Malware analysis Malicious
Por um escritor misterioso
Last updated 31 março 2025

How to Do Malware Analysis?

Malware Analysis: Steps & Examples - CrowdStrike
Top static malware analysis techniques for beginners

Malware Analysis: Steps & Examples - CrowdStrike
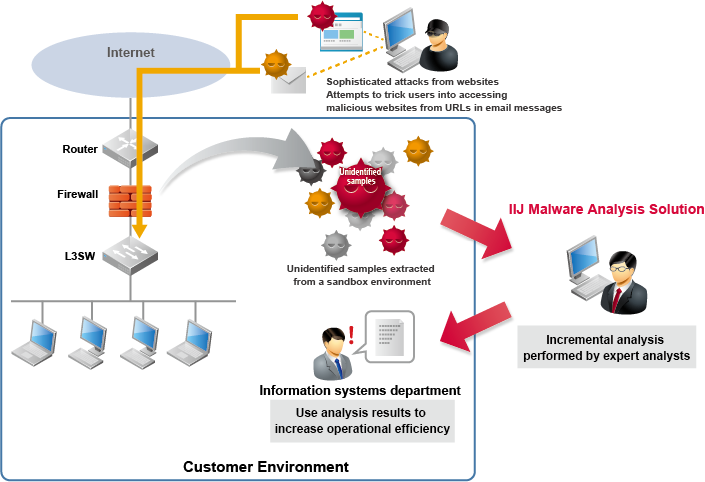
IIJ Malware Analysis Solution, Business

Basic Malware Analysis: Malicious Data Mining E-Mail Attachment – CYBER ARMS – Computer Security

The Role of Malware Analysis in Cybersecurity
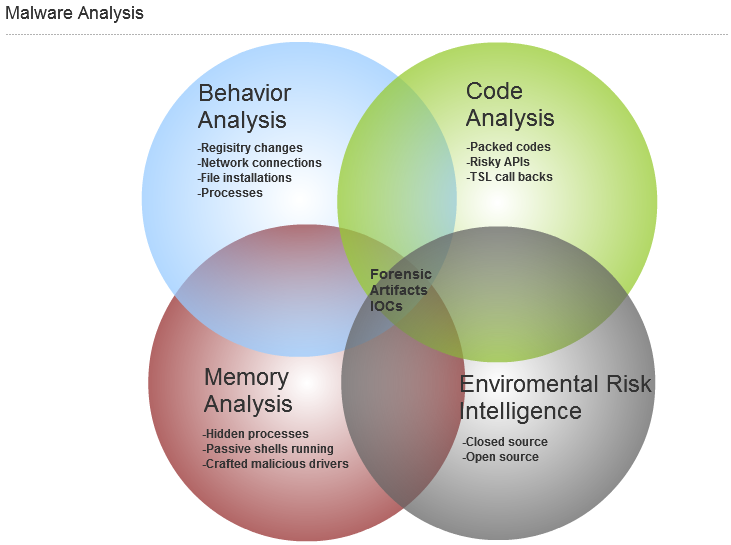
SANS Digital Forensics and Incident Response Blog, Four Focus Areas of Malware Analysis
Highlight, take notes, and search in the book In this edition, page numbers are just like the physical edition

Practical Malware Analysis: The Hands-On Guide to Dissecting Malicious Software

TryHackMe Malware Analysis

A MS word malware analysis Part2: Analyzing malicious macros, by Nishan Maharjan
Recomendado para você
-
wearedevs.net Competitors - Top Sites Like wearedevs.net31 março 2025
-
 Krnl Wearedevs GIF - Krnl Wearedevs Virus - Discover & Share GIFs31 março 2025
Krnl Wearedevs GIF - Krnl Wearedevs Virus - Discover & Share GIFs31 março 2025 -
 Top game mods tagged wearedevs31 março 2025
Top game mods tagged wearedevs31 março 2025 -
wearedevs.net31 março 2025
-
 Wearedevs.net é confiável? Wearedevs é segura?31 março 2025
Wearedevs.net é confiável? Wearedevs é segura?31 março 2025 -
WeAreDevs · GitHub31 março 2025
-
 How to make a proxy for wearedevs - WRD Community31 março 2025
How to make a proxy for wearedevs - WRD Community31 março 2025 -
 wearedevs Memes & GIFs - Imgflip31 março 2025
wearedevs Memes & GIFs - Imgflip31 março 2025 -
AIESEC in Austria - We are excited to invite you to the31 março 2025
-
 Virus Hack GIF - Virus Hack Malware - Discover & Share GIFs31 março 2025
Virus Hack GIF - Virus Hack Malware - Discover & Share GIFs31 março 2025
você pode gostar
-
 Roblox Analysts Divided On Timing Of Margin Expansion, $5B Market31 março 2025
Roblox Analysts Divided On Timing Of Margin Expansion, $5B Market31 março 2025 -
 Tycoons To Reopen Soon - In A Time Of Restaurants Closing Desmond Rice Announces A Relaunch, Explocity Guide To Bangalore31 março 2025
Tycoons To Reopen Soon - In A Time Of Restaurants Closing Desmond Rice Announces A Relaunch, Explocity Guide To Bangalore31 março 2025 -
CONTAINS MANGA SPOILER] Haikyuu Vol. - Haikyuu to Basuke31 março 2025
-
 Remnant 2: Uma análise completa - Dolutech31 março 2025
Remnant 2: Uma análise completa - Dolutech31 março 2025 -
 4k wallpaper for pc 1920x1080 - top10_4k wallpaper for pc_31 março 2025
4k wallpaper for pc 1920x1080 - top10_4k wallpaper for pc_31 março 2025 -
How to Use Abstraction Effectively in Logo Design31 março 2025
-
 Kanye West confuses fans with face mask at BET Awards 202231 março 2025
Kanye West confuses fans with face mask at BET Awards 202231 março 2025 -
 Velozes e Furiosos 10 tem cena pós-crédito? - Canaltech31 março 2025
Velozes e Furiosos 10 tem cena pós-crédito? - Canaltech31 março 2025 -
 showcase soul guitar in blox fruit|TikTok Search31 março 2025
showcase soul guitar in blox fruit|TikTok Search31 março 2025 -
DC - The gods have arrived. ⚡SHAZAM! FURY OF THE GODS is31 março 2025

![CONTAINS MANGA SPOILER] Haikyuu Vol. - Haikyuu to Basuke](https://lookaside.fbsbx.com/lookaside/crawler/media/?media_id=3663019443748054)

