Abusing Exceptions for Code Execution, Part 2
Por um escritor misterioso
Last updated 07 abril 2025

In this article, we'll explore how the concepts behind Exception Oriented Programming can be abused when exploiting stack overflow vulnerabilities on Windows.

What is an Integer Overflow Attack (with Examples)?

Hunting for Suspicious Windows Libraries for Execution and Defense

Abusing Windows Internals - Part Two
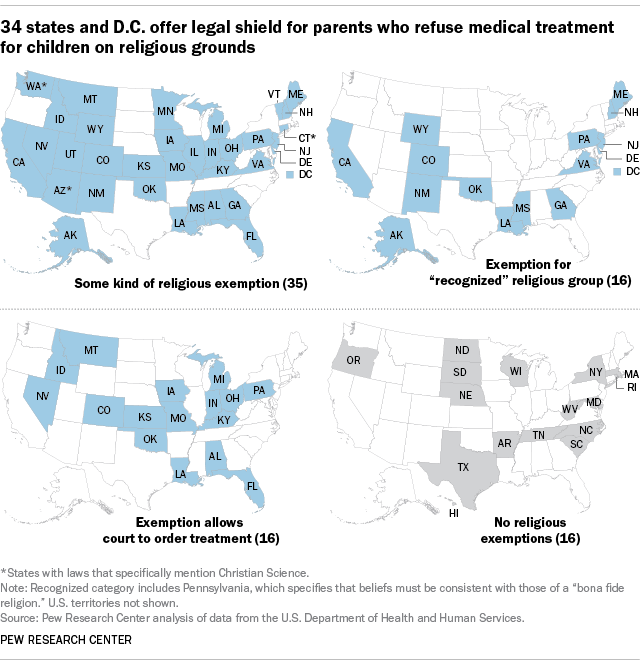
Most states' child abuse and neglect laws have religious

Secure Your AWS EC2 IMDS - Tenable Cloud Security

Hackers Exploit Windows Policy Loophole to Forge Kernel-Mode
Log4Shell Zero-Day Vulnerability - CVE-2021-44228

