Blog - Page 2 of 4 - Infosec
Por um escritor misterioso
Last updated 02 abril 2025
No blog da Infosec Security você encontra matérias relacionadas a vulnerabilidades em redes, aplicações Web, aplicativos mobile, ransomware, dentre outros.

The 5 Pillars of Information Security and How to Manage Them
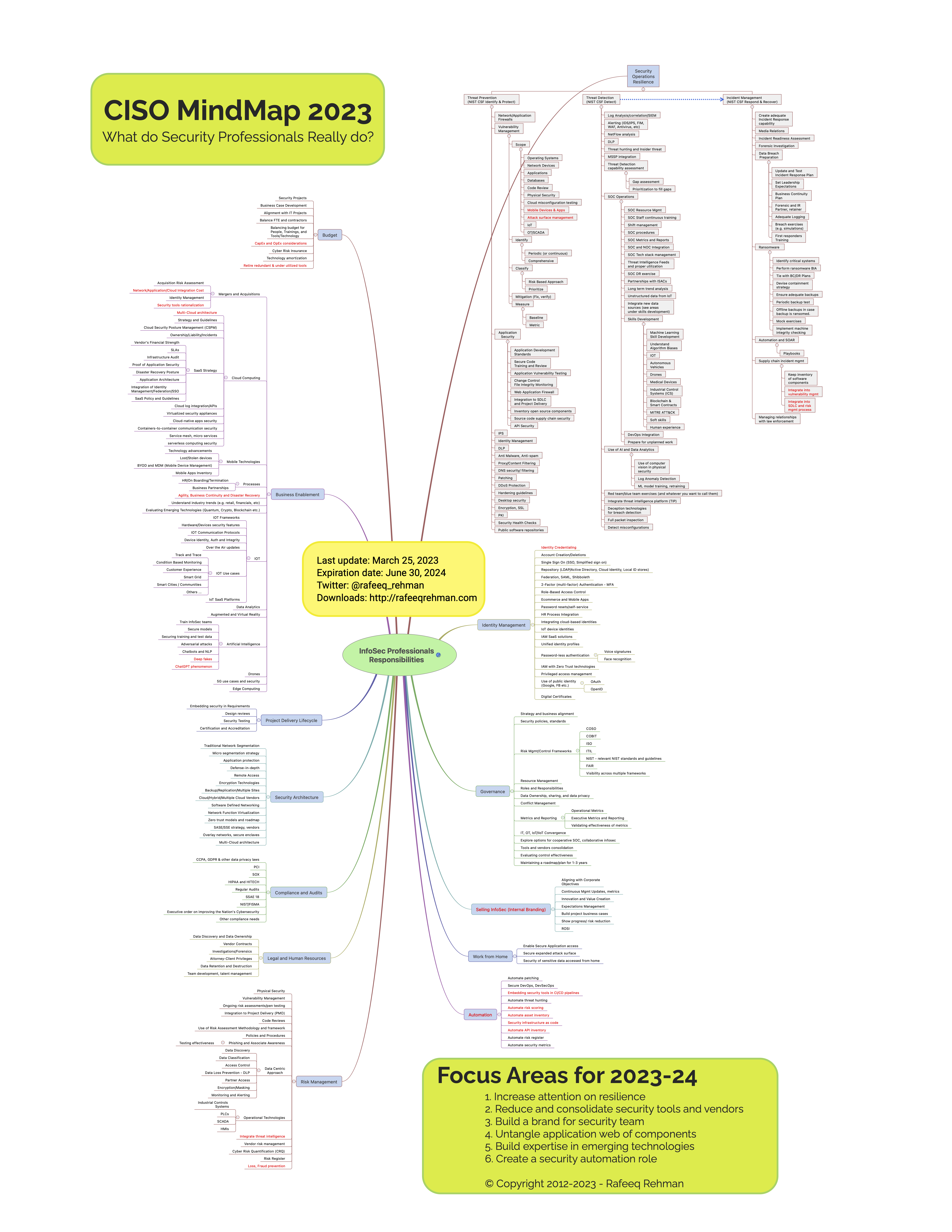
CISO MindMap 2023: What do InfoSec Professionals Really do?Rafeeq Rehman, Cyber, Automation

