Advanced Apple Debugging & Reverse Engineering, Chapter 31
Por um escritor misterioso
Last updated 09 abril 2025

In this chapter, you'll use DTrace to hook objc_msgSend's entry probe and pull out the class name along with the Objective-C selector for that class. By the end of this chapter, you'll have LLDB generating a DTrace script which only generates tracing info for code implemented within the main executable that calls objc_msgSend.

Mastering Malware Analysis

Windows Reverse Engineering - O'Reilly Media

Advanced Apple Debugging & Reverse Engineering, Chapter 31: DTrace vs. objc_msgSend

What Can Reverse Engineering Do For You?

iOS App Reverse Engineering

PDF) Reverse Engineering for Malicious Code Behavior Analysis using Virtual Security Patching
Future Internet, Free Full-Text
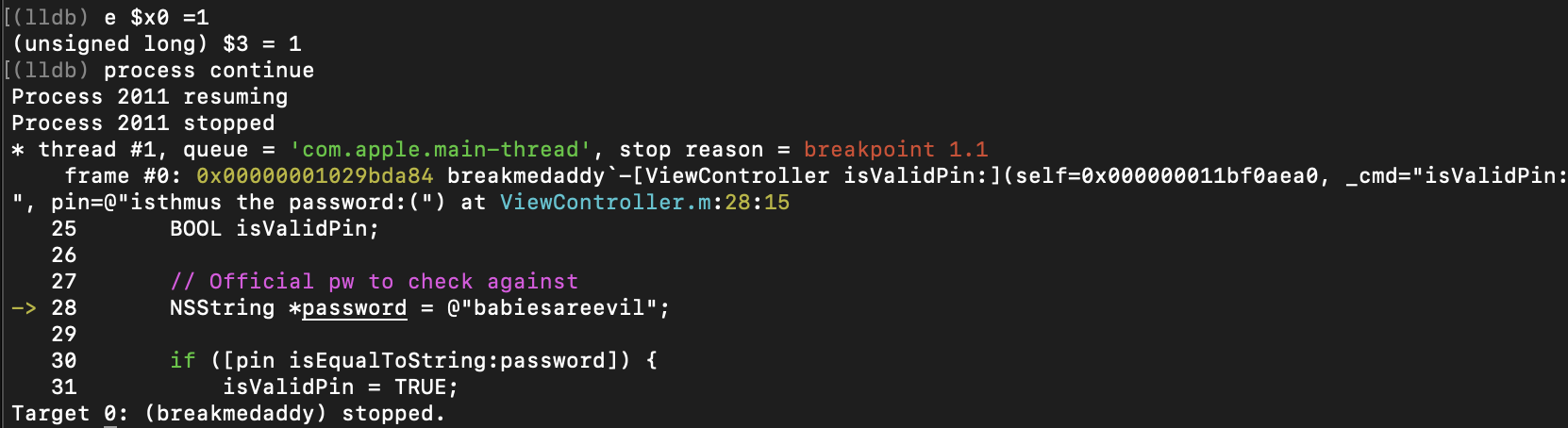
How to Reverse Engineer and Patch an iOS Application for Beginners: Part I
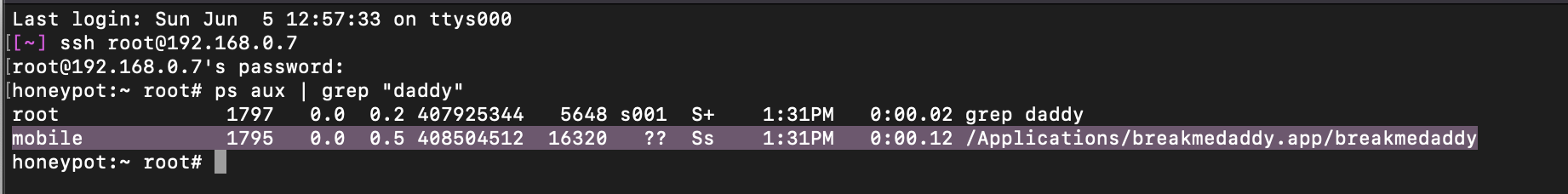
How to Reverse Engineer and Patch an iOS Application for Beginners: Part I