What is code injection?, Tutorial & examples

Changing Spring Boot Env Properties at Runtime
Recomendado para você
-
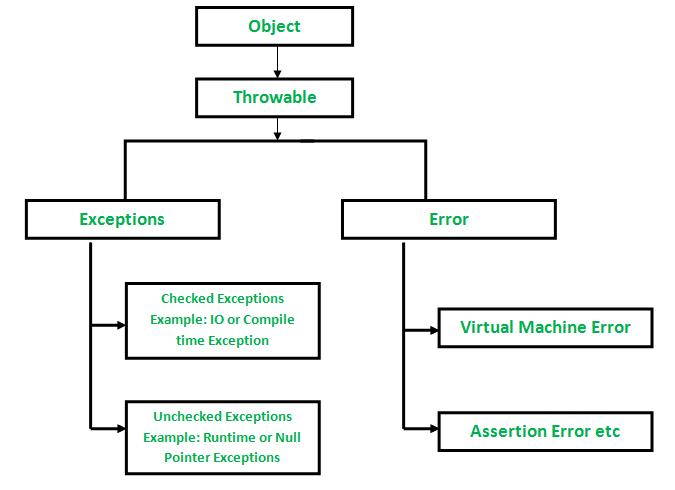 Checked vs Unchecked Exceptions in Java - GeeksforGeeks07 abril 2025
Checked vs Unchecked Exceptions in Java - GeeksforGeeks07 abril 2025 -
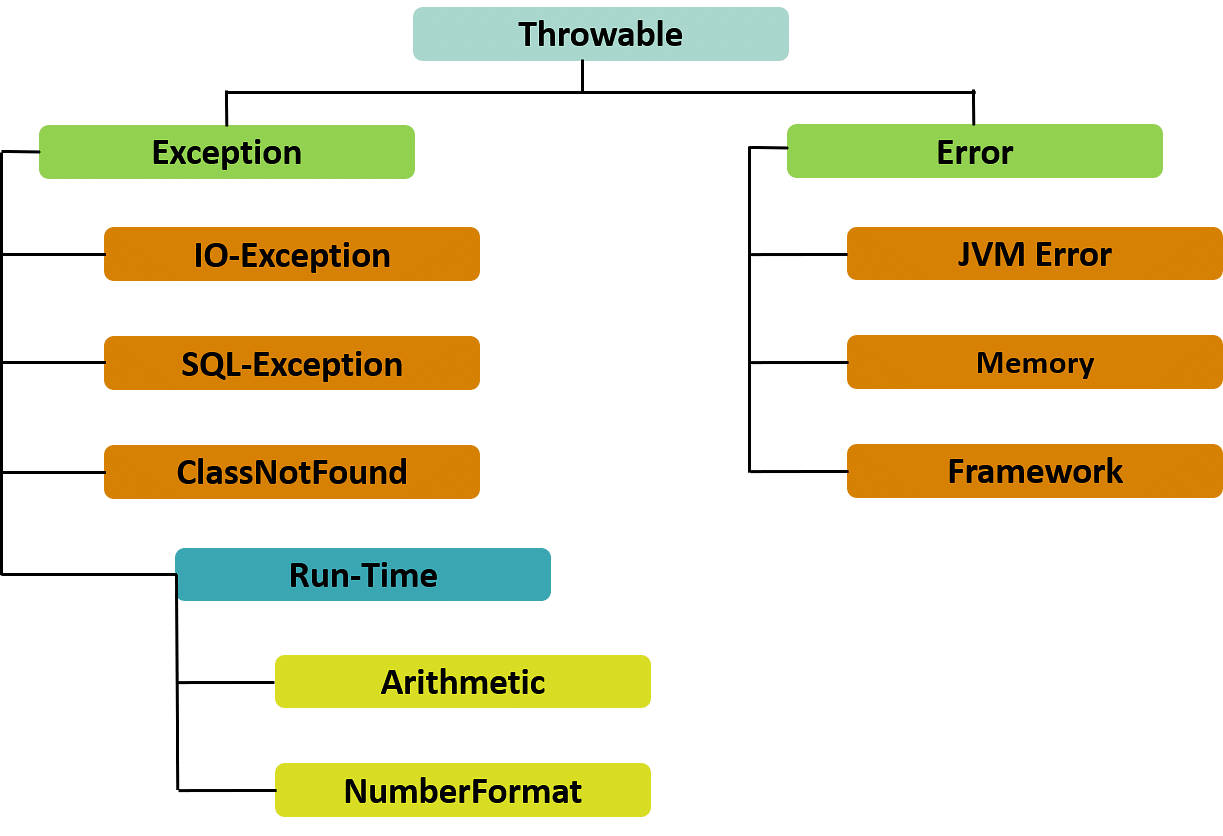 What is Exception Handling in Java?07 abril 2025
What is Exception Handling in Java?07 abril 2025 -
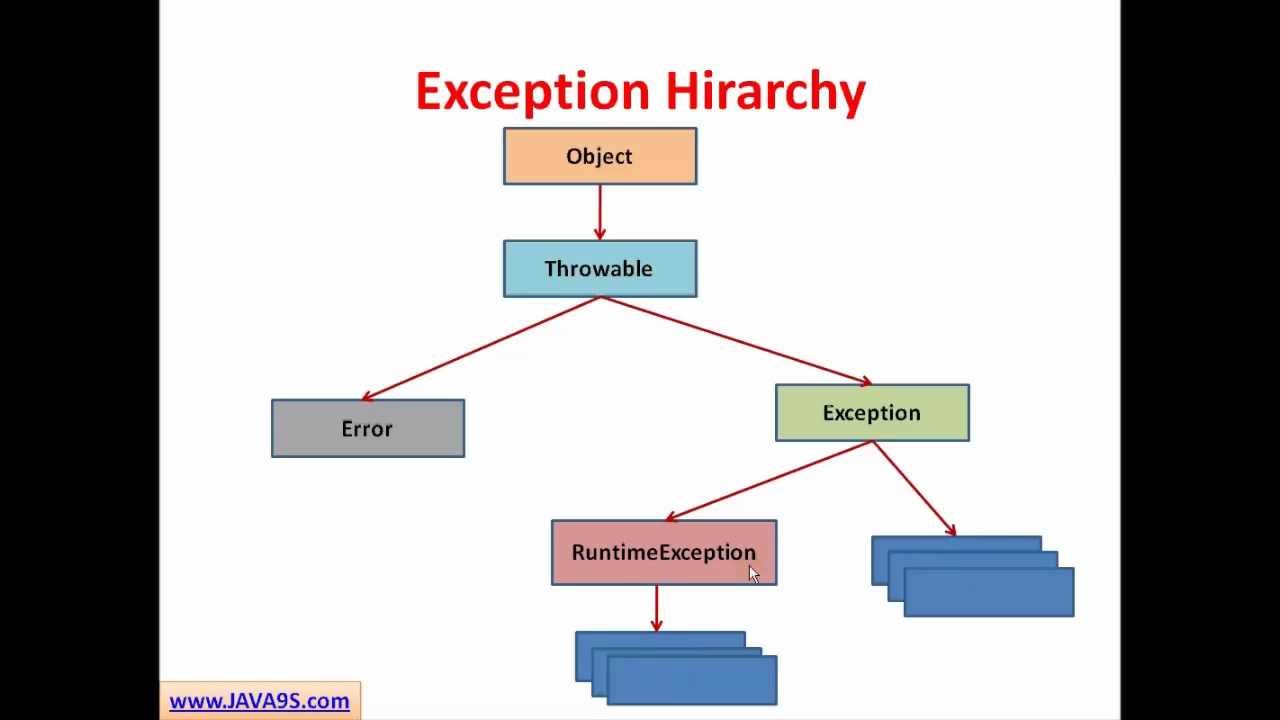 Java Tutorial # 14 Exception Handling in Java - Checked and Unchecked Exceptions07 abril 2025
Java Tutorial # 14 Exception Handling in Java - Checked and Unchecked Exceptions07 abril 2025 -
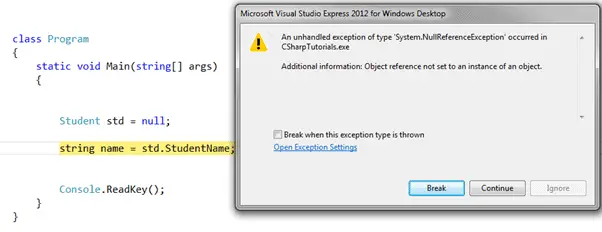 Built-in Exception Classes in C#07 abril 2025
Built-in Exception Classes in C#07 abril 2025 -
Exceptions are meant to be exceptional - DEV Community07 abril 2025
-
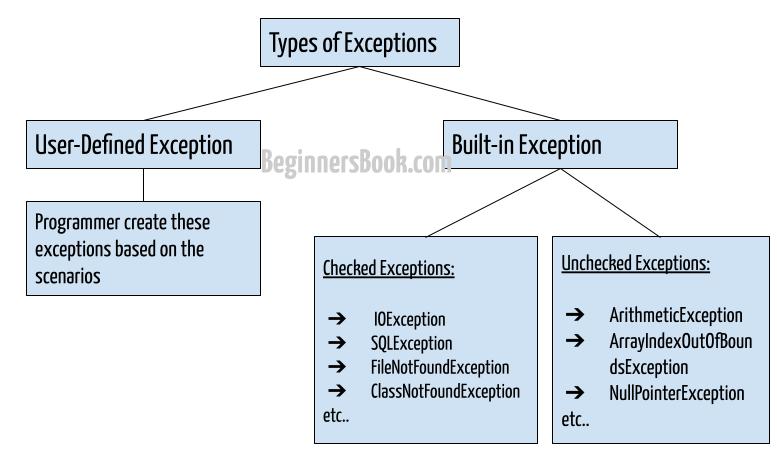 Exception handling in Java with examples07 abril 2025
Exception handling in Java with examples07 abril 2025 -
 Abusing Exceptions for Code Execution, Part 107 abril 2025
Abusing Exceptions for Code Execution, Part 107 abril 2025 -
 Java Exception Handling Cheat Sheet07 abril 2025
Java Exception Handling Cheat Sheet07 abril 2025 -
 Invoice Exceptions: Where they come from and how to prevent them07 abril 2025
Invoice Exceptions: Where they come from and how to prevent them07 abril 2025 -
 No exceptions rubber stamp Royalty Free Vector Image07 abril 2025
