Algorithms, Free Full-Text
Por um escritor misterioso
Last updated 01 abril 2025
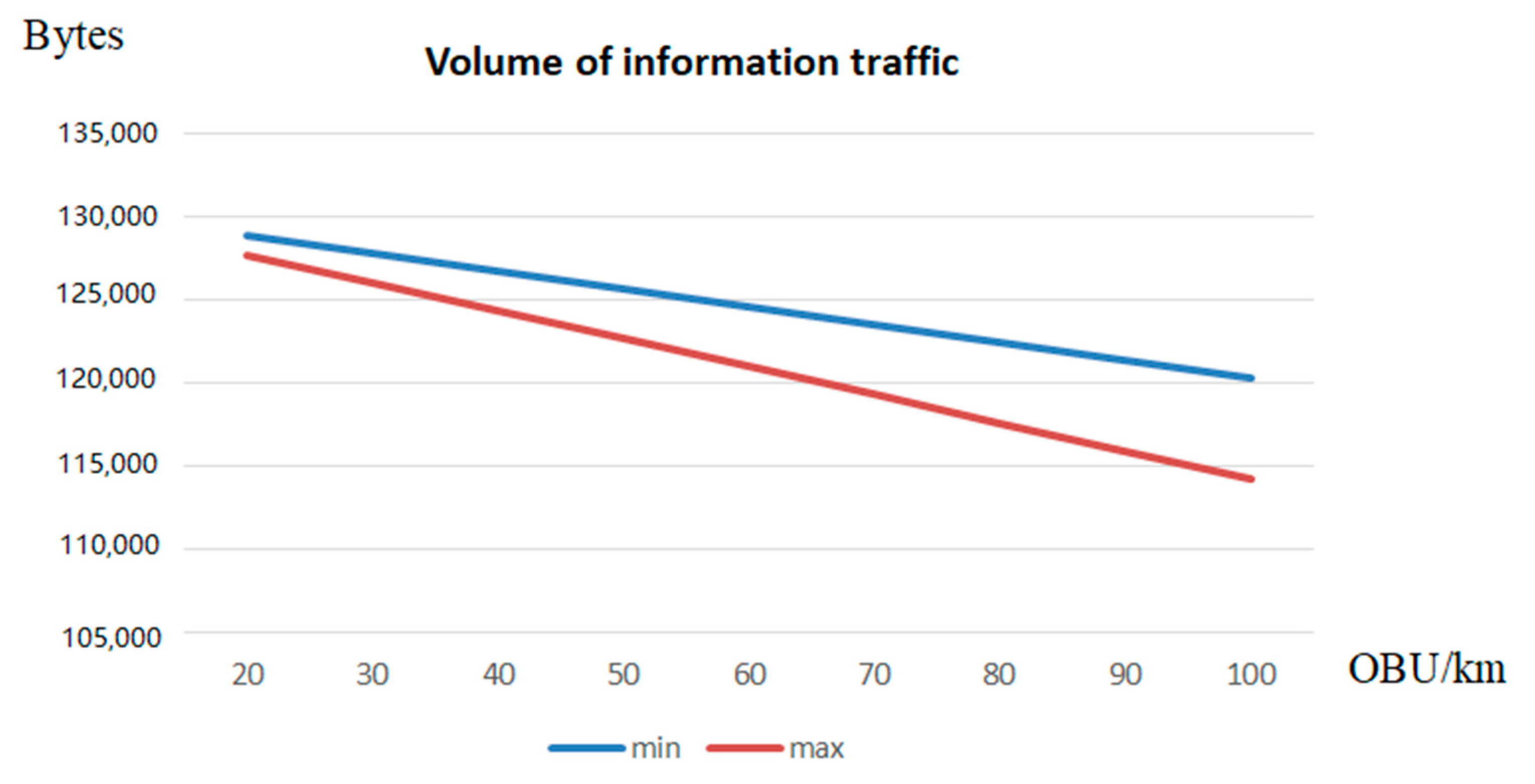
Authentication protocols are expanding their application scope in wireless information systems, among which are low-orbit satellite communication systems (LOSCS) for the OneWeb space Internet, automatic object identification systems using RFID, the Internet of Things, intelligent transportation systems (ITS), Vehicular Ad Hoc Network (VANET). This is due to the fact that authentication protocols effectively resist a number of attacks on wireless data transmission channels in these systems. The main disadvantage of most authentication protocols is the use of symmetric and asymmetric encryption systems to ensure high cryptographic strength. As a result, there is a problem in delivering keys to the sides of the prover and the verifier. At the same time, compromising of keys will lead to a decrease in the level of protection of the transmitted data. Zero-knowledge authentication protocols (ZKAP) are able to eliminate this disadvantage. However, most of these protocols use multiple rounds to authenticate the prover. Therefore, ZKAP, which has minimal time costs, is developed in the article. A scheme for adapting protocol parameters has been developed in this protocol to increase its efficiency. Reductions in the level of confidentiality allow us to reduce the time spent on the execution of the authentication protocol. This increases the volume of information traffic. At the same time, an increase in the confidentiality of the protocol entails an increase in the time needed for authentication of the prover, which reduces the volume of information traffic. The FPGA Artix-7 xc7a12ticsg325-1L was used to estimate the time spent implementing the adaptive ZKAP protocol. Testing was performed for 32- and 64-bit adaptive authentication protocols.
:max_bytes(150000):strip_icc()/algorithm-df9b57e8ea7c494b891da25987643fab.jpg)
What an Algorithm Is and Implications for Trading

