Trend Micro Research on X: Scenario 2: If the user is not logged
Por um escritor misterioso
Last updated 10 abril 2025
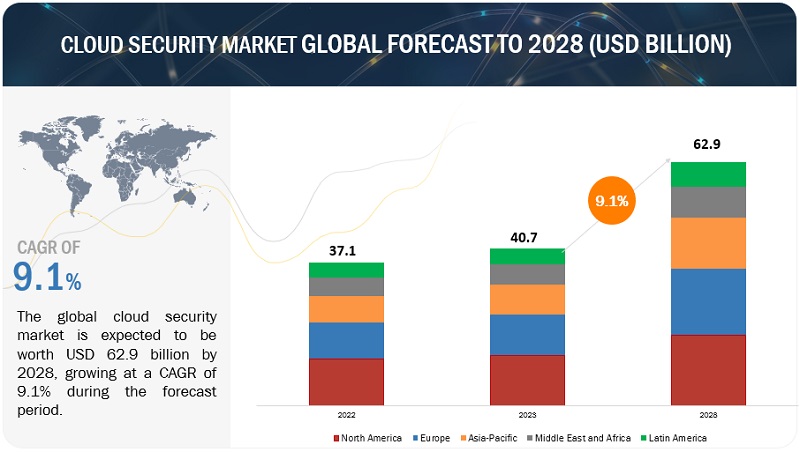
Cloud Security Market Size & Forecast, [Latest]

RADIUS Server Authentication: Explained

The Myth of Air Purifier in Mitigating the Transmission Risk of SARS-CoV-2 Virus - Aerosol and Air Quality Research
Verification Unsuccessful error from Trend Micro Antivirus
Evaluate Microsoft Exchange Online modules - Cloud App Security
1 in Cloud Security & Endpoint Cybersecurity
How to generate various logs in Trend Micro for Windows
Set up Authentication Agent Self-Signed Certificate with SAN - TMWS

Trend Micro Antivirus+ Security Review
Collecting debug logs - Portable Security 3.0
Collecting debug logs - Portable Security 3.0
General Troubleshooting Methods - Netskope Knowledge Portal
How to add items in Trend Micro Exception List on Windows
Recomendado para você
-
 How to Login to Your Facebook Business Profile from Anywhere10 abril 2025
How to Login to Your Facebook Business Profile from Anywhere10 abril 2025 -
 Facebook Login Home Page Screen Editorial Stock Photo10 abril 2025
Facebook Login Home Page Screen Editorial Stock Photo10 abril 2025 -
 Should I Log In With Facebook? - Ask Leo!10 abril 2025
Should I Log In With Facebook? - Ask Leo!10 abril 2025 -
 Configure Facebook Login on Your Website & Mobile App in 202010 abril 2025
Configure Facebook Login on Your Website & Mobile App in 202010 abril 2025 -
 Facebook Screenshot, screenshot of facebook login page on m…, Neeraj Kumar10 abril 2025
Facebook Screenshot, screenshot of facebook login page on m…, Neeraj Kumar10 abril 2025 -
 ThrowbackTechnology: Facebook's original login page - Pixafy : Pixafy10 abril 2025
ThrowbackTechnology: Facebook's original login page - Pixafy : Pixafy10 abril 2025 -
 Facebook Login Page Stock Photos - 863 Images10 abril 2025
Facebook Login Page Stock Photos - 863 Images10 abril 2025 -
 SignUp with Facebook using VueJS. Sign-in / Sign-up with Facebook10 abril 2025
SignUp with Facebook using VueJS. Sign-in / Sign-up with Facebook10 abril 2025 -
Removing clients' pages from FB profile - Social Media Pulse10 abril 2025
-
 Facebook Login Sign Up New Account, Login FB Account Now10 abril 2025
Facebook Login Sign Up New Account, Login FB Account Now10 abril 2025
você pode gostar
-
 Peaky Blinders' Season 6 Finale: Tommy's Ending Explained10 abril 2025
Peaky Blinders' Season 6 Finale: Tommy's Ending Explained10 abril 2025 -
 Ban Midou (GetBackers) - Clubs10 abril 2025
Ban Midou (GetBackers) - Clubs10 abril 2025 -
Romance Anime Quiz - Forums10 abril 2025
-
 Pure Sonic Advance Vibes by dupreedraws on Newgrounds10 abril 2025
Pure Sonic Advance Vibes by dupreedraws on Newgrounds10 abril 2025 -
 Elden Ring Let Me Solo Her Build: Level & Spirit Summon - Top-mmo10 abril 2025
Elden Ring Let Me Solo Her Build: Level & Spirit Summon - Top-mmo10 abril 2025 -
 Pin em Diseños de dibujo10 abril 2025
Pin em Diseños de dibujo10 abril 2025 -
prompthunt: anime cyberpunk 2077 anime series screenshot, perfect faces, fine details10 abril 2025
-
 Zoo Tycoon Dino Digs Jurassic Zoo Part 210 abril 2025
Zoo Tycoon Dino Digs Jurassic Zoo Part 210 abril 2025 -
 Poker World: Offline Poker - Free Play & No Download10 abril 2025
Poker World: Offline Poker - Free Play & No Download10 abril 2025 -
Magic Bubble Shooter: Classic Bubbles Arcade for Nintendo Switch10 abril 2025

