Initial access broker repurposing techniques in targeted attacks
Por um escritor misterioso
Last updated 12 abril 2025

Describing activities of a crime group attacking Ukraine.
Cybersecurity Risk Fact #3: Initial Access Brokers Attack What Organizations Ignore

Disk-Locking HDDCryptor/Mamba Ransomware Makes a Comeback - Security News - Trend Micro IN

Security in product lifecycle of IoT devices: A survey - ScienceDirect

The Role AI Can Play in Pharmaceutical Discovery - Techopedia

Cisco Umbrella discovers evolving cyberthreats in first half of 2020
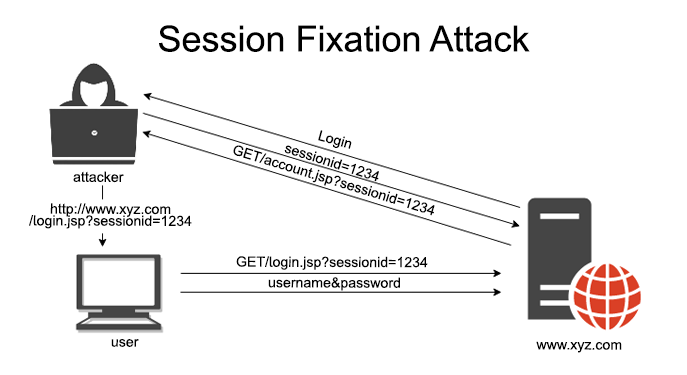
Session Side Hijacking Vulnerability in Ethical Hacking - GeeksforGeeks
New Report: Risky Analysis: Assessing and Improving AI Governance Tools

