Malware analysis Suspicious activity
Por um escritor misterioso
Last updated 14 abril 2025

Malware Incident Response Steps on Windows, and Determining If the

Top 10 Malware Analysis Platforms & Tools

Malware Analysis: Steps & Examples - CrowdStrike
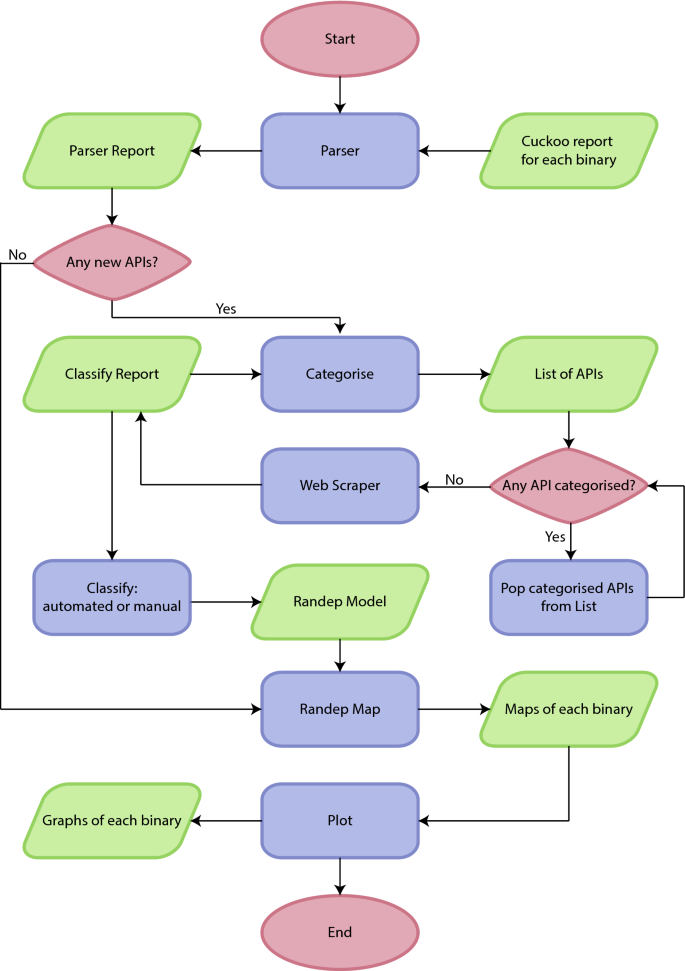
Ransomware deployment methods and analysis: views from a

What is Network Behavior Analysis (NBA)