SOLUTION: Social media algorithms affect our lives free download

Algorithms, 4th Edition by Robert Sedgewick and Kevin Wayne

Autonomous Unmanned Aerial/Ground Vehicles and their Applications

Comparative analysis of the BVTNet with baseline algorithms for

Beyond the Worst-Case Analysis of Algorithms
Free Algorithms Book

Centrum Wiskunde & Informatica: Local improvement algorithms for a

Algorithm - Wikipedia
Free Text Redaction - Delphix Masking 6.0.17
Recomendado para você
-
 Project New World Codes - XP and Money Boost (December 2023)01 abril 2025
Project New World Codes - XP and Money Boost (December 2023)01 abril 2025 -
CODE] HAZE PIECE - Roblox01 abril 2025
-
Elections in digital times: a guide for electoral practitioners01 abril 2025
-
 Agenda - City of Santa Monica01 abril 2025
Agenda - City of Santa Monica01 abril 2025 -
 Investigators Stop Work at Goudey Station Near Johnson City01 abril 2025
Investigators Stop Work at Goudey Station Near Johnson City01 abril 2025 -
 JPM, Free Full-Text01 abril 2025
JPM, Free Full-Text01 abril 2025 -
 Top 10 Trending Metaverse Projects of The Week - NFT News Pro01 abril 2025
Top 10 Trending Metaverse Projects of The Week - NFT News Pro01 abril 2025 -
 Slavery - Wikipedia01 abril 2025
Slavery - Wikipedia01 abril 2025 -
Combined Experimental and Mechanoelastic Modeling Studies on the Low-Spin Stabilized Mixed Crystals of 3D Oxalate-Based Coordination Materials01 abril 2025
-
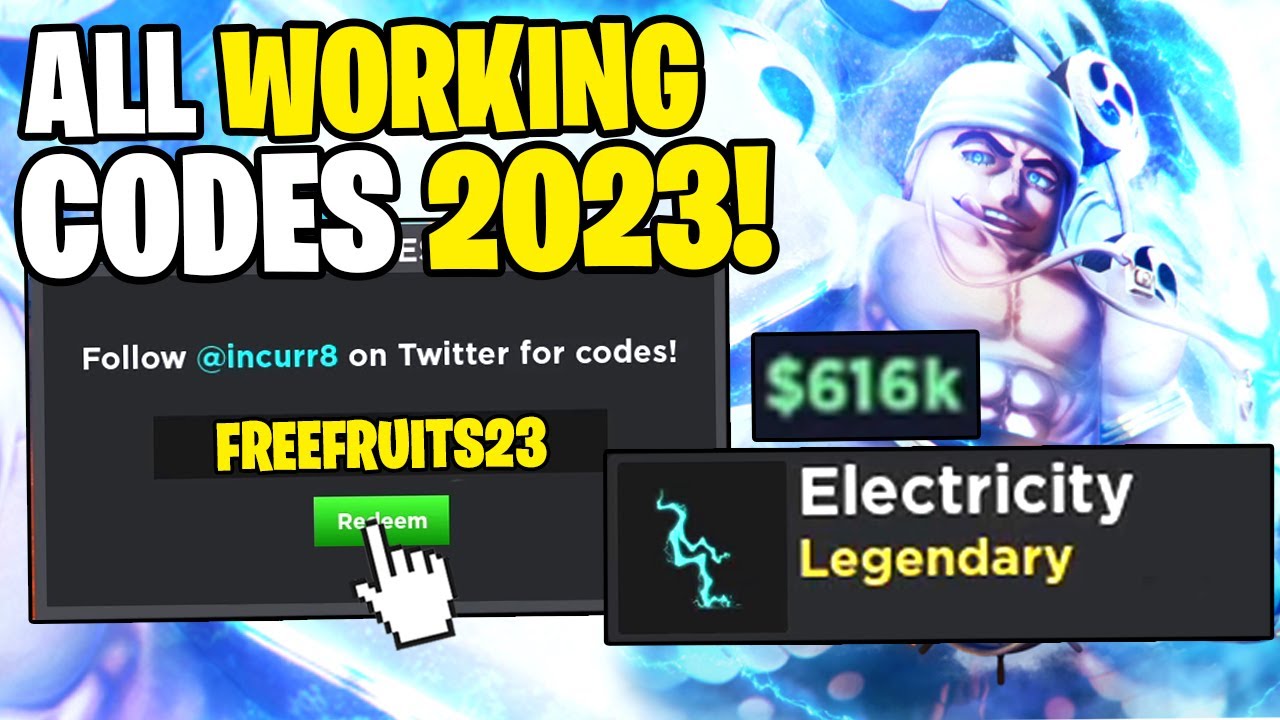 NEW* ALL WORKING CODES FOR PROJECT NEW WORLD IN 2023! ROBLOX PROJECT NEW WORLD CODES01 abril 2025