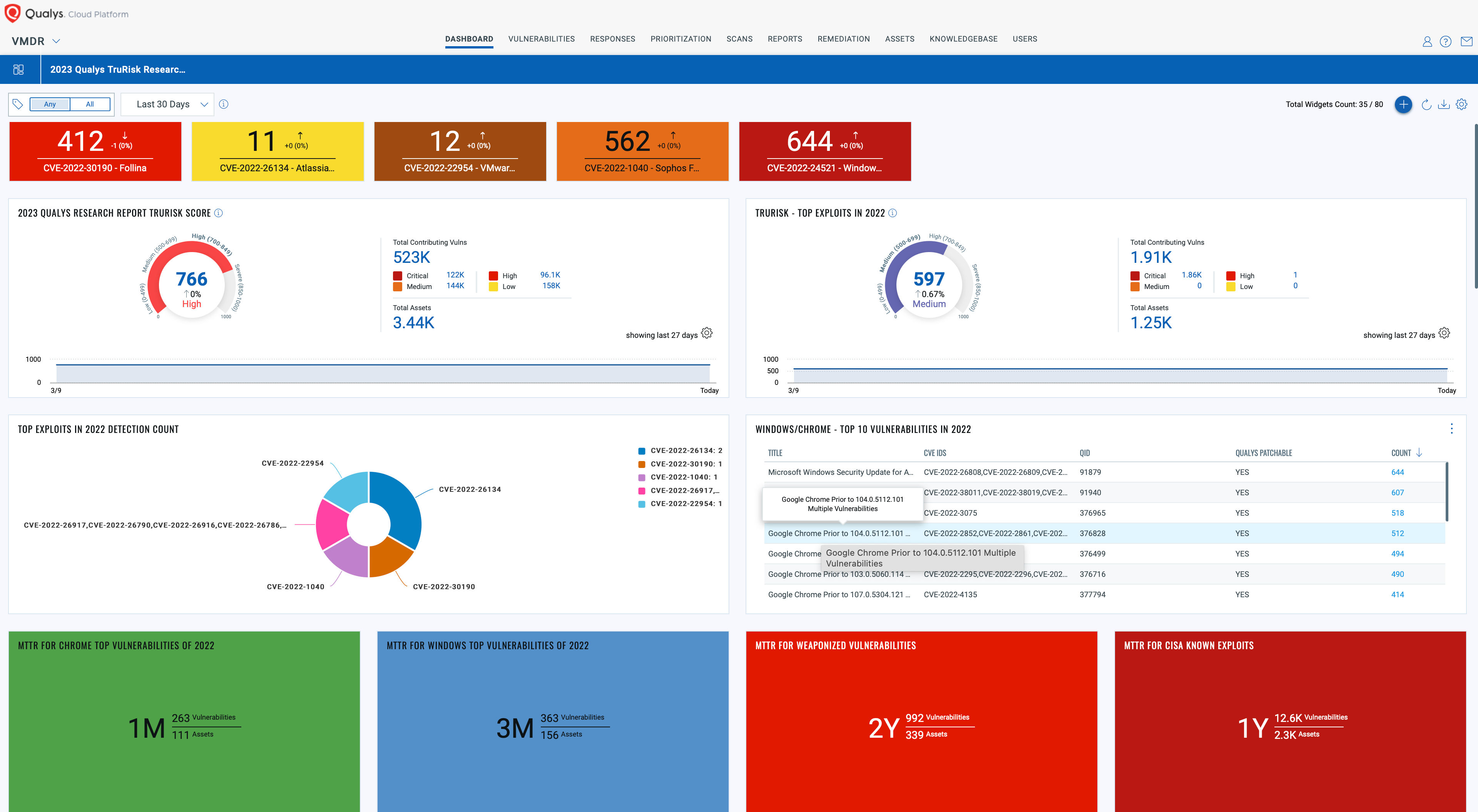
Initial Access Brokers Fueling Ransomware
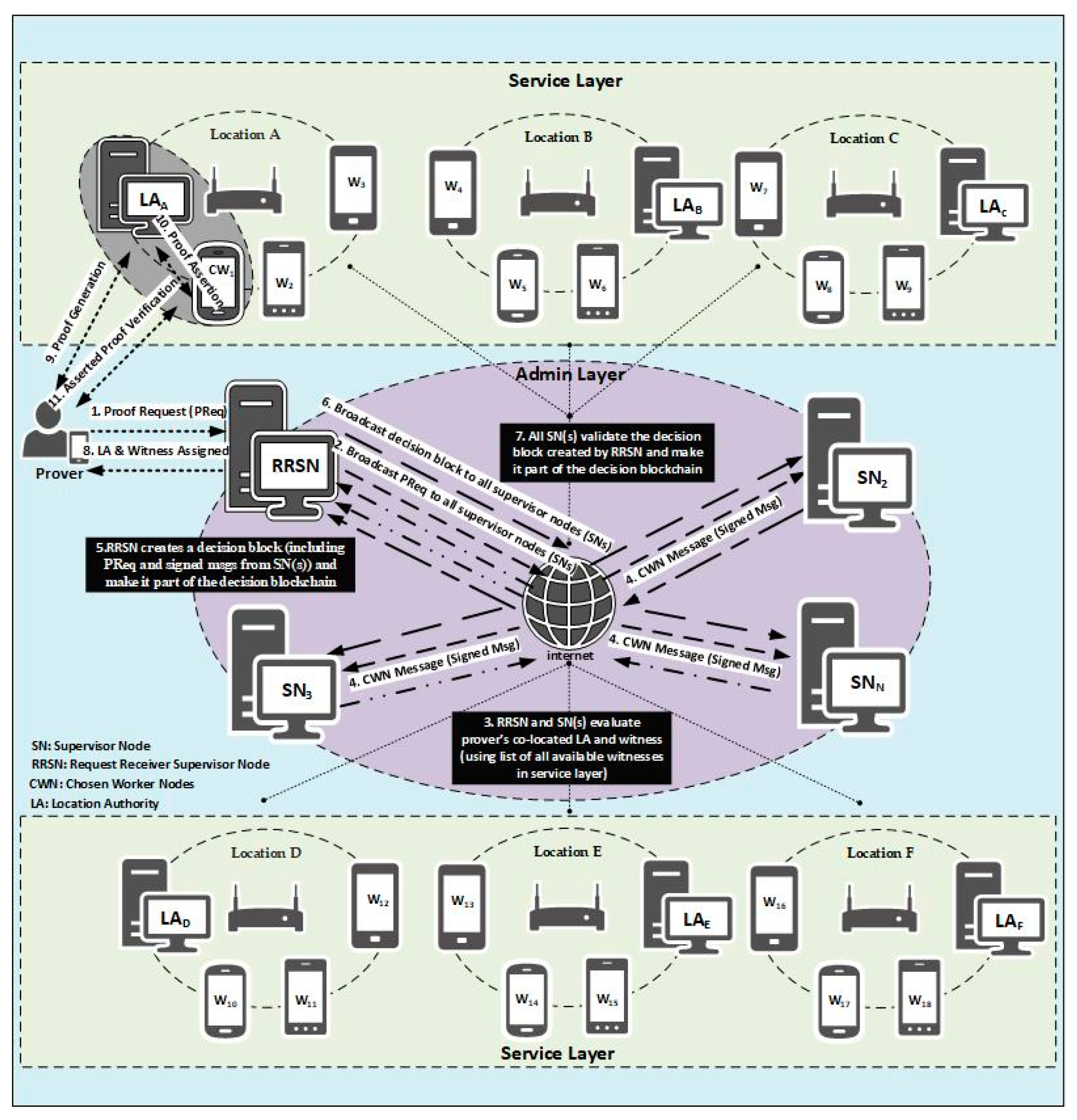
Sensors, Free Full-Text