10 Best Malware Analysis Tools - Updated 2023! (Paid & Free)
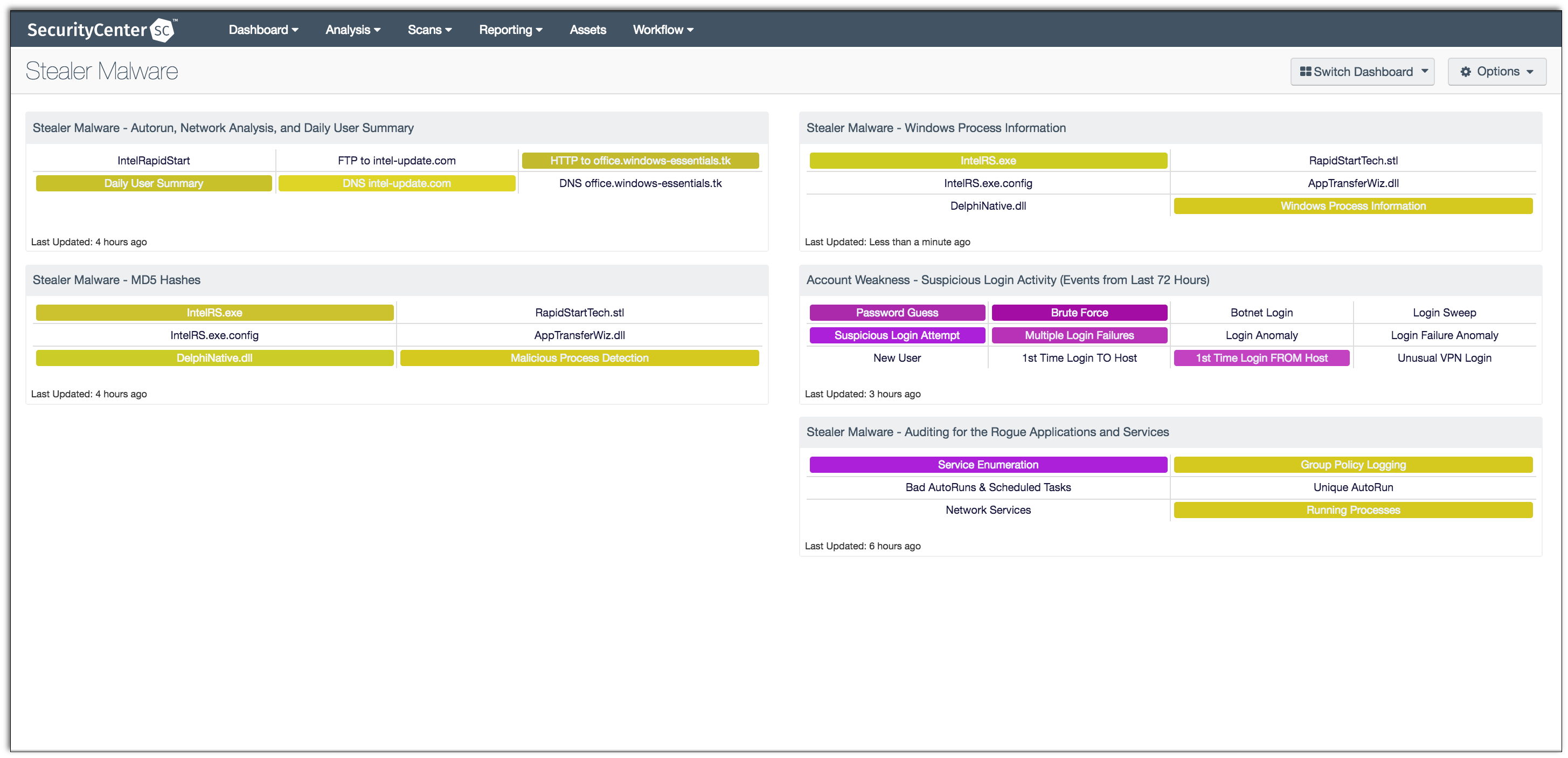
Stealer Malware - SC Dashboard
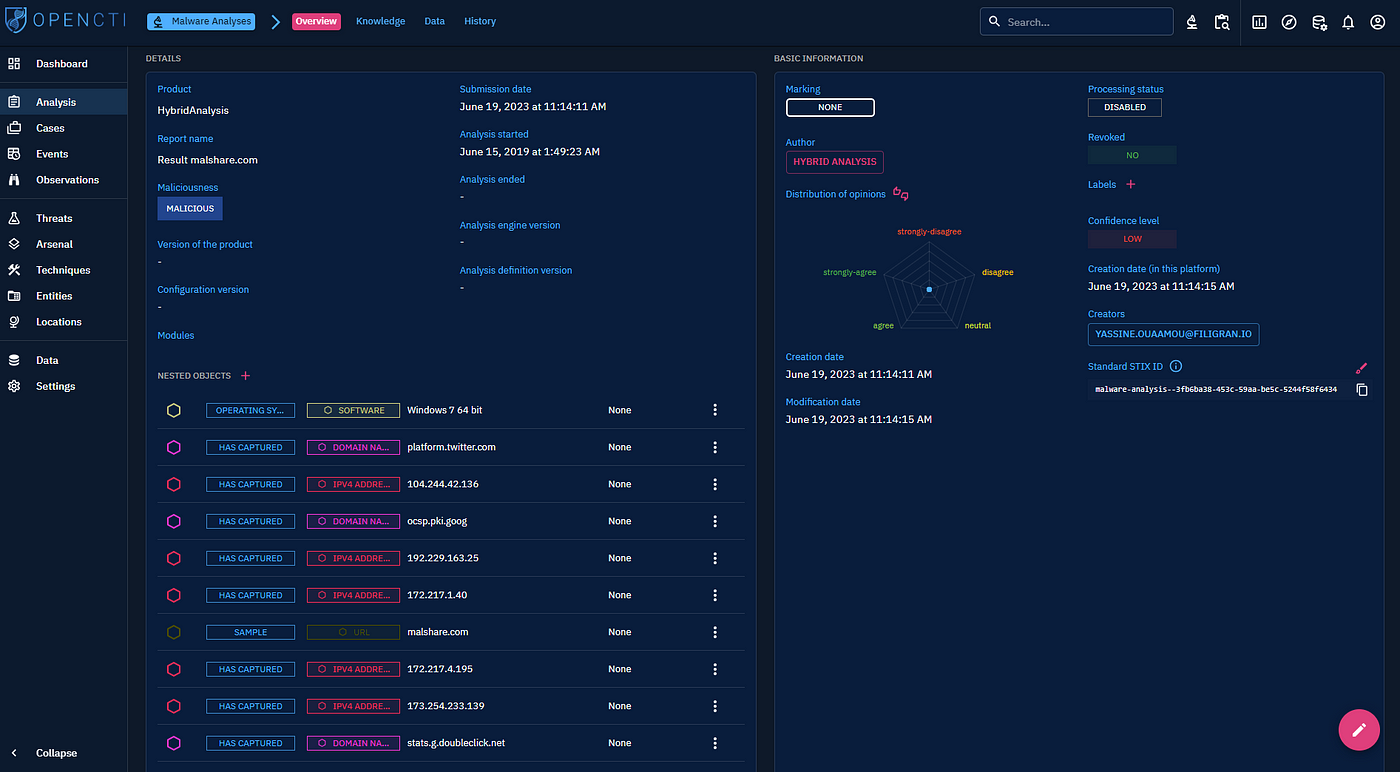
Introducing malware analysis: enhance your cybersecurity triage

