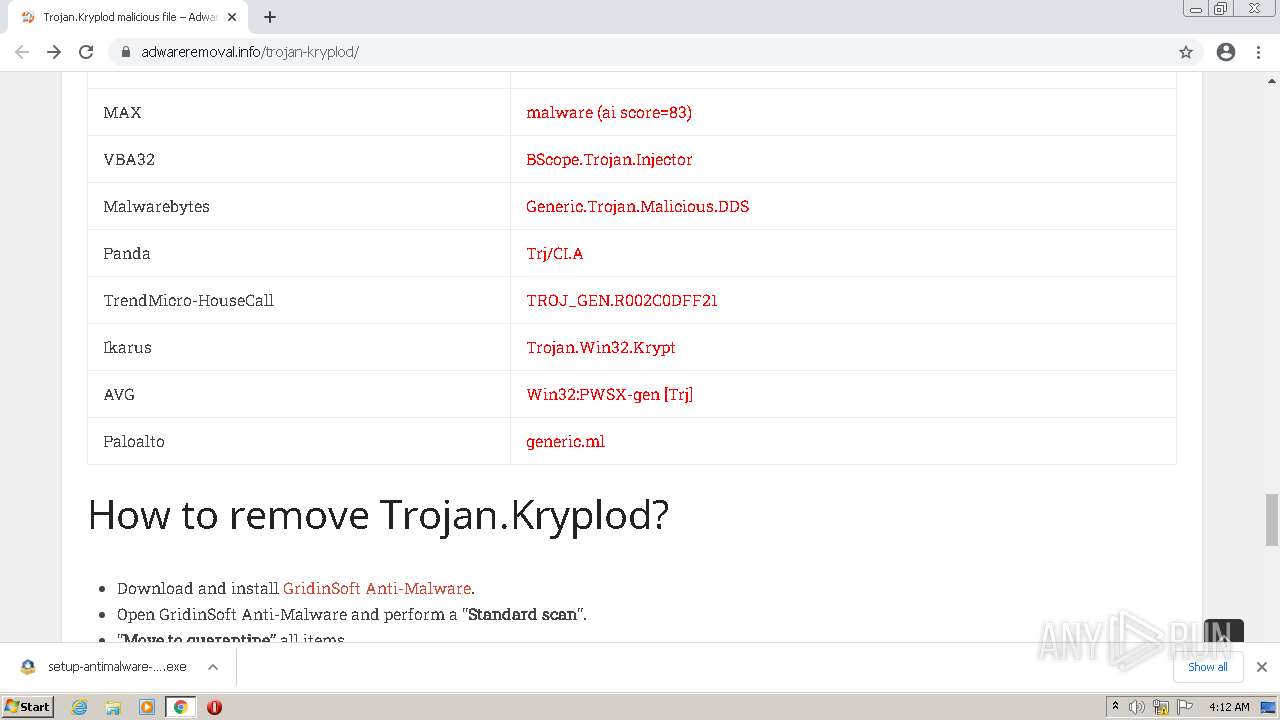 Malware analysis Malicious activity02 abril 2025
Malware analysis Malicious activity02 abril 2025 -
 Malware Must Die!: CNC analysis of Citadel Trojan Bot-Agent - Part 1: with Wireshark02 abril 2025
Malware Must Die!: CNC analysis of Citadel Trojan Bot-Agent - Part 1: with Wireshark02 abril 2025 -
 TROJ_UPATRE.YYMV - Threat Encyclopedia02 abril 2025
TROJ_UPATRE.YYMV - Threat Encyclopedia02 abril 2025 -
trojan virus Generik.ICX ESET virus scanner notification02 abril 2025
-
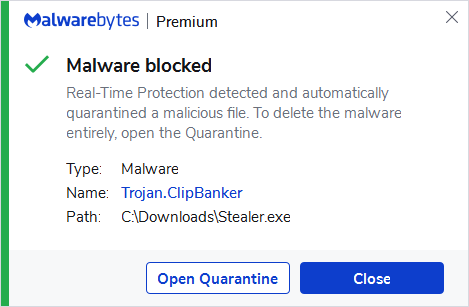 Trojan.ClipBanker02 abril 2025
Trojan.ClipBanker02 abril 2025 -
Trojan Virus Found in the Enigma Seven Lives Many Faces (2008) Music CD !!!02 abril 2025
você pode gostar
-
Clube de Xadrez Marabá: 230 - INTERATIVIDADE - ENCONTRE O MELHOR LANCE 1, 2, 3 e 402 abril 2025
-
 MM2 Roblox In-Game Heartblade Godly - Fast Delivery, Malaysia02 abril 2025
MM2 Roblox In-Game Heartblade Godly - Fast Delivery, Malaysia02 abril 2025 -
 Vetores de Ilustração Monocromática Livro De Colorir Conjunto De Sorvete De Verão Bonito Lanche Doce Frio Estilo Desenho Animado e mais imagens de Picolé - Sorvete - iStock02 abril 2025
Vetores de Ilustração Monocromática Livro De Colorir Conjunto De Sorvete De Verão Bonito Lanche Doce Frio Estilo Desenho Animado e mais imagens de Picolé - Sorvete - iStock02 abril 2025 -
 ✓ How to Install Google Play Store on iOS (iPhone & iPad) - Easy & Detailed Guide 202302 abril 2025
✓ How to Install Google Play Store on iOS (iPhone & iPad) - Easy & Detailed Guide 202302 abril 2025 -
 Expressões dos Seriados: Knock yourself out - English Experts02 abril 2025
Expressões dos Seriados: Knock yourself out - English Experts02 abril 2025 -
 ESC2018: Cantor austríaco lança letra em português de Nobody but02 abril 2025
ESC2018: Cantor austríaco lança letra em português de Nobody but02 abril 2025 -
 FIFA Mobile - Speedrun02 abril 2025
FIFA Mobile - Speedrun02 abril 2025 -
 SP - CORINTHIANS X GARATINGUETA - ESPORTES - Os jogadores Bovio(d) coloca esparadrapo na marca da alianca de Dentinho(e), durante partida válida pelo Campeonato Paulista 2008, primeiro turno, realizada no estádio do02 abril 2025
SP - CORINTHIANS X GARATINGUETA - ESPORTES - Os jogadores Bovio(d) coloca esparadrapo na marca da alianca de Dentinho(e), durante partida válida pelo Campeonato Paulista 2008, primeiro turno, realizada no estádio do02 abril 2025 -
 Click - definition and meaning with pictures02 abril 2025
Click - definition and meaning with pictures02 abril 2025 -
Buu Saga 🔥 •credit @cat.destroyer •••••••••••••••••••••••••••••••••••••••••••••• #dragonball #dragonballz #dragonballgt #dragonballsuper…02 abril 2025