Advanced Apple Debugging & Reverse Engineering, Chapter 1: Getting Started

Mastering Malware Analysis
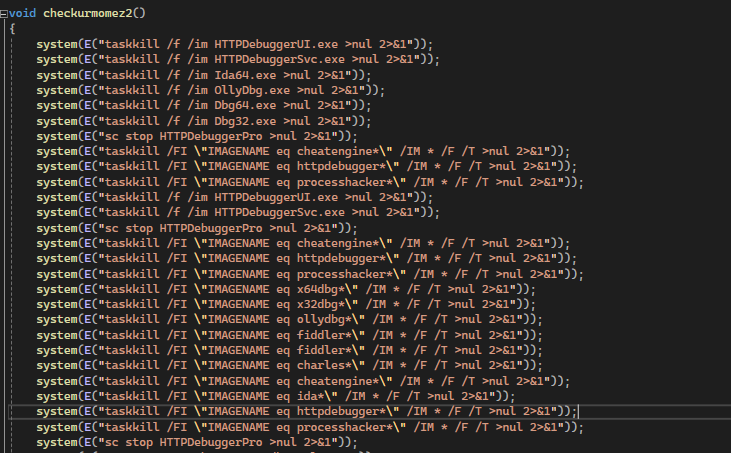
Reverse Engineering: Binary Security, by Totally_Not_A_Haxxer
Recomendado para você
-
Blox Fruits09 abril 2025
-
Flee The Facility Scripts09 abril 2025
-
RBX Gum, PDF, World Wide Web09 abril 2025
-
 What is the difference between Robux and Tix? - Quora09 abril 2025
What is the difference between Robux and Tix? - Quora09 abril 2025 -
como ver los codigos de rbx gum en discord|Búsqueda de TikTok09 abril 2025
-
 Discuss Everything About Bubble Gum Simulator Wiki09 abril 2025
Discuss Everything About Bubble Gum Simulator Wiki09 abril 2025 -
 This is my primary CAC, I named him after my username in game but his name is Jeans! : r/dbxv09 abril 2025
This is my primary CAC, I named him after my username in game but his name is Jeans! : r/dbxv09 abril 2025 -
Content Deleted ] Roblox Item - Rolimon's09 abril 2025
-
easy rbx|TikTok Search09 abril 2025
-
 Yamaha Music09 abril 2025
Yamaha Music09 abril 2025
você pode gostar
-
 LofZOdyssey - Anime Reviews: Anime Hajime Review: Ousama Game The Animation09 abril 2025
LofZOdyssey - Anime Reviews: Anime Hajime Review: Ousama Game The Animation09 abril 2025 -
 Genshin Impact To Release Version 3.4 On January 18th09 abril 2025
Genshin Impact To Release Version 3.4 On January 18th09 abril 2025 -
 Jogo de construir casas Black Friday Casas Bahia09 abril 2025
Jogo de construir casas Black Friday Casas Bahia09 abril 2025 -
 DIY Room Decor Ideas for the Master Bedroom - Domestically Speaking09 abril 2025
DIY Room Decor Ideas for the Master Bedroom - Domestically Speaking09 abril 2025 -
 Least Cash, Bloons Wiki09 abril 2025
Least Cash, Bloons Wiki09 abril 2025 -
 Triggered Kuros_PL Meme XD by KurosPL on DeviantArt09 abril 2025
Triggered Kuros_PL Meme XD by KurosPL on DeviantArt09 abril 2025 -
 Ai Takes the Cake in New Oshi no Ko Anime Collaboration - Crunchyroll News09 abril 2025
Ai Takes the Cake in New Oshi no Ko Anime Collaboration - Crunchyroll News09 abril 2025 -
 REICRIL CHAPAS ACRILICAS POLICARBONATO PETG COLA PARA PLASTICOS - COLAS PARA PLASTICOS09 abril 2025
REICRIL CHAPAS ACRILICAS POLICARBONATO PETG COLA PARA PLASTICOS - COLAS PARA PLASTICOS09 abril 2025 -
 Redfall Game Update 3 Release Notes09 abril 2025
Redfall Game Update 3 Release Notes09 abril 2025 -
 QUIZ DA LULUCA(LUÍZA)09 abril 2025
QUIZ DA LULUCA(LUÍZA)09 abril 2025