1. General Flow of Signature-Based Malware Detection and Analysis

How to Detect New Threats via Suspicious Activities
Highlight, take notes, and search in the book

Mastering Malware Analysis: A malware analyst's practical guide to combating malicious software, APT, cybercrime, and IoT attacks, 2nd Edition
Recomendado para você
-
 Roblox on the App Store14 abril 2025
Roblox on the App Store14 abril 2025 -
 Pin em Roblox Hack 202114 abril 2025
Pin em Roblox Hack 202114 abril 2025 -
roblox-hacks · GitHub Topics · GitHub14 abril 2025
-
roblox-executor · GitHub Topics · GitHub14 abril 2025
-
 Zeus S Executor Free, Zeus S Roblox Script 202314 abril 2025
Zeus S Executor Free, Zeus S Roblox Script 202314 abril 2025 -
ke3) Dungeon Quest Script Roblox Hack (AutoFarm) Download 2023 2023 - New Undetected Version (gg9i - Collection14 abril 2025
-
 Why You Should Avoid Roblox Hack V3.7 Download 70 Մամուլի խոսնակ - Անկախ հրապարակումների հարթակ14 abril 2025
Why You Should Avoid Roblox Hack V3.7 Download 70 Մամուլի խոսնակ - Անկախ հրապարակումների հարթակ14 abril 2025 -
 roblox mod menu modder14 abril 2025
roblox mod menu modder14 abril 2025 -
 robux: Roblox 2023 guide: How to get free Robux? Here's what you need to know - The Economic Times14 abril 2025
robux: Roblox 2023 guide: How to get free Robux? Here's what you need to know - The Economic Times14 abril 2025 -
 Roblox - Apps on Google Play14 abril 2025
Roblox - Apps on Google Play14 abril 2025
você pode gostar
-
 animation adorable gif14 abril 2025
animation adorable gif14 abril 2025 -
 Why Is Minecraft The Biggest Selling Game?14 abril 2025
Why Is Minecraft The Biggest Selling Game?14 abril 2025 -
 Juxtaposition between Development and Tribal Rights: A Story of Determined Struggle of Niyamgiri Tribes14 abril 2025
Juxtaposition between Development and Tribal Rights: A Story of Determined Struggle of Niyamgiri Tribes14 abril 2025 -
 Zombie apocalypse - Wikiwand14 abril 2025
Zombie apocalypse - Wikiwand14 abril 2025 -
 BEN10 Omnitrix Toy Kids Watch Cartoon Children 3D Projector Watch Genuine Anime Figures Model PVC Toys for Boys Birthday Gifts - AliExpress14 abril 2025
BEN10 Omnitrix Toy Kids Watch Cartoon Children 3D Projector Watch Genuine Anime Figures Model PVC Toys for Boys Birthday Gifts - AliExpress14 abril 2025 -
 akatsuki ring - Compre akatsuki ring com envio grátis no14 abril 2025
akatsuki ring - Compre akatsuki ring com envio grátis no14 abril 2025 -
 Parking Department14 abril 2025
Parking Department14 abril 2025 -
 Top 15 Best funny gifs — you can't stop Laughing!!, by Funny Gifs & Funny Images, Meme, Downloadfeast14 abril 2025
Top 15 Best funny gifs — you can't stop Laughing!!, by Funny Gifs & Funny Images, Meme, Downloadfeast14 abril 2025 -
 CapCut_how to get key in arceus x 202214 abril 2025
CapCut_how to get key in arceus x 202214 abril 2025 -
 120 Free Fire Wallpaper ideas14 abril 2025
120 Free Fire Wallpaper ideas14 abril 2025