Security in product lifecycle of IoT devices: A survey - ScienceDirect

Transfer Learning: Repurposing ML Algorithms from Different Domains to Cloud Defense

Into the Hashed Realm: Understanding the Privacy Risks Associated with the Use of Hashed Emails for Advertising, by Tolulope Ogundele
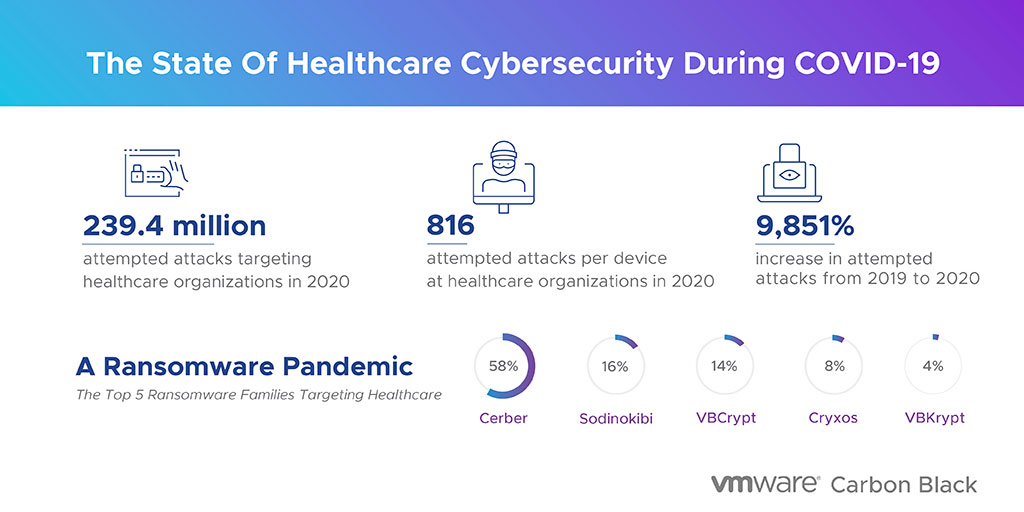
The State of Healthcare Cybersecurity: VMware Carbon Black Explores the Surge in Cyber Threats - REAL security

