Do Not Cross The 'RedLine' Stealer: Detections and Analysis
Por um escritor misterioso
Last updated 10 abril 2025

The Splunk Threat Research Team provides a deep dive analysis of the RedLine Stealer threat and shares valuable insights to help enable blue teamers to defend against and detect this malware variant.
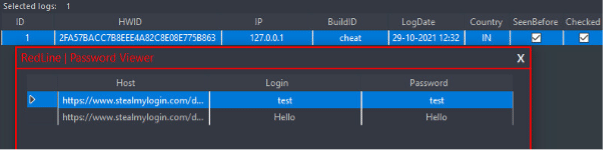
Preventing Credential Theft by RedLine Stealer Malware - Attivo Networks

Do Not Cross The 'RedLine' Stealer: Detections and Analysis
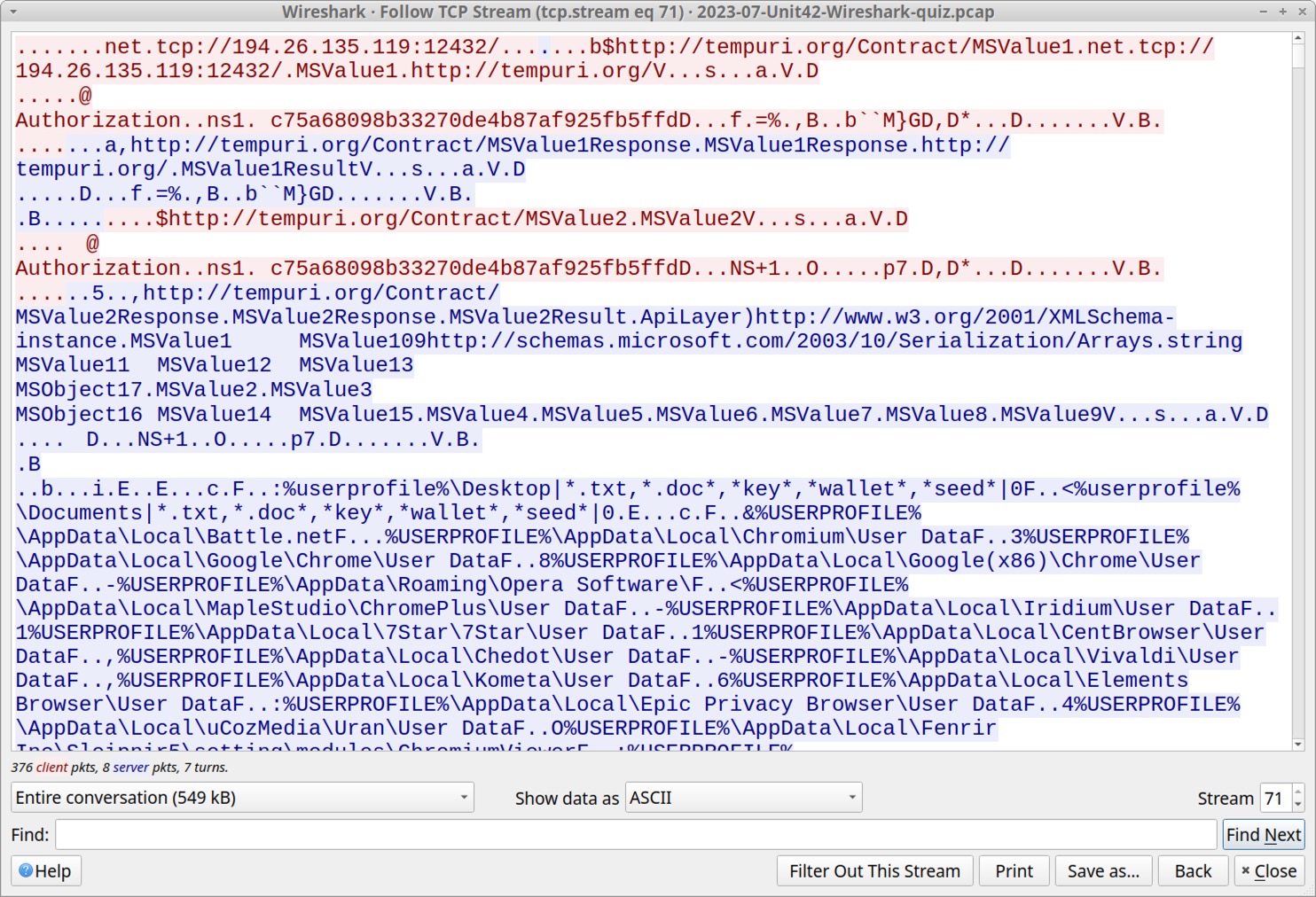
RedLine Stealer: Answers to Unit 42 Wireshark Quiz