No exceptions rubber stamp Royalty Free Vector Image07 abril 2025
você pode gostar
-
 Star Wars: Battlefront II Download (2005 Arcade action Game)07 abril 2025
Star Wars: Battlefront II Download (2005 Arcade action Game)07 abril 2025 -
 Gumball Watterson's Real House From The Amazing World of Gumball07 abril 2025
Gumball Watterson's Real House From The Amazing World of Gumball07 abril 2025 -
 Ícone de sinal do teste. Perguntas e respostas jogo . imagem07 abril 2025
Ícone de sinal do teste. Perguntas e respostas jogo . imagem07 abril 2025 -
 160+ y2k roblox outfits w/ CODES & LINKS ♡07 abril 2025
160+ y2k roblox outfits w/ CODES & LINKS ♡07 abril 2025 -
 Ben Foster07 abril 2025
Ben Foster07 abril 2025 -
 Anime Girl Id Roblox, HD Png Download - 992x900(#4593957) - PngFind07 abril 2025
Anime Girl Id Roblox, HD Png Download - 992x900(#4593957) - PngFind07 abril 2025 -
 Snake Game Addition Kit 2 - ETC Montessori Online07 abril 2025
Snake Game Addition Kit 2 - ETC Montessori Online07 abril 2025 -
 Star Wars: Andor Disney+ Show Reveals New Droid Character (Photos)07 abril 2025
Star Wars: Andor Disney+ Show Reveals New Droid Character (Photos)07 abril 2025 -
 The Dawn of the Witch - Anime ganha imagem e confirmação de dubladores - AnimeNew07 abril 2025
The Dawn of the Witch - Anime ganha imagem e confirmação de dubladores - AnimeNew07 abril 2025 -
 Pikachu - Free gaming icons07 abril 2025
Pikachu - Free gaming icons07 abril 2025