Blogs Dell Technologies Info Hub
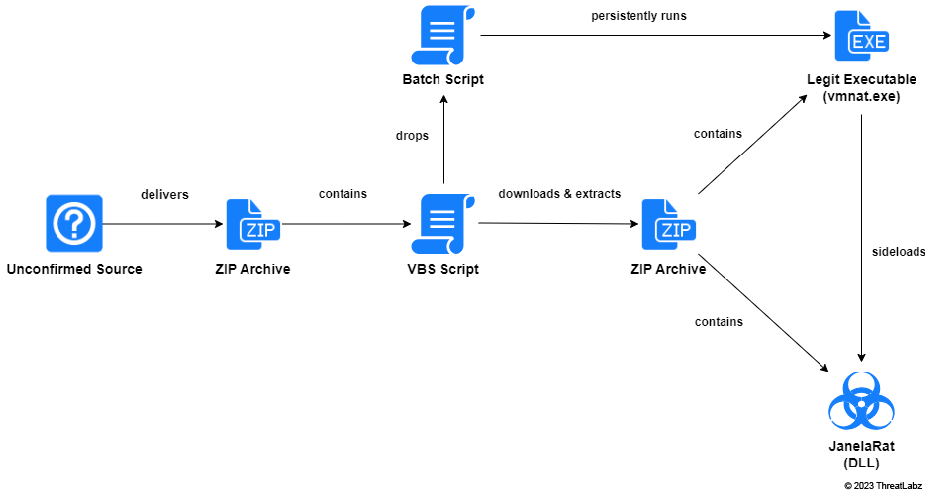
JanelaRAT ThreatLabz Zscaler Blog
Recomendado para você
-
 Analysis Group (@analysisgroup) / X12 abril 2025
Analysis Group (@analysisgroup) / X12 abril 2025 -
 Menlo Park - Analysis Group12 abril 2025
Menlo Park - Analysis Group12 abril 2025 -
 Careers - Analysis Group12 abril 2025
Careers - Analysis Group12 abril 2025 -
Derek Vicino - Vice President of Finance - Analysis Group12 abril 2025
-
 Not All Evidence is Equal - Threat Analysis Group12 abril 2025
Not All Evidence is Equal - Threat Analysis Group12 abril 2025 -
 Our People - Analysis Group12 abril 2025
Our People - Analysis Group12 abril 2025 -
 Active North Korean campaign targeting security researchers12 abril 2025
Active North Korean campaign targeting security researchers12 abril 2025 -
Target Analysis Group12 abril 2025
-
 Media Ecosystems Analysis Group12 abril 2025
Media Ecosystems Analysis Group12 abril 2025 -
 Analysis Team – Analysis, Reporting & Planning Solutions12 abril 2025
Analysis Team – Analysis, Reporting & Planning Solutions12 abril 2025
você pode gostar
-
 Kit Festa Redondo c/ Nome + Idade Monstros Sa12 abril 2025
Kit Festa Redondo c/ Nome + Idade Monstros Sa12 abril 2025 -
 Mutirão contra jagunçada. Empate na estrada de Boca do Acr…12 abril 2025