Blog - Lieberman Technologies

10 Information Security Policies Organizations Should Implement
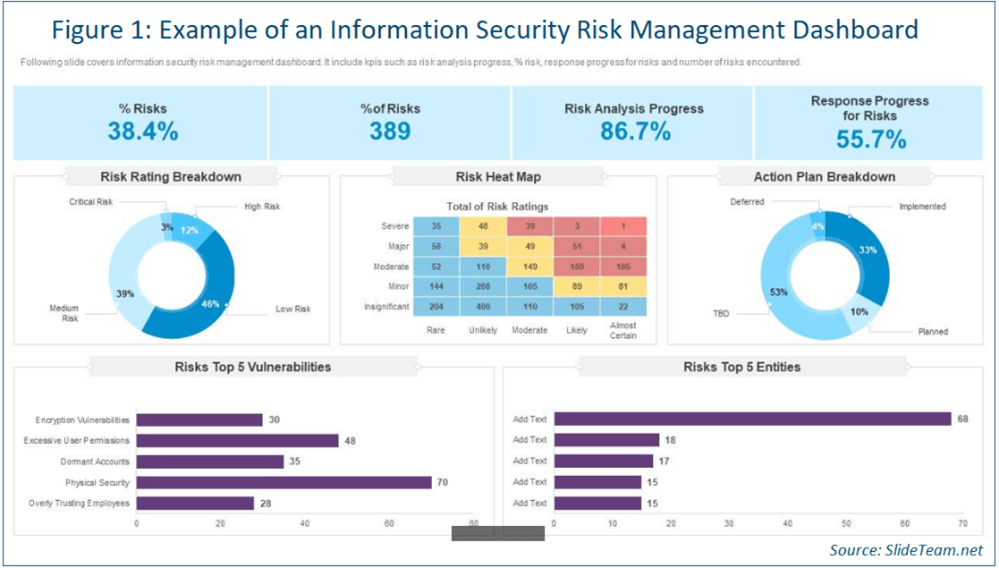
How to Create Effective Executive InfoSec Dashboard

Blog Series: “Information Security, Compliance and Governance in the Cloud Era - Oversimplified” - Part #2
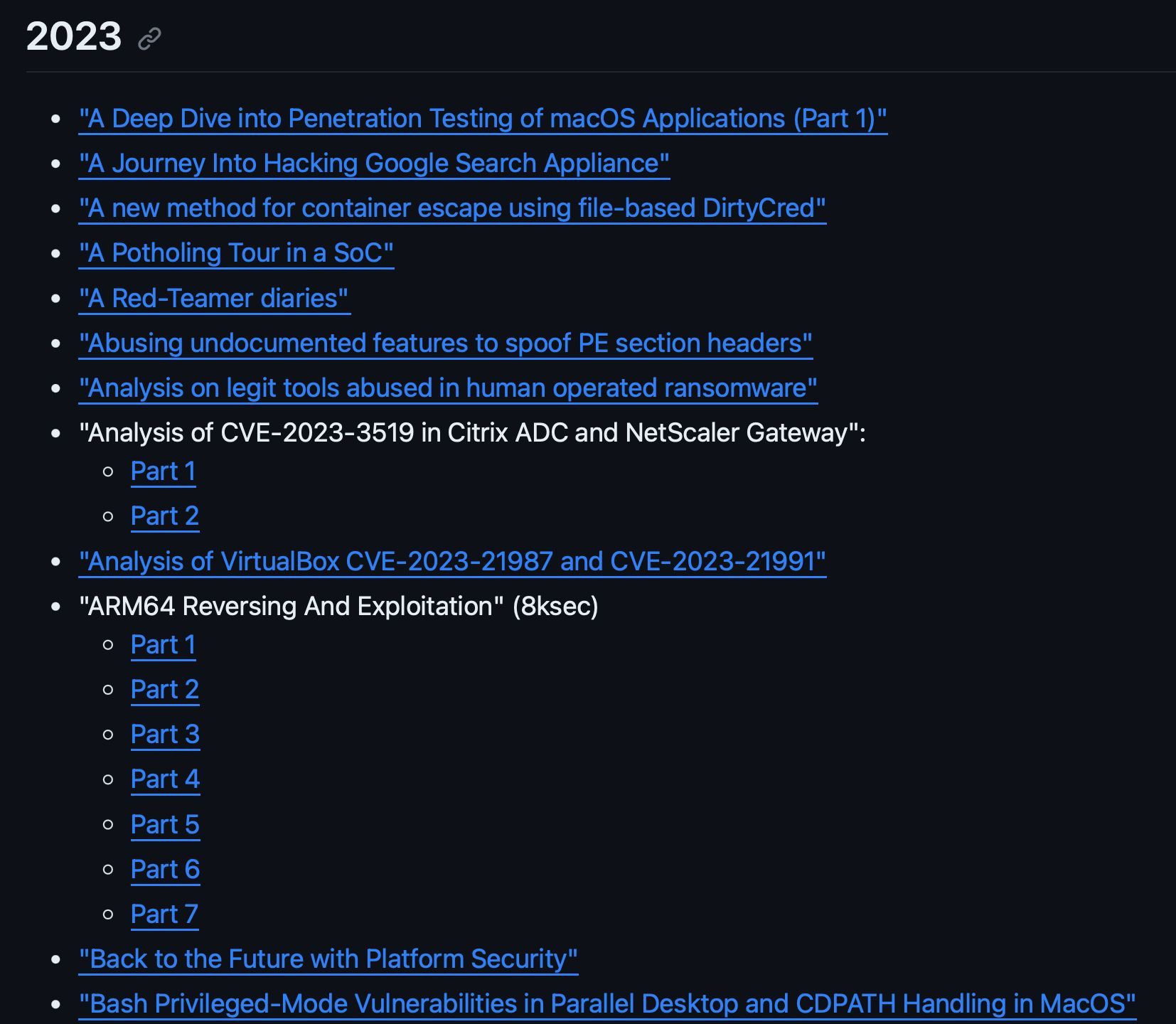
0xor0ne on X: List of links to blog posts, write-ups and papers related to cybersecurity, reverse engineering and exploitation (constantly updated) #cybersecurity #infosec / X