Do Not Cross The 'RedLine' Stealer: Detections and Analysis

Crossing the Line: Unit 42 Wireshark Quiz for RedLine Stealer

Dominant Info-Stealing Malware: RedLine, Raccoon, and Vidar
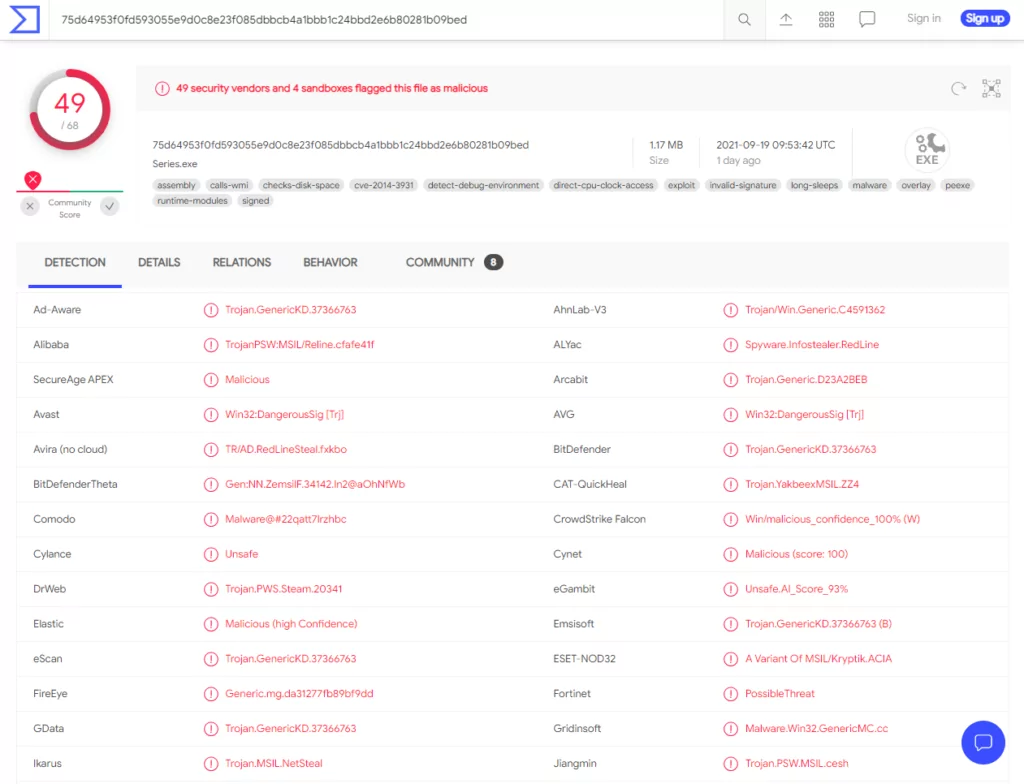
What is RedLine Stealer and What Can You Do About it? - SOCRadar® Cyber Intelligence Inc.

Do Not Cross The 'RedLine' Stealer: Detections and Analysis

A Detailed Analysis of the RedLine Stealer

A thief in red: Compliance and the RedLine information stealer
Recomendado para você
-
🔥New Roblox Working *BYPASSED* Audio Codes/IDs in 2023! #fyp #bypasse, Better Call Saul10 abril 2025
-
 All Roblox Zo Samurai codes for free Shards & Spins in December10 abril 2025
All Roblox Zo Samurai codes for free Shards & Spins in December10 abril 2025 -
 Murder Mystery 2 Codes (December 2023) - Knives, Gold & more10 abril 2025
Murder Mystery 2 Codes (December 2023) - Knives, Gold & more10 abril 2025 -
 All Evade Codes in Roblox (December 2023)10 abril 2025
All Evade Codes in Roblox (December 2023)10 abril 2025 -
 Evade 🍀 Codes Wiki 2023 - St Patricks Update Codes10 abril 2025
Evade 🍀 Codes Wiki 2023 - St Patricks Update Codes10 abril 2025 -
 Evade Codes November 2023 - Pillar Of Gaming10 abril 2025
Evade Codes November 2023 - Pillar Of Gaming10 abril 2025 -
 Evade codes December 2023 - PROJAKER10 abril 2025
Evade codes December 2023 - PROJAKER10 abril 2025 -
 Redtrite10 abril 2025
Redtrite10 abril 2025 -
 Full code Evade Roblox mới nhất 2023, cách nhập code10 abril 2025
Full code Evade Roblox mới nhất 2023, cách nhập code10 abril 2025 -
 Stranger Danger - Self-Defense, Escape & Evade10 abril 2025
Stranger Danger - Self-Defense, Escape & Evade10 abril 2025
você pode gostar
-
 SAO Wikia on X: On this day, at 14:55 on 7 November, 2024, Sword10 abril 2025
SAO Wikia on X: On this day, at 14:55 on 7 November, 2024, Sword10 abril 2025 -
![My 8k Collection of Anime Wallpapers [Various Resolutions] : r/Animewallpaper](https://external-preview.redd.it/xmbWsBjXjNHhSVrERDVjtv15JkJGKxVyiLfo-AVXoSE.jpg?width=640&crop=smart&auto=webp&s=83c70600da6b803cfc2581e41db605b8b42fe95a) My 8k Collection of Anime Wallpapers [Various Resolutions] : r/Animewallpaper10 abril 2025
My 8k Collection of Anime Wallpapers [Various Resolutions] : r/Animewallpaper10 abril 2025 -
Quadro Decorativo Mosaico 5 Peças Anjo Água E Fogo 3mm10 abril 2025
-
 Messi careca10 abril 2025
Messi careca10 abril 2025 -
 Mini World (id.avantgardelab.miniworld) 1.0 APK 下载- Android10 abril 2025
Mini World (id.avantgardelab.miniworld) 1.0 APK 下载- Android10 abril 2025 -
 MILTON NASCIMENTO - ATLANTIC GREEN – 101 Apparel10 abril 2025
MILTON NASCIMENTO - ATLANTIC GREEN – 101 Apparel10 abril 2025 -
 Pokemon Fossil Rare Card - Aerodactyl 16/6210 abril 2025
Pokemon Fossil Rare Card - Aerodactyl 16/6210 abril 2025 -
Temple Run - Welcome the Lunar New Year with the Lantern10 abril 2025
-
 PSN UK GBP25 – MyDigitalBN10 abril 2025
PSN UK GBP25 – MyDigitalBN10 abril 2025 -
 Suehara confesses to Shida Kuroha10 abril 2025
Suehara confesses to Shida Kuroha10 abril 2025