Mutirão contra jagunçada. Empate na estrada de Boca do Acr…12 abril 2025 -
 What Is the Autism Creature (aka TBH, TBH Creature, Yippee)?12 abril 2025
What Is the Autism Creature (aka TBH, TBH Creature, Yippee)?12 abril 2025 -
![EA SPORTS FC 24 Ultimate - Steam PC [Online Game Code] : Everything Else](https://images-na.ssl-images-amazon.com/images/I/81Y37sig2yL._AC_UL600_SR600,600_.jpg) EA SPORTS FC 24 Ultimate - Steam PC [Online Game Code] : Everything Else12 abril 2025
EA SPORTS FC 24 Ultimate - Steam PC [Online Game Code] : Everything Else12 abril 2025 -
 Cartilha xadrez12 abril 2025
Cartilha xadrez12 abril 2025 -
11564681 - Copa Libertadores - Corinthians vs. LiverpoolSearch12 abril 2025
-
 Hunter/Game - Live DJ Set @ Afterlife (Tulum) 12-01-2018 - Listen Online12 abril 2025
Hunter/Game - Live DJ Set @ Afterlife (Tulum) 12-01-2018 - Listen Online12 abril 2025 -
 3 NOVOS CODIGO DE RESGATE 2020 LORDS MOBILE12 abril 2025
3 NOVOS CODIGO DE RESGATE 2020 LORDS MOBILE12 abril 2025 -
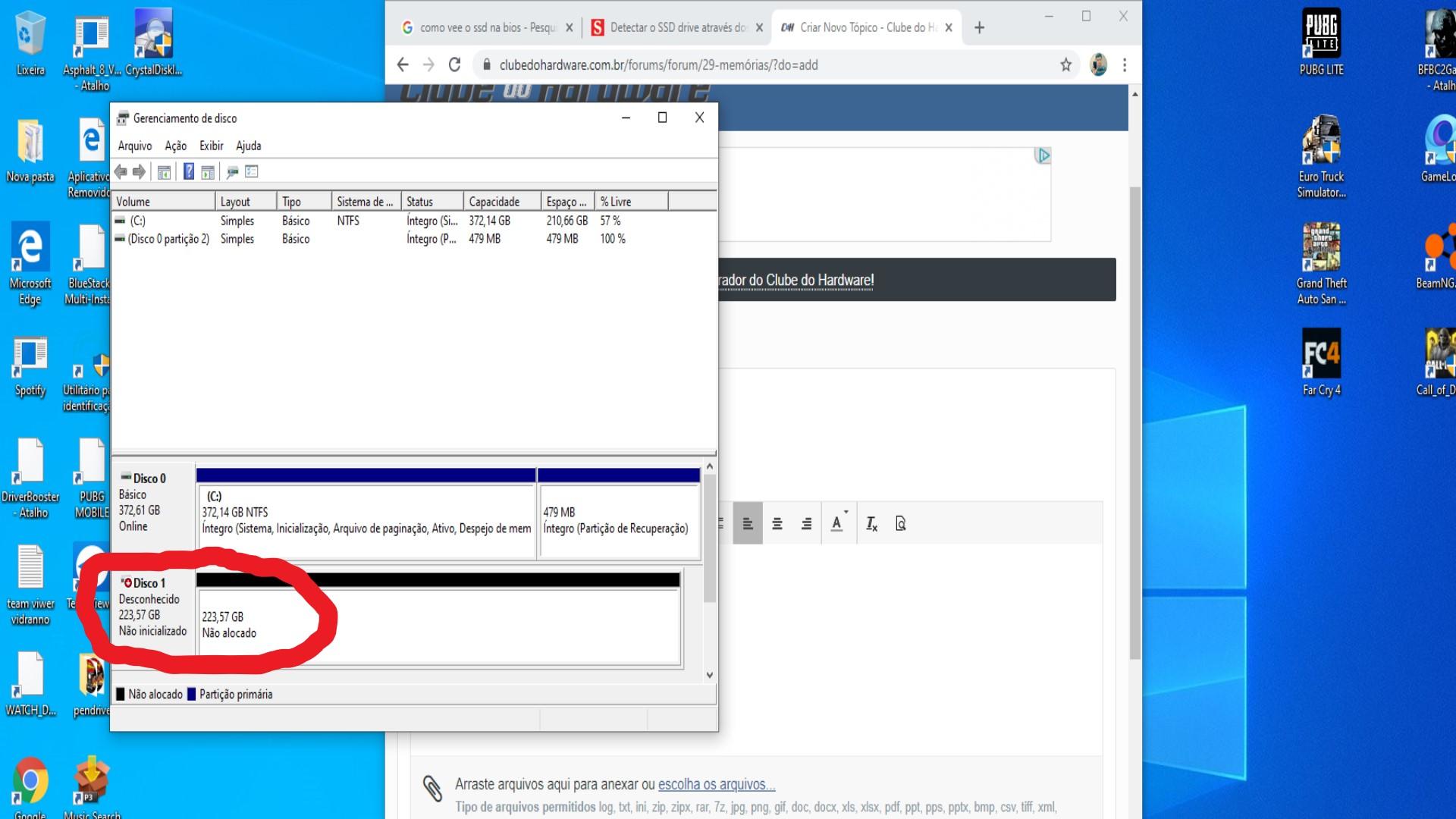 erro de ssd kingston 240gb, SATAFIRM s11 - HD, SSD e NAS - Clube12 abril 2025
erro de ssd kingston 240gb, SATAFIRM s11 - HD, SSD e NAS - Clube12 abril 2025 -
 Firefox start page Themes & Skins12 abril 2025
Firefox start page Themes & Skins12 abril 2025