NEW* ALL WORKING CODES FOR PROJECT NEW WORLD IN 2023! ROBLOX PROJECT NEW WORLD CODES01 abril 2025
você pode gostar
-
 PPT - TGI047 - Leitura e Formação do Leitor PowerPoint Presentation, free download - ID:595209001 abril 2025
PPT - TGI047 - Leitura e Formação do Leitor PowerPoint Presentation, free download - ID:595209001 abril 2025 -
Hot Cloud Gaming01 abril 2025
-
 Tatuagem temp mod 38 - Minecraft01 abril 2025
Tatuagem temp mod 38 - Minecraft01 abril 2025 -
 CBF divulga tabela do Brasileiro Feminino A2; Veja os jogos do Vila Nova01 abril 2025
CBF divulga tabela do Brasileiro Feminino A2; Veja os jogos do Vila Nova01 abril 2025 -
 Review: Chainsaw Man – Cedar BluePrints Magazine01 abril 2025
Review: Chainsaw Man – Cedar BluePrints Magazine01 abril 2025 -
Sterling Superkings 100 Multipack Cigarettes - ASDA Groceries01 abril 2025
-
 Super Mario Party - Nintendo Switch 16 Dígitos Código Digital - PentaKill Store - Gift Card e Games01 abril 2025
Super Mario Party - Nintendo Switch 16 Dígitos Código Digital - PentaKill Store - Gift Card e Games01 abril 2025 -
 The Story Behind Beth Harmon's Red Hair in The Queen's Gambit01 abril 2025
The Story Behind Beth Harmon's Red Hair in The Queen's Gambit01 abril 2025 -
 Camiseta Oakley Mercado Livre 📦01 abril 2025
Camiseta Oakley Mercado Livre 📦01 abril 2025 -
仙王的日常生活第三季》第1集大小姐vs大小姐- video Dailymotion01 abril 2025
![CODE] HAZE PIECE - Roblox](https://tr.rbxcdn.com/f2b07ef514f1a9460746f6395a1fd9a2/768/432/Image/Png)