Altruism In Information Security? (Part 2 of 3)

Top OSINT & Infosec Resources for You and Your Team: 100+ Blogs, Podcasts, Channels, Books, and more! - Maltego

Guide on creating enterprise security policy – Tresorit

Unlock the world of Information Security Analyst: Salary, Must-Have Skills, and Beyond

What is an Information Security Policy and Why is it Important?

Information security policy: Core elements

Is The CIA Triad Relevant? Confidentiality, Integrity & Availability Today
Recomendado para você
-
 How to sign in02 abril 2025
How to sign in02 abril 2025 -
 Subscribing to Smart Proxy Manager - Zyte documentation02 abril 2025
Subscribing to Smart Proxy Manager - Zyte documentation02 abril 2025 -
 Olx Plugins, Code & Scripts02 abril 2025
Olx Plugins, Code & Scripts02 abril 2025 -
Jiji Ghana - Hi Everyone! OLX is now Jiji! Please if you are encountering any log in issues or any other difficulties please check out this FAQ! Thank you!02 abril 2025
-
I shared my OLX password/OTP with someone – India Help Center02 abril 2025
-
 OLX Autos (Dealers Only) on the App Store02 abril 2025
OLX Autos (Dealers Only) on the App Store02 abril 2025 -
 OLX Screen Redesign02 abril 2025
OLX Screen Redesign02 abril 2025 -
www.tokoaldhieprakerja.com02 abril 2025
-
 KIBU-OLX APK for Android Download02 abril 2025
KIBU-OLX APK for Android Download02 abril 2025 -
KinaBesa.com02 abril 2025
você pode gostar
-
) Stencil Fundo Mini Xadrez 2 Linhas 95 - Jeito Próprio Artesanato02 abril 2025
Stencil Fundo Mini Xadrez 2 Linhas 95 - Jeito Próprio Artesanato02 abril 2025 -
 evil boywithuke : r/boywithuke02 abril 2025
evil boywithuke : r/boywithuke02 abril 2025 -
 Desenhos do River para Colorir V2 – A beleza do simples02 abril 2025
Desenhos do River para Colorir V2 – A beleza do simples02 abril 2025 -
 Mini Mesa De Sinuca Bilhar Snooker Portatil Jogo Brinquedo02 abril 2025
Mini Mesa De Sinuca Bilhar Snooker Portatil Jogo Brinquedo02 abril 2025 -
 Pedra da Roseta, a chave do conhecimento sobre o Egito Antigo02 abril 2025
Pedra da Roseta, a chave do conhecimento sobre o Egito Antigo02 abril 2025 -
 Adachi and Shimamura Review (Episodes 1-3) - Niche Gamer02 abril 2025
Adachi and Shimamura Review (Episodes 1-3) - Niche Gamer02 abril 2025 -
Inscrições do Vestibulinho da Etec Philadelpho se encerram no dia 06 de junho Etec Philadelpho Gouvêa Netto, By Programa Jornal do Trabalhador02 abril 2025
-
 Will Champion's Feet << wikiFeet Men02 abril 2025
Will Champion's Feet << wikiFeet Men02 abril 2025 -
 Últimos classificados para as oitavas de final da Série B serão conhecidos neste domingo (23) - Rede Web TV02 abril 2025
Últimos classificados para as oitavas de final da Série B serão conhecidos neste domingo (23) - Rede Web TV02 abril 2025 -
 Breaking Point (2023) — The Movie Database (TMDB)02 abril 2025
Breaking Point (2023) — The Movie Database (TMDB)02 abril 2